Austin Larsen
@austinlarsen_
Principal Threat Analyst - Google Threat Intelligence Group - Opinions attributable to me
ID: 465195359
16-01-2012 02:34:44
518 Tweet
764 Followers
967 Following



Update 6: We’ve been working with Mandiant (part of Google Cloud) to perform a comprehensive investigation of the incident. Their deep expertise in cybersecurity and Google Cloud infrastructure makes them the ideal partner as we work to protect performance and security for our traders.









This is an interesting case study because it concretely shows that you have to go further than allowlisting known/trusted executables, they also need runtime memory integrity protection/guarantees: cloud.google.com/blog/topics/th… Ideally, page-level integrity like iOS in your vm impl.


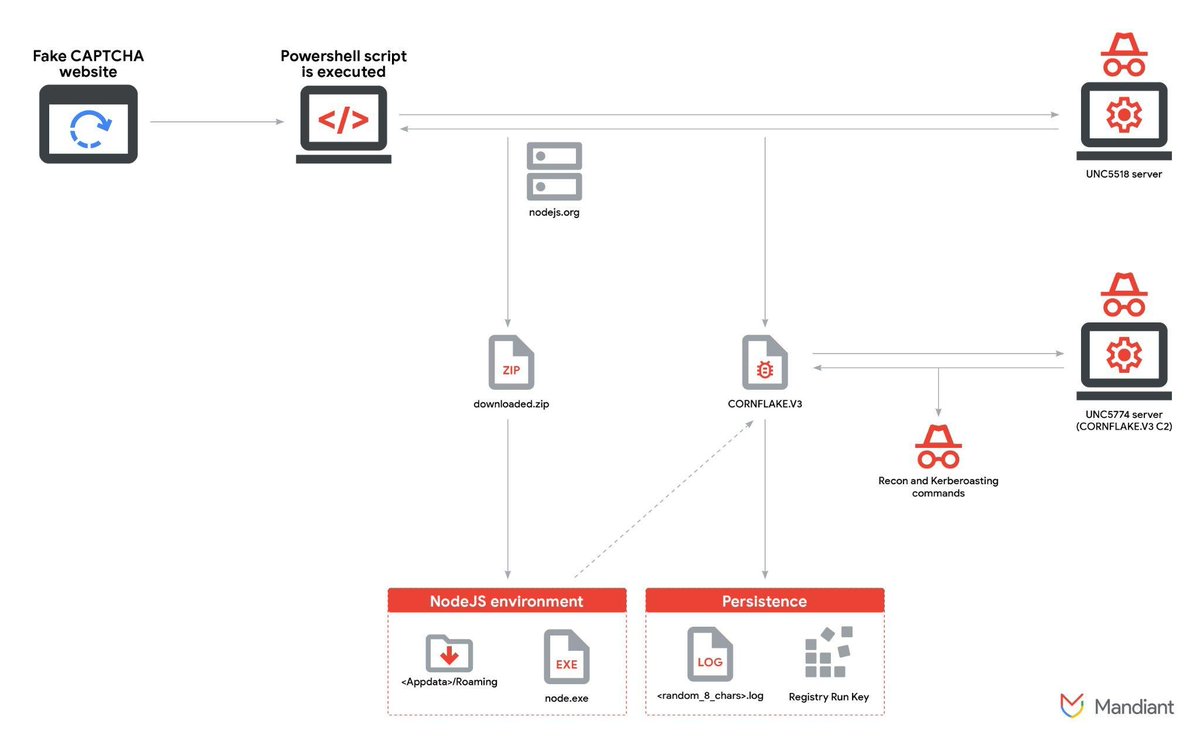
New Mandiant (part of Google Cloud) research: Financially motivated actor #UNC5518 is using ClickFix (fake CAPTCHA) lures on compromised websites to provide initial access-as-a-service. This access is leveraged by partner group #UNC5774 to deploy the CORNFLAKE.V3 backdoor. cloud.google.com/blog/topics/th…