Ch. Bertrand V-o
@chbertrandvo
PostDoc @UCLouvain_be cybersecurity and machine learning 🤖 CTF player
ID: 2596644169
30-06-2014 16:51:14
42 Tweet
34 Followers
250 Following


La montée du nationalisme, de l'autoritarisme et de la haine ne semble pas être un accident circonstanciel limité à un pays. Selon les rapports Varieties of Democracy Institute auquel 3000+ chercheurs contribuent, il s'agit d'une tendance alarmante à l'échelle planétaire. v-dem.net/democracy_repo…






Systems for automatic paper-reviewer assignments (e.g., TPMS - mila.quebec/en/publication…) are used during the reviewing process of conferences such as ICML Conference. In arxiv.org/abs/2303.14443, we explore how authors might try to game these systems. We propose an attack that adapts...
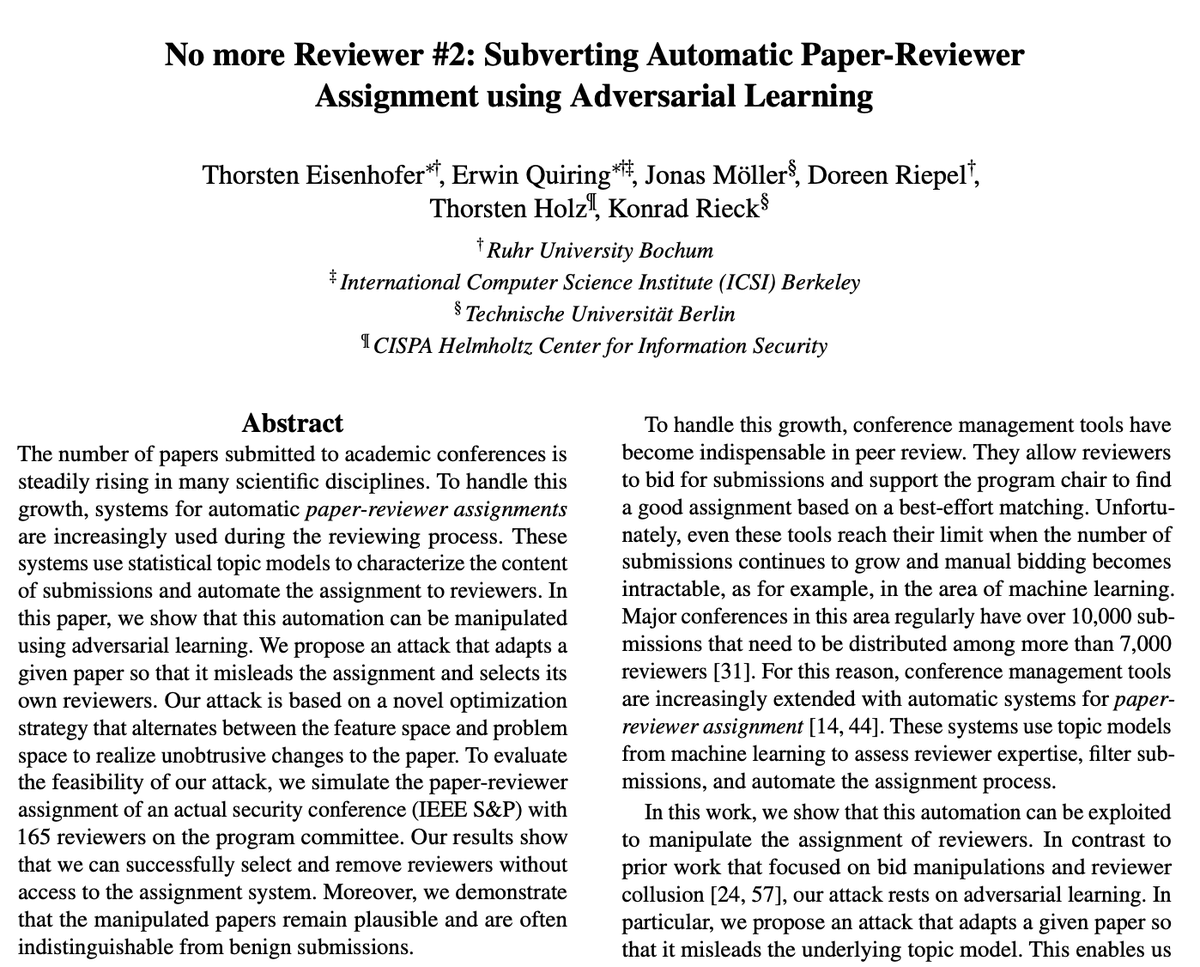



Get rid of bad reviewers? 🤔 Today, Thorsten Eisenhofer presents our work USENIX Security on misleading the automatic assignment of reviewers at large conferences (e.g. #CVPR or #NeurIPS). Our attack generates adversarial papers that select their own reviewers. BIFOLD CASA - Cluster of Excellence for Cyber Security 1/5