Olga Barinova
@_lely___
Manager, Product Security @Okta
ID: 2739675225
11-08-2014 07:09:00
82 Tweet
838 Followers
310 Following










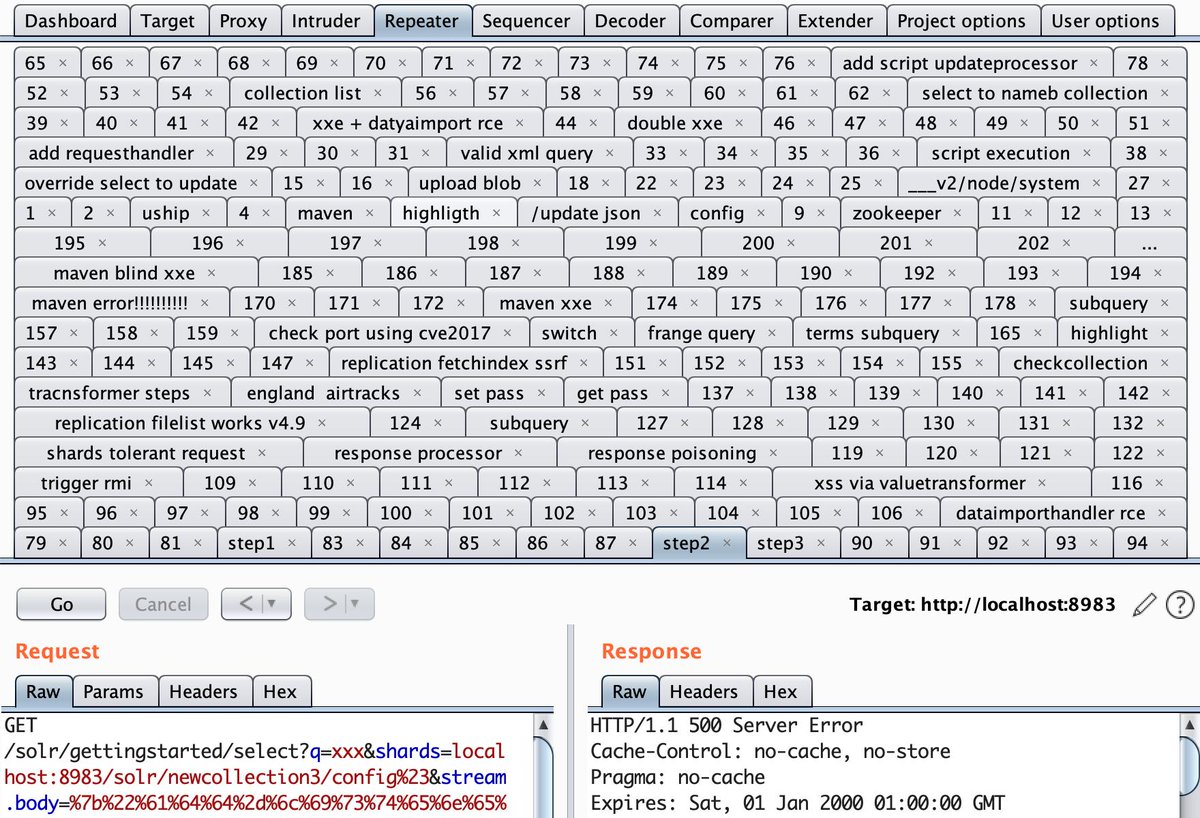
Our guy, @[email protected], had a presentation at OWASP Poland Day about exploiting prototype pollution to RCE on the example of Kibana, by abusing environmental variables in node. The slides are here: slides.com/securitymb/pro… We will also release a writeup soon so stay in touch!


I'm excited to share my post about discovering & exploiting multiple critical vulnerabilities in Cisco's DCNM. Busting Cisco's Beans :: Hardcoding Your Way to Hell srcincite.io/blog/2020/01/1… PoC exploit code: srcincite.io/pocs/cve-2019-… srcincite.io/pocs/cve-2019-… srcincite.io/pocs/cve-2019-…

Up next and making his #Pwn2Own debut, Michael Stepankin (Michael Stepankin) of Veracode will be targeting a remote code execution with continuation against the Inductive Automation Ignition in the Control Server category. #P2OMiami #S4x20

We have confirmed the successful demonstration from Michael Stepankin used a previously reported bug. This counts as a partial win, but does earn him 12.5 Master of Pwn points. #P2OMiami #S4x20


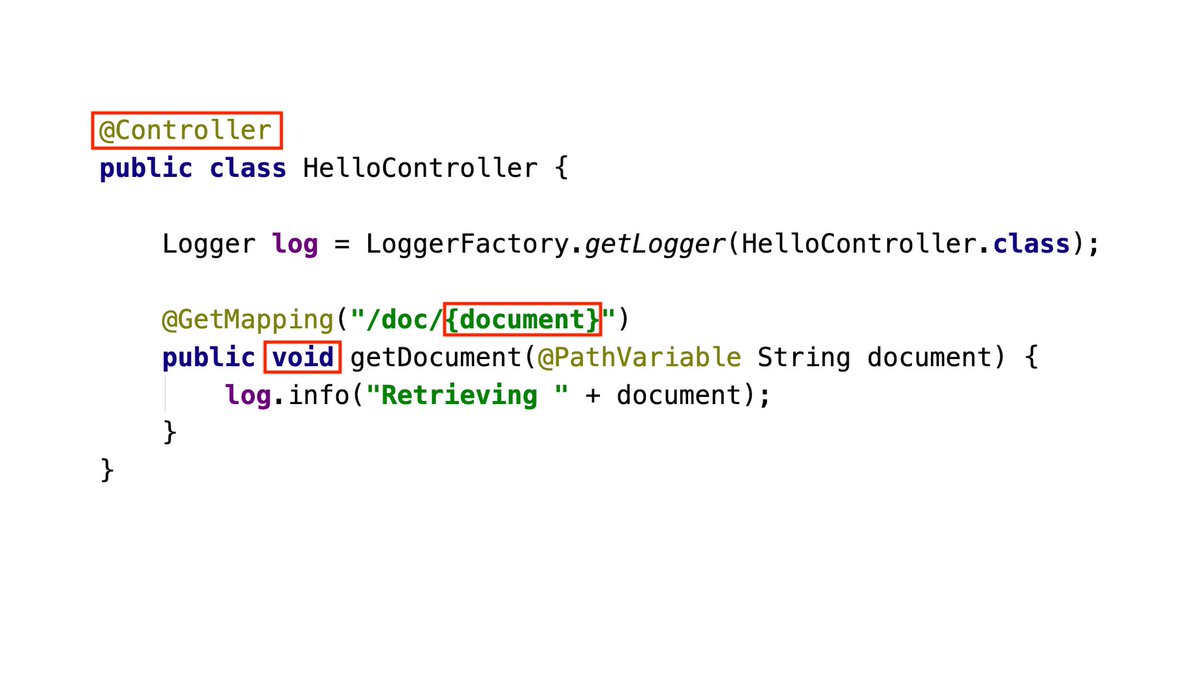
Can you spot a critical vulnerability in this innocent code? Learn about Spring View Manipulation in our latest article github.com/veracode-resea… #java Spring Framework


The top 10 web hacking techniques of 2020, by James Kettle with help from FD, Soroush Dalili, Nicolas Grégoire and the entire community portswigger.net/research/top-1…

New attacks on OAuth: SSRF by design and Session Poisoning by Michael Stepankin portswigger.net/research/hidde…

The comprehensive list of today's emerging threats, nOtWASP bottom 10: vulnerabilities that make you cry by James Kettle, Michael Stepankin and Gareth Heyes \u2028 portswigger.net/research/notwa…