Gyver
@dr4s1l
ID: 3009285878
03-02-2015 14:02:38
4,4K Tweet
423 Followers
1,1K Following




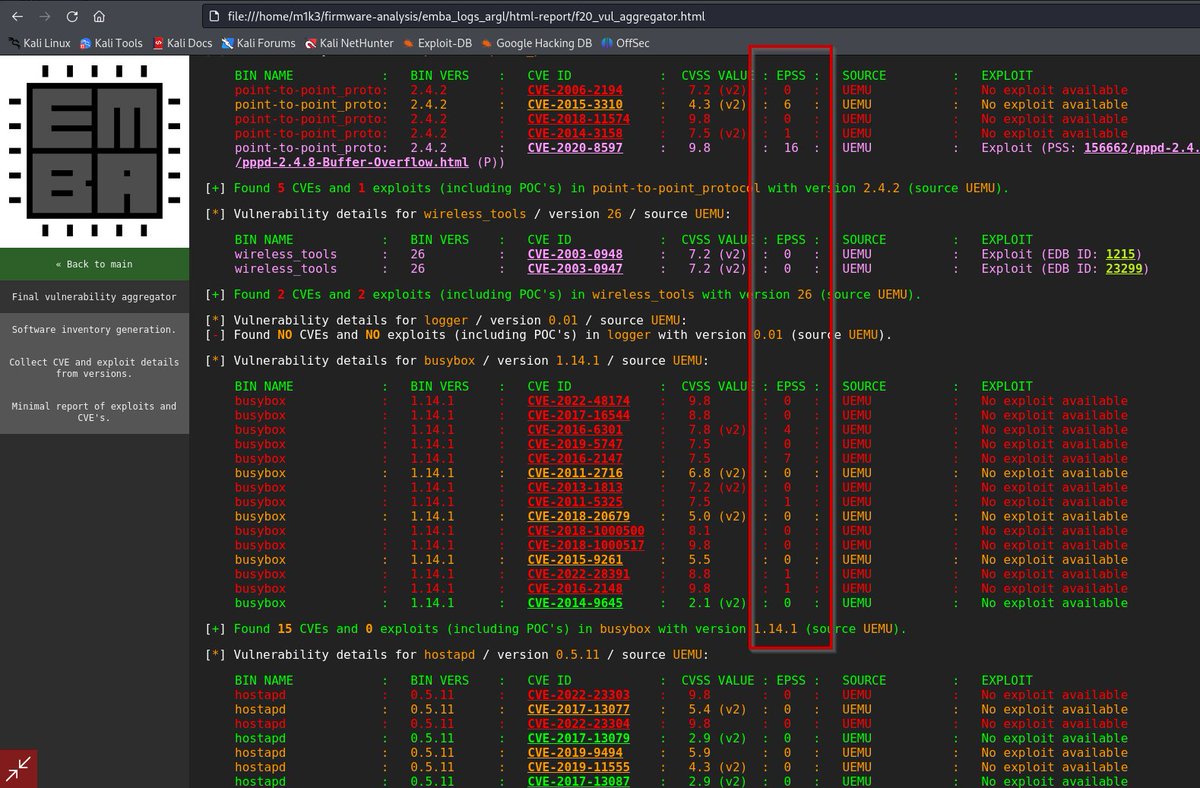
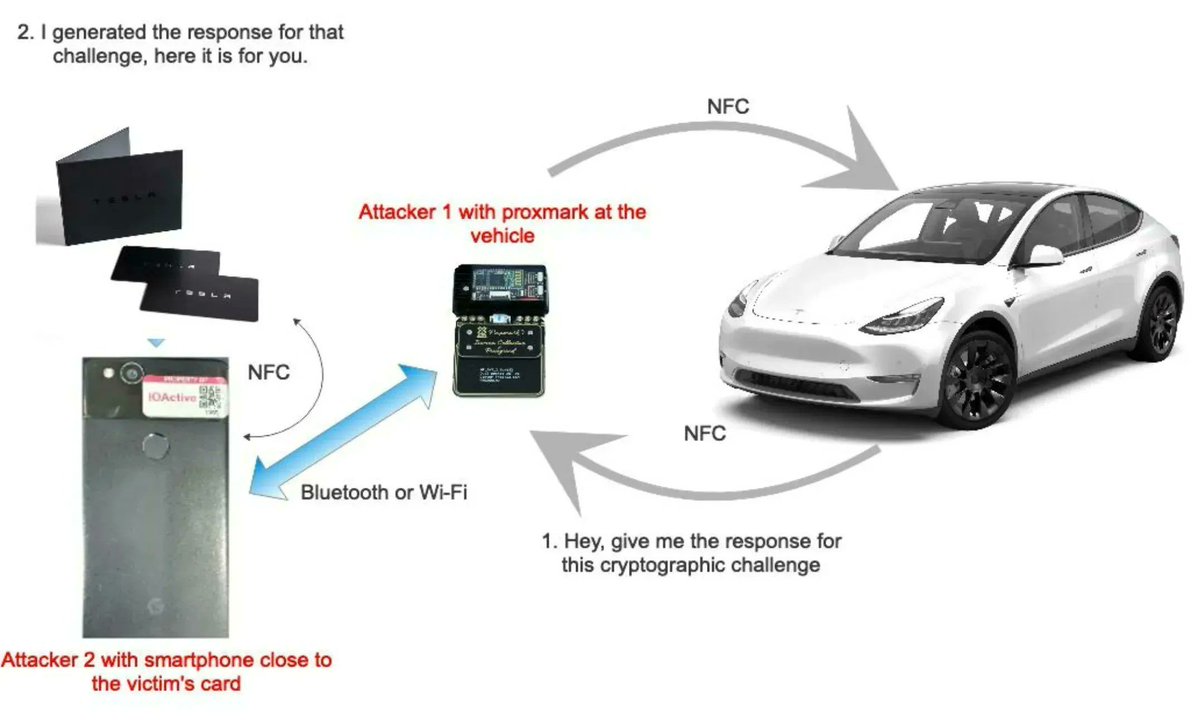
Attacking cars wireless exposed communication (Tesla Model Y, NFC and Proxmark) Interesting white paper (2022) by Josep Pi Rodriguez (IOActive, Inc) White paper link: act-on.ioactive.com/acton/attachme… #automotive #cybersecurity





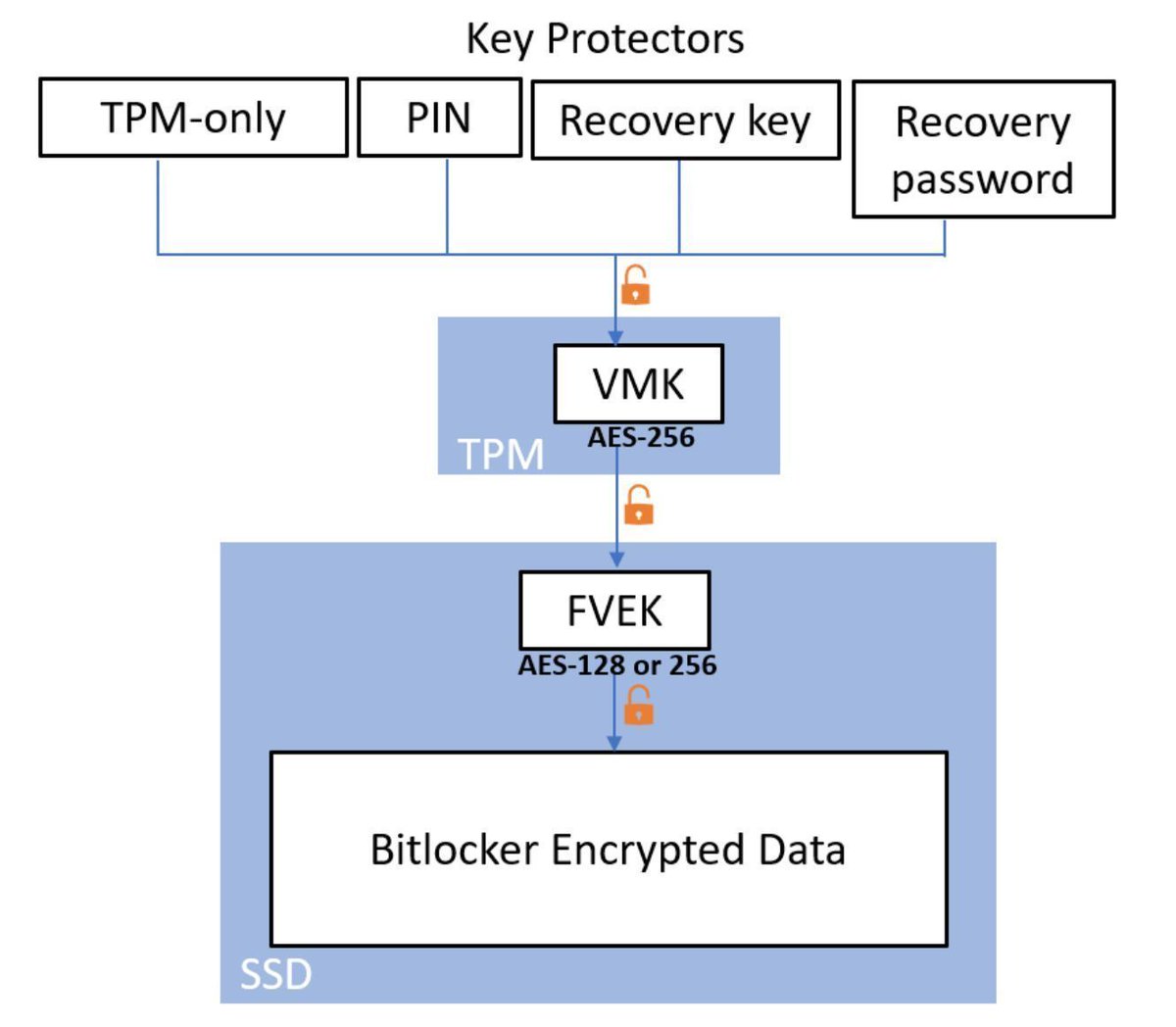
Total Identity Compromise: DART lessons on securing Active Directory, by Matt Zorich techcommunity.microsoft.com/t5/microsoft-s…



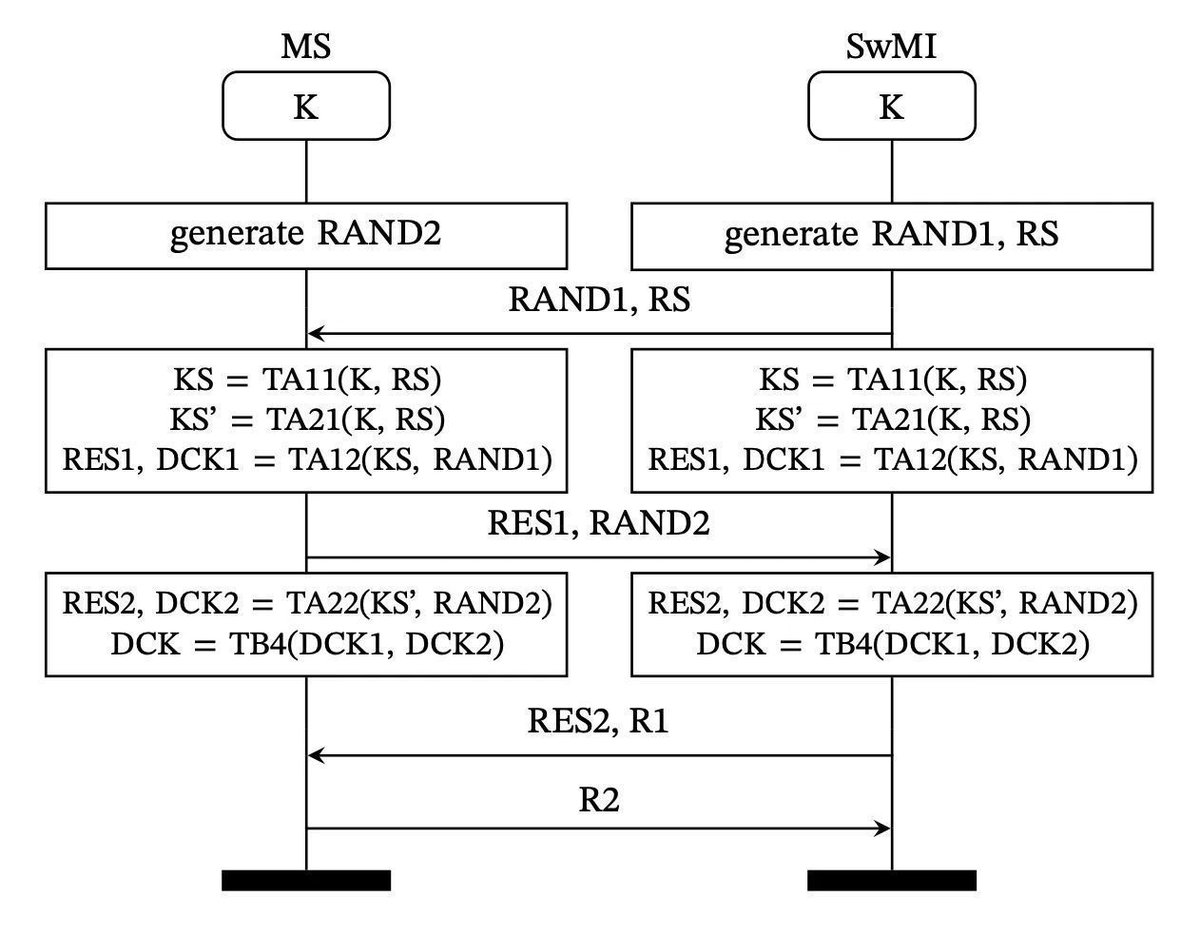
After two years of hard work with Damien Cauquil (@[email protected]) , we are proud to release for DEFCON32 the first public version of WHAD, a whole new ecosystem of opensource libs, tools & firmwares for wireless security ! The main repo is here: github.com/whad-team/whad… . And now, demo time ! [1/n]



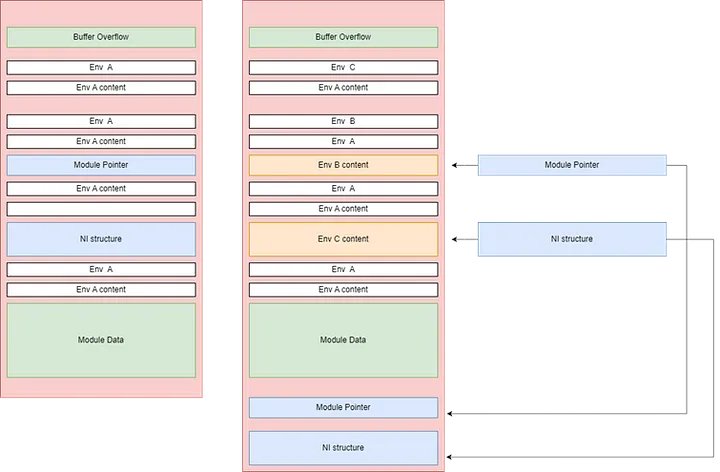
A repo for learning various heap exploitation techniques by Shellphish github.com/shellphish/how…