
45tr00
@amaizing_human
A cyber security enthusiast, CTF player @p3rf3ctr00t.
Building Self Sovereign Identity 🆔️
ID: 1396479120553480199
http://www.perfectroot.wiki 23-05-2021 14:52:48
52 Tweet
27 Followers
113 Following


Final scoreboard of the #BSidesNairobi2024 CTF with p3rf3ctr00t taking the lead in the last minutes. CTFRoom Strathmore University
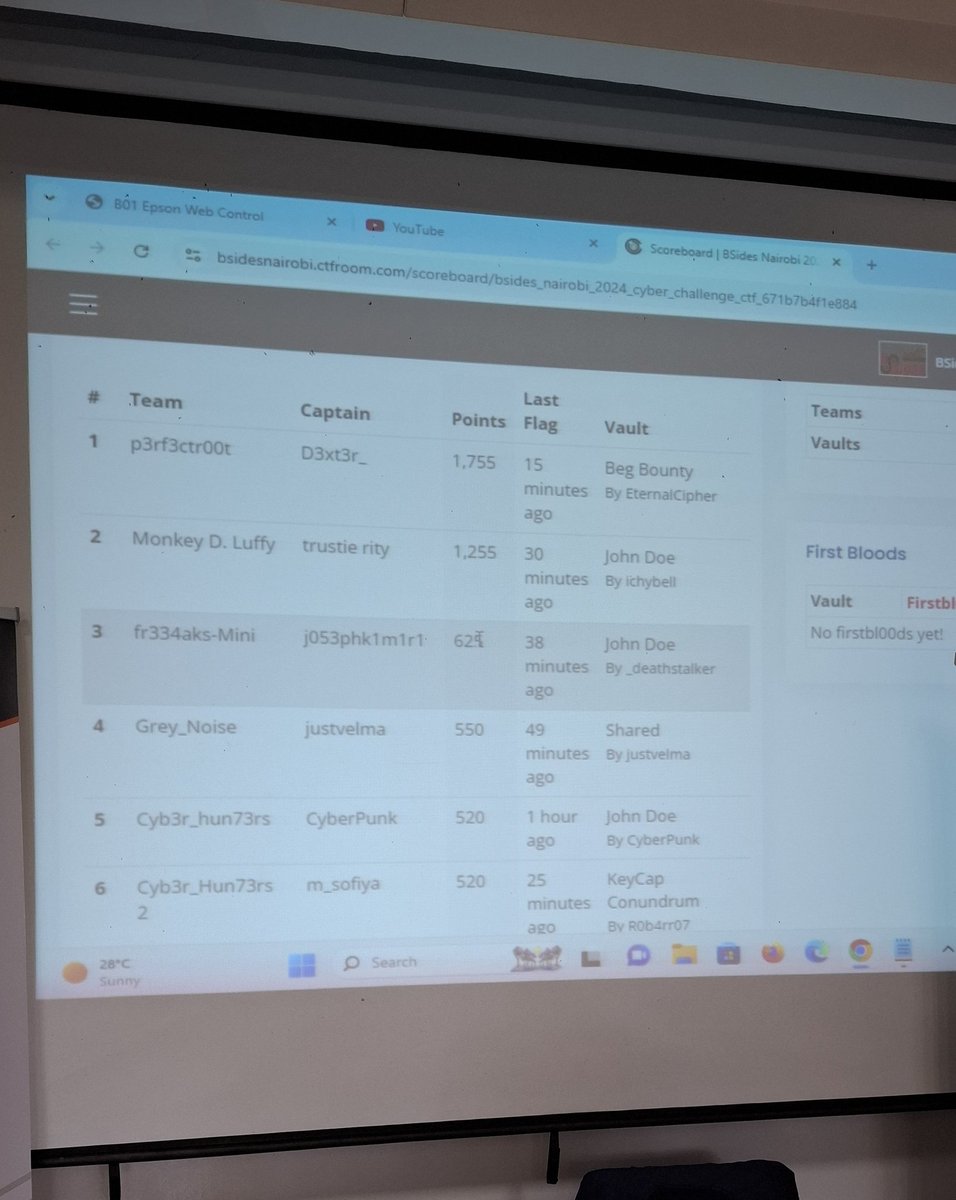




Thank you for playing our CTF! We hope it was both fun and educational. Keep exploring , learning.See you in the next one. Big thank you to our guest challenge creators🙏: Oste Winter Tahaa Farooq Joel. they call me jjjohn And p3rf3ctr00t team members





















