d4d
@d4d89704243
Zakhar Fedotkin
All thought are mine and mine alone
ID: 1151719984910995457
18-07-2019 05:06:57
116 Tweet
1,1K Followers
74 Following


Great job Chris Ratcliff! The photos are absolutely amazing!

Thanks PortSwigger and Bug Bounty Village for this awesome event — and also to my DEVCORE buddies for standing on stage to collect the trophy for me! A little follow-up article on this research is coming soon... stay tuned! 🤘






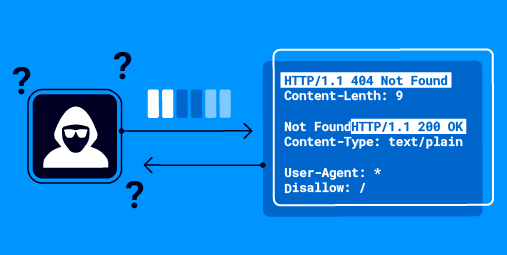
HTTP Request Smuggler v3.0.1 is now live! This fixes a false positive in the CL.0 scan caused by pipelining - thanks to sw33tLie for the report. Note that the new parser discrepancy scan still has superior accuracy. For more info on pipelining check out portswigger.net/research/how-t…







Can’t believe mentioning techniques still work - you’ve got to see this talk by Gareth Heyes \u2028