Sean Hopkins
@_seahop
Red teamer, terrible coder. Black Badge Defcon30.
ID: 1431702456313032708
28-08-2021 19:37:36
618 Tweet
182 Followers
207 Following












Why should Microsoft's Nested App Authentication (NAA) should be on your security team's radar? Hope Walker breaks down NAA and shows how attackers can pivot between Azure resources using brokered authentication. ghst.ly/45h2Zw3




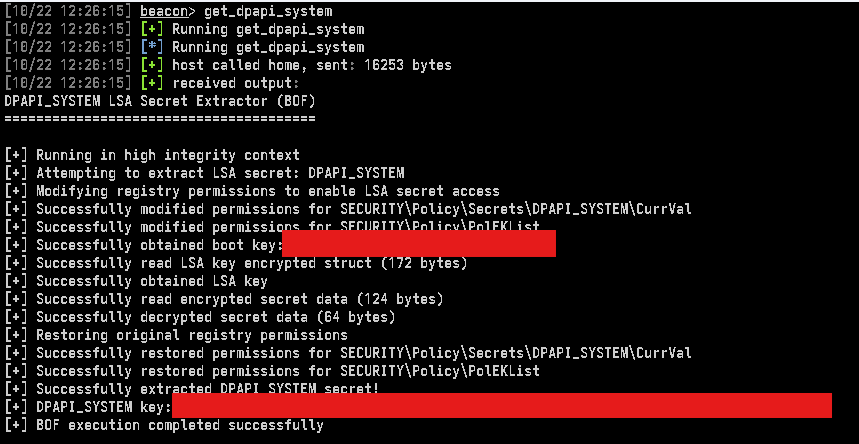
Credential Guard was supposed to end credential dumping. It didn't. Valdemar Carøe just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled. Read for more ⤵️ ghst.ly/4qtl2rm


Last month, Dylan Tran and I gave a talk Munich Cyber Tactics, Techniques and Procedures called "COM to the Darkside" focusing on COM/DCOM cross-session and fileless lateral movement tradecraft. Check out the slides here: github.com/bohops/COM-to-… Recording should be released soon.

Forget common backdoors — a DLL hijack in Windows Narrator can grant SYSTEM-level persistence at login. In our new blog, Oddvar Moe shows how attackers abuse accessibility features and what defenders should monitor. Read now! trustedsec.com/blog/hack-cess…