ExecuteMalware
@executemalware
#malware hunter & analyst.
Opinions are my own.
ID:743883460587167744
17-06-2016 19:10:12
15,6K Tweets
25,9K Followers
191 Following






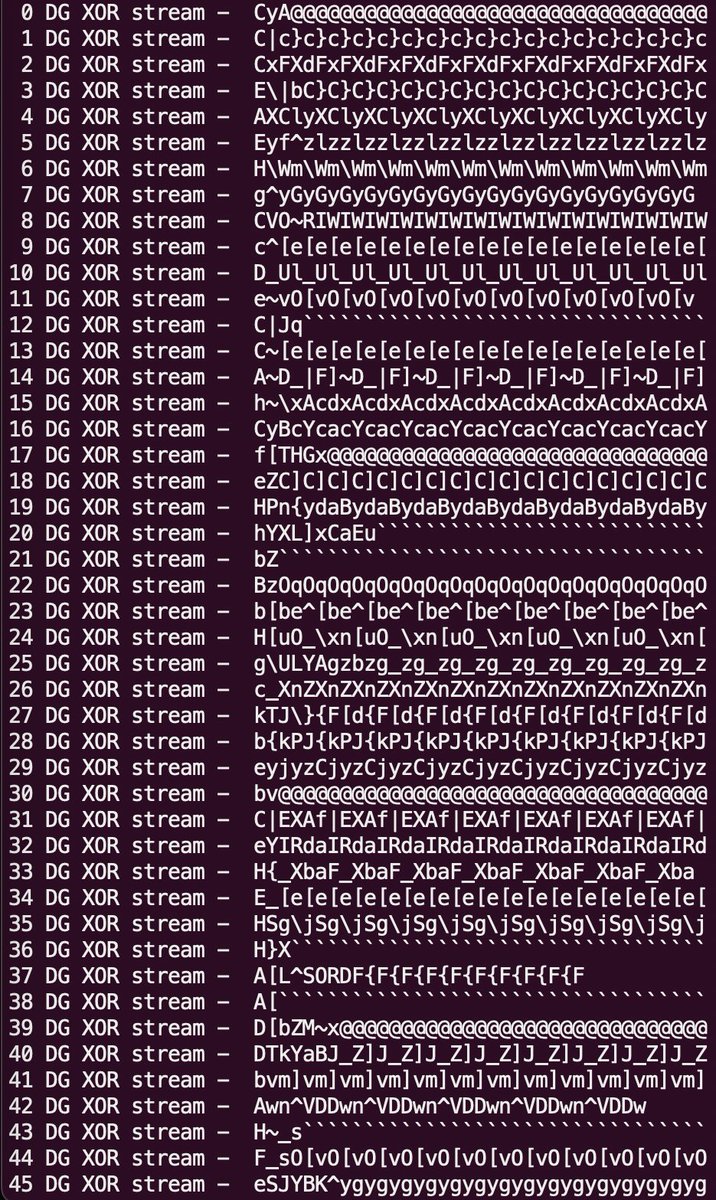
Another great showcase of using urlscan.io.
You can use Options to specify the HTTP referer and user agent. Let's apply this to the threat case that DaveTheResearcher found today. We were able to extract the main culprit (chatgpt-app.]cloud) from the injected script that is…
![RussianPanda 🐼 🇺🇦 (@RussianPanda9xx) on Twitter photo 2024-05-03 20:51:17 Another great showcase of using @urlscanio. You can use Options to specify the HTTP referer and user agent. Let's apply this to the threat case that @DaveLikesMalwre found today. We were able to extract the main culprit (chatgpt-app.]cloud) from the injected script that is… Another great showcase of using @urlscanio. You can use Options to specify the HTTP referer and user agent. Let's apply this to the threat case that @DaveLikesMalwre found today. We were able to extract the main culprit (chatgpt-app.]cloud) from the injected script that is…](https://pbs.twimg.com/media/GMrpKm5WsAEIUQZ.jpg)


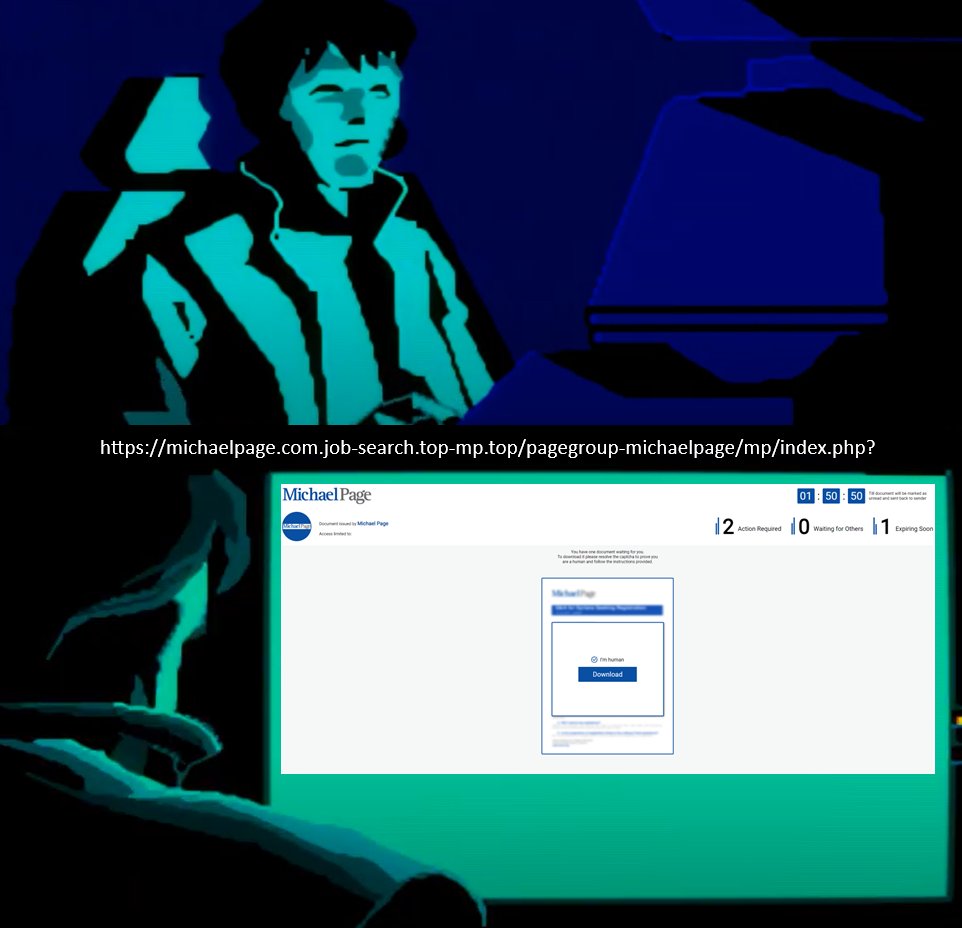
The infamous #Rhadamanthys Stealer has been banned from XSS forum after failing to provide protection to CIS countries people.
Rhadamanthys was used against Russian military infrastructure (habr.com/en/companies/f…), also by some fellow traffers guys...
🫂🫡
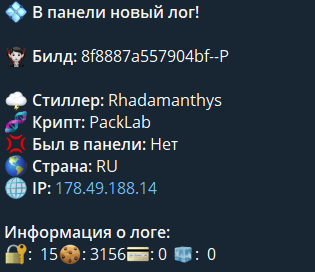

vx-underground Turns out the LUA wasn't part of RedLine but a newish 'SmartLoader' malware loader.
research.openanalysis.net/github/lua/202…



Wanna join the team?
proofpoint.wd5.myworkdayjobs.com/en-US/Proofpoi…
Day to day:
Write intrusion detection rules for the Snort and Suricata platforms
Answer support questions about rule guidance and false positives
Work with the open source community to maintain and optimize the ETOpen ruleset…

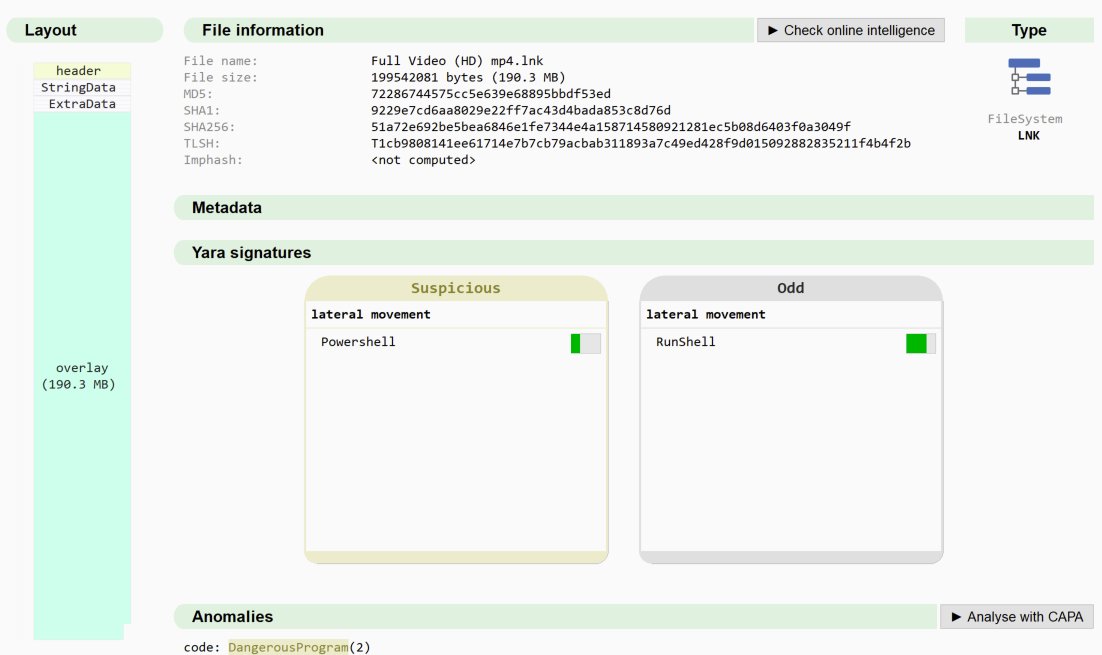
New Latrodectus malware attacks use Microsoft, Cloudflare themes - Lawrence Abrams
bleepingcomputer.com/news/security/…
bleepingcomputer.com/news/security/…





#Latrodectus - .pdf > url > .js > .msi > .dll
wscript.exe Document.js
msiexec.exe /V
MSIBE26.tmp rundll32.exe C:\Users\Admin\AppData\Local\glosar\beta.dll, homq
rundll32.exe C:\Users\Admin\AppData\Roaming\Custom_update\Update.dll, homq
(1/3) 👇
IOC's
github.com/pr0xylife/Latr…