c0rdis
@c0rdis

.Nimrod Kor's allthetalksconf recording is up! 🥳 Check it out to see the unveiling of AirIAM, our newest open-source project that migrates existing AWS IAM to least-privilege IAM Terraform. youtu.be/nFD0e9BNQRg




I am just watching a great presentation about security & #WardleyMapping by Mario Platt. My notes are here, feel free to add notion.so/kdaniel/Evolut…





Without formal access, a college kid got hold of OpenAI's GPT-3 and created a fake, AI-generated blog under a fake name. Within hours, his first post reached #1 on Hacker News Bot. A case study in how people could (ab)use the model in the future. technologyreview.com/2020/08/14/100…










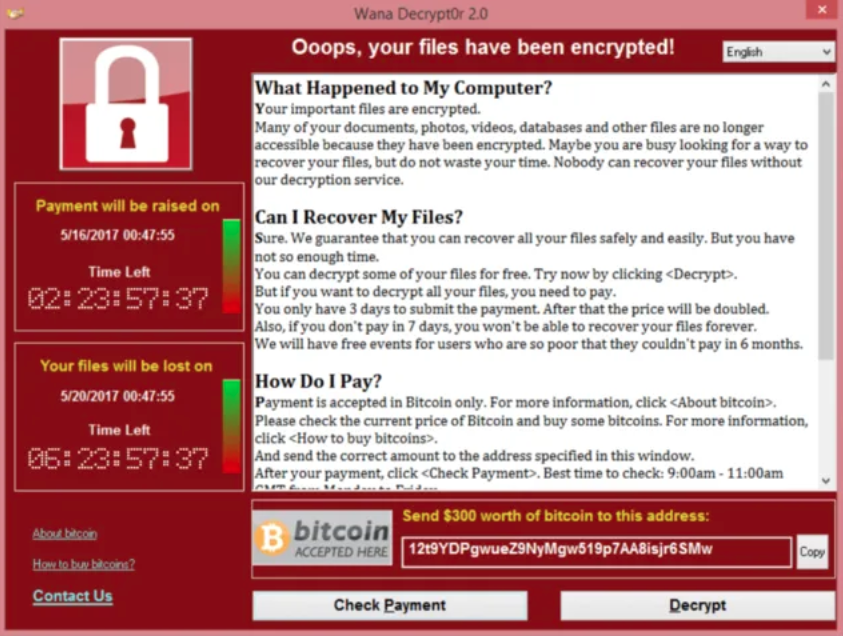
#GhostSec claims to have conducted the first ever #ransomwwre attack against an RTU - remote terminal unit used in ICS environments. Allan “Ransomware Sommelier🍷” Liska Robert M. Lee #cybersecurity #infosecurity #infosec #cyber