
mrroot
@_mohd_saqlain
Application Security Engineer | bbhunter.com/mrrootsec
ID: 2219265548
https://mrrootsec.vercel.app 28-11-2013 09:03:25
2,2K Tweet
862 Followers
404 Following

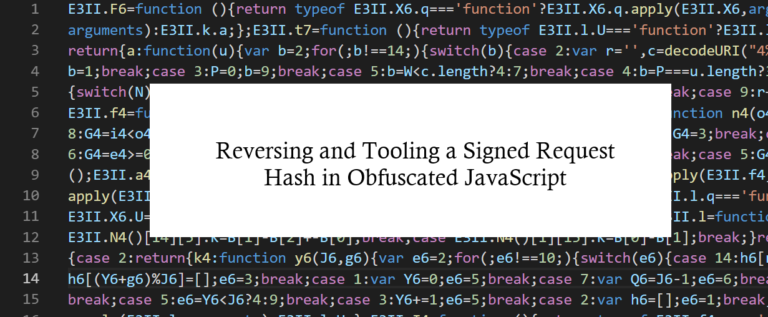
Reversing and Tooling a Signed Request Hash in Obfuscated JavaScript buer.haus/2024/01/16/rev… Thanks to HackingHub for putting together a lab to learn more about it: app.hackinghub.io/surl



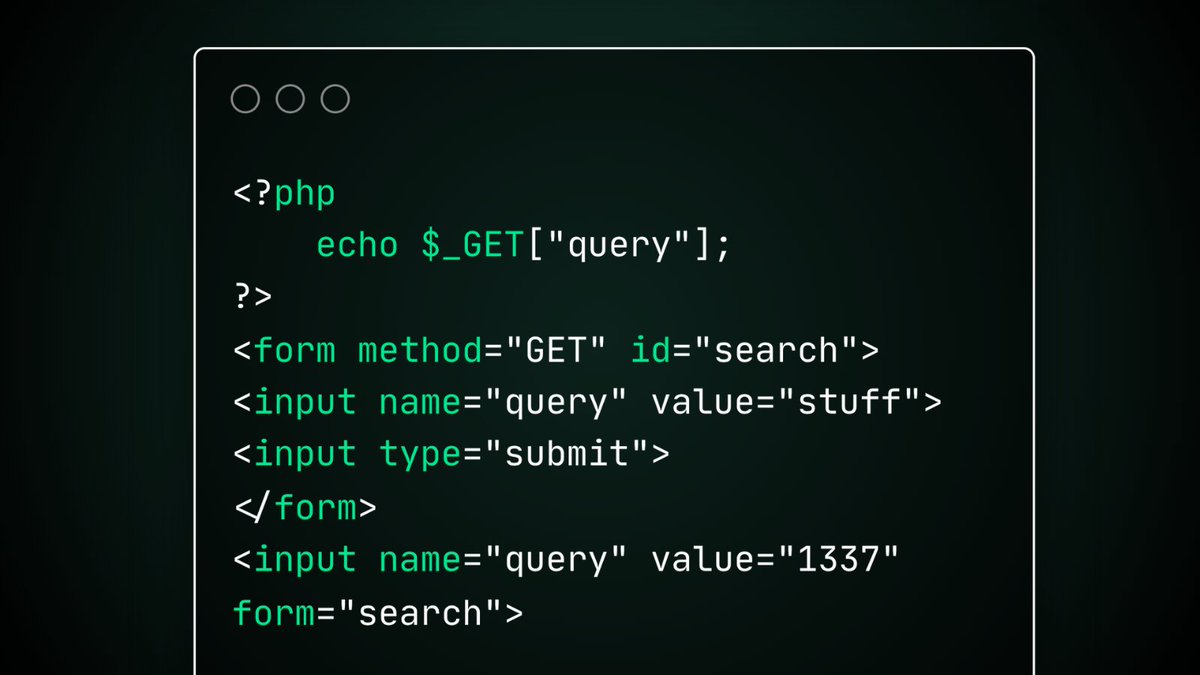
Did you know an input can use the form attribute to link to a form by ID letting it submit with the form even if it’s placed outside of it!? 👀 In this PHP example, an input outside the form adds a URL argument and only the second parm value (1337) is echoed. S/O to Andreas Söderlund


Ryan Barnett (B0N3) Even full-er list here github.com/ACK-J/CSP-B-Go…







When applying for a job at McDonald's, over 90% of franchises use "Olivia," an AI-powered chatbot. We (Ian Carroll and I) discovered a vulnerability that could allow an attacker to access the over 64 million chat records using the password "123456". ian.sh/mcdonalds


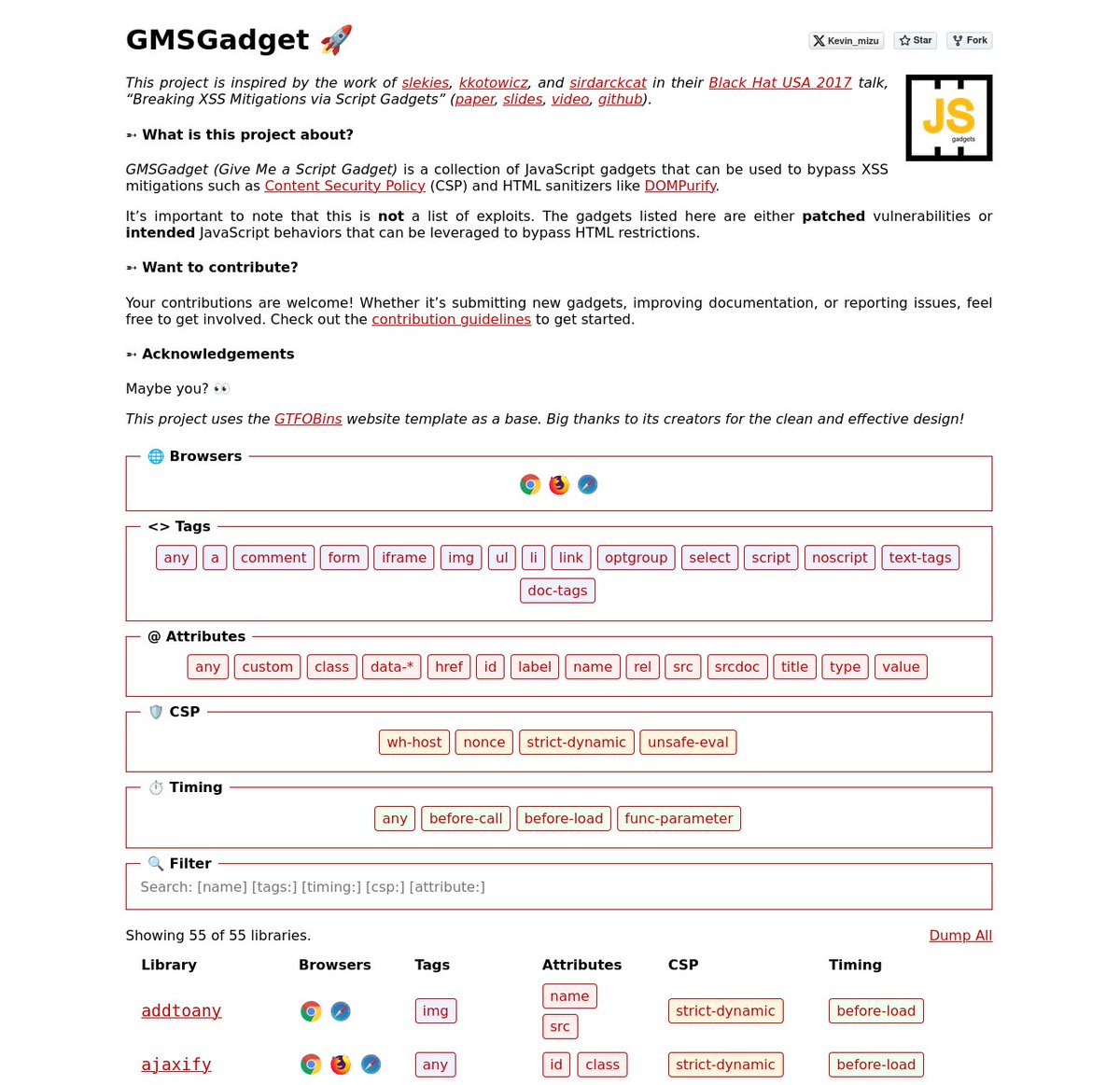
I'm happy to release a script gadgets wiki inspired by the work of Sebastian Lekies, koto, and Eduardo Vela in their Black Hat USA 2017 talk! 🔥 The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇 gmsgadget.com 1/4




Sleepless Strings - Template Injection in Insomnia - Tanto Security tantosec.com/blog/2025/06/i…



