Chackal (Esdras DAGO)
@chackal__
"Vulnerability researcher" doing Bug Bounty on free time (yeswehack.com/hunters/chackal) Also doing some Reverse on many targets but find no vuln 😒
ID: 969762059226316800
https://medium.com/@chackal 03-03-2018 02:31:06
2,2K Tweet
1,1K Followers
875 Following


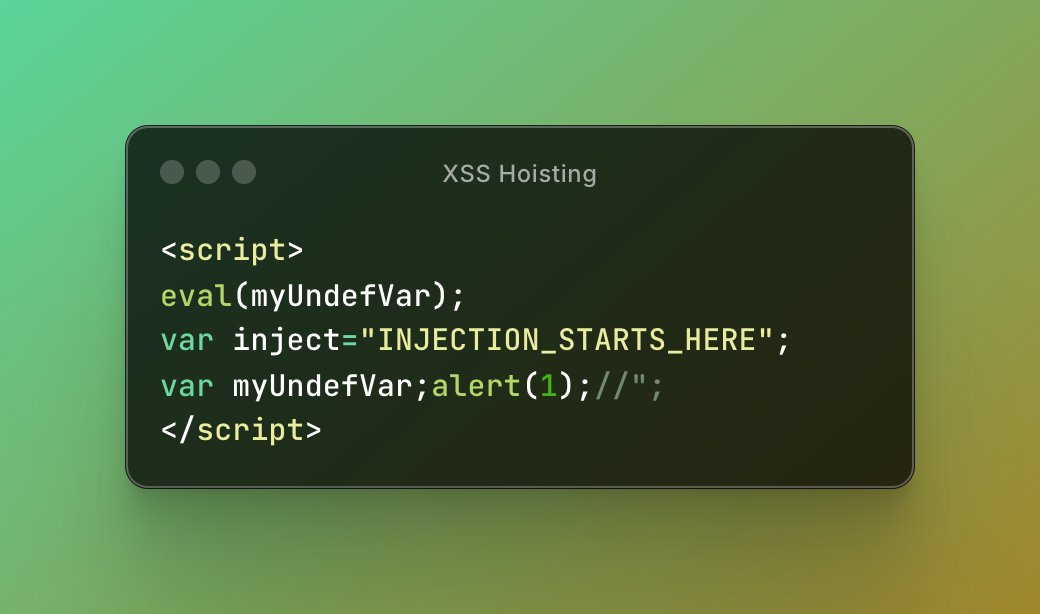
There is only one atomic building blocks: I call it Context Confusion! which I believe LiveOverflow 🔴 referees as Injection in his tweet. Single data becomes part of the another data. It’is still “data” for you but the moment that data switched the context, for instance sent


You can watch the recording of today's Off By One Security stream with James Kettle here: youtube.com/live/B7p8dIB7b…







Please join me on the next Off By One Security stream with guest Eugene Lim (spaceraccoon | Eugene Lim ) on 4-Sept at 6PM PT for a session on "0-day Hunting Strategy!" This will be a great session for those interested in vulnerability research! Note the time at 6PM PT youtube.com/watch?v=dMt2qy…




Synacktiv Volker bsecure.fr Orange Cyberdefense France Pierre Milioni 📢 #GreHack25 program release! We're kicking off this weekend with a bang by announcing our guest speaker for this edition 👀 👤 Gynvael Coldwind from HexArcana ➡️ CTF in a box ? The weirdest NETGEAR network switch 2021 exploit chain See you tomorrow for a next talk 🔥

Anotha week, another VR newsletter 🏴☠️📰 NCC Group Research & Technology (McCaulay, Alex Plaskett) pop a Tesla TCU unit kCTF 1-day breakdowns from Faith 🇧🇩🇦🇺 & Pumpkin 🎃 Jann Horn - [email protected] talks potential remote ASLR leaks + Jobs and MORE 👇 blog.exploits.club/exploits-club-…



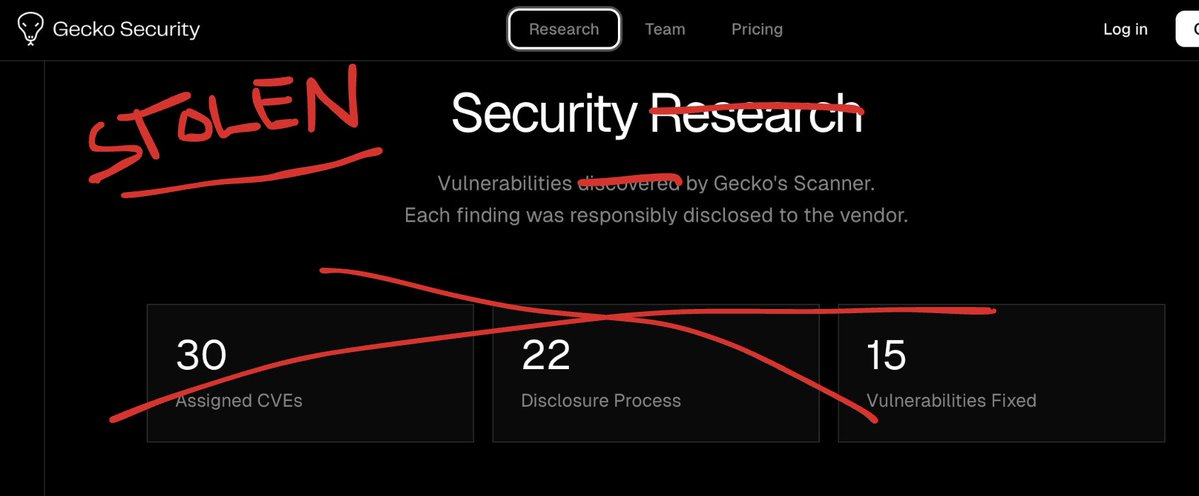
💣 We caught Y Combinator–backed Gecko Security stealing two of our CVEs, one on ollama , one on Gradio. They copied our PoCs, claimed CVE IDs, and even back-dated their blog posts. Here’s the full story 👇


PoV: you wakeup and go run a pwn2own exploit Trend Zero Day Initiative