Focus on Linux/Kubernetes Attack/Detection/Forensics/Incident Response/Threat Hunting. Active Defense. PurpleLabs Cyber Range. Learning hard every single day.
ID: 335283366
https://edu.defensive-security.com 14-07-2011 13:00:06
1,1K Tweet
2,2K Followers
1,1K Following





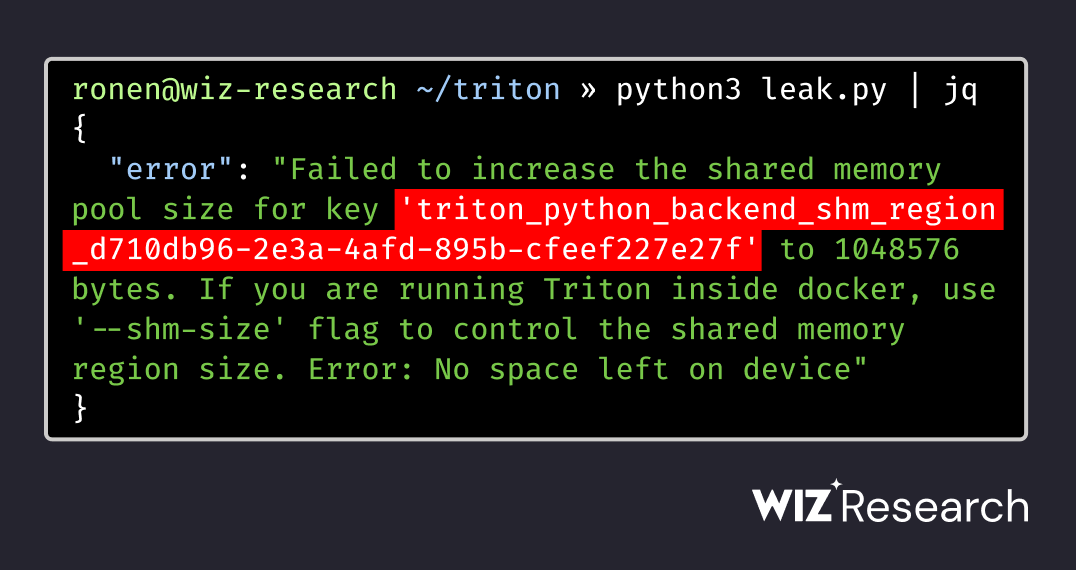
We (+Nir Ohfeld) found a critical vulnerability chain in NVIDIA's Triton Inference Server (CVE-2025-23319) that can lead to full Remote Code Execution (RCE). An unauthenticated attacker can remotely take over the server, a cornerstone of many AI/ML production environments. 🧵






We engineered an attack against GitHub Copilot to add a hidden backdoor via a malicious GitHub issue. See if you would’ve fallen for it: blog.trailofbits.com/2025/08/06/pro…



Exploiting All Google kernelCTF Instances And Debian 12 With A 0-Day For $82k Article by Crusaders of Rust about exploiting a UAF in the network packet scheduler. Researchers manipulated red-black trees to achieve a page-level UAF and escalate privileges. syst3mfailure.io/rbtree-family-…





