Ács Dávid
@acsdavid97
Computer Science student, interested in all things Red & Blue team.
ID: 772395450930462720
04-09-2016 11:26:40
39 Tweet
36 Followers
389 Following

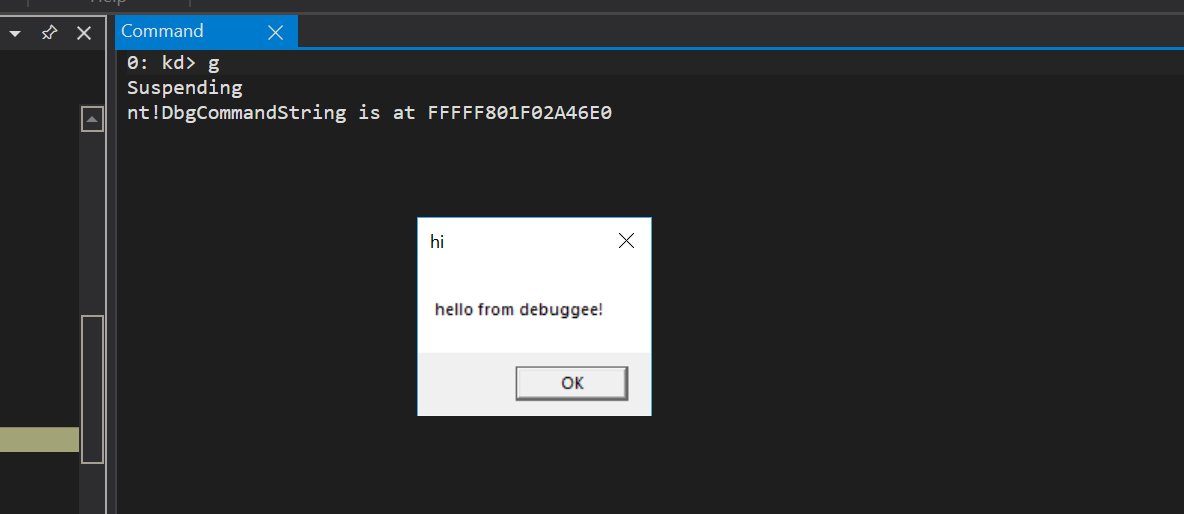
ntoskrnl.exe has an undocumented function, nt!DbgCommandString() that allows a driver of a #Kd debuggee to execute #windbg commands (so, any code) on the session of the debugger (#win7 -> #win10). So be careful when debugging untrusted drivers via #Kd 😅 Found by Alex Ionescu




We have downloaded and archived everything shared by conti leaks thus far. - Chat logs 2020 - 2022 - Internal software source code - Jabber chat logs 2021 - 2022 - Pony leak - Rocket Chat logs - Screenshots, December 2021 - Trickbot forum Download: share.vx-underground.org



"Password expiration requirements do more harm than good, because these requirements make users select predictable passwords" Thank you Microsoft. NIST agrees. Everyone who attacks password auth agrees. Can we get compliance to update their requirements. docs.microsoft.com/en-us/microsof…








hacker.house port 48101 has been showing increasingly growing numbers, a week ago around 450k, 2 days ago 850k and 950k today