
Jonas Wagner
@_jwagner
Co-Founder & CTO @threatray
ID: 1298368650
25-03-2013 08:42:25
36 Tweet
80 Followers
117 Following




We’re very pleased to announce that John Fokker has joined the Threatray team as an advisor! Read more about John and Threatray here: threatray.com/blog/introduci…




Curious about how to identify #Malware attacks with Threatray? Follow our CTO and Co-founder Jonas Wagner through the process in Part 1 of our new series. Watch the video here: youtu.be/UfC2vP6QlqQ

Hunting and Pivoting are essential for #ThreatIntelligence and #DetectionEngineering. Listen to our CTO and Co-founder Jonas Wagner on how Threatray does it in Part 2 of our new series. youtu.be/A3pS97ceq4Y

Staring at your #IDAPro disassembler window and wondering if you’ve seen this code before? Get a walkthrough of our CTO and Co-founder Jonas Wagner on how Threatray brings #BinaryIntelligence into your #ReverseEngineering workflows in Part 3 of our series. youtu.be/y4oP2LGRT7g

We discovered additional insights complementing the CYFIRMA Research report cyfirma.com/research/qwert… on the 'QWERTY Stealer' sample. Our analysis attributes this sample to the DoNot_Downloader family, which is linked to #APT_C_35, also known as the #DoNotTeam. 1/n


Our code analysis engine has found that the malware sample 4dd08b0bab6f19d143cca6f96c8b780da7f60dbf74f1c16c3442bc9f07d38030 — recently reported as Nnice ransomware by CYFIRMA Research cyfirma.com/research/nnice… is identical to the Slam ransomware sample 1/3


🚨 Following up on SentinelOne recent ransomware analysis: Our code search engine has discovered AidLocker/Frag, variants of HellCat/Morpheus. Our findings show that: (1) Like HellCat/Morpheus, AidLocker/Frag are code-wise identical but use different branding in their ransom


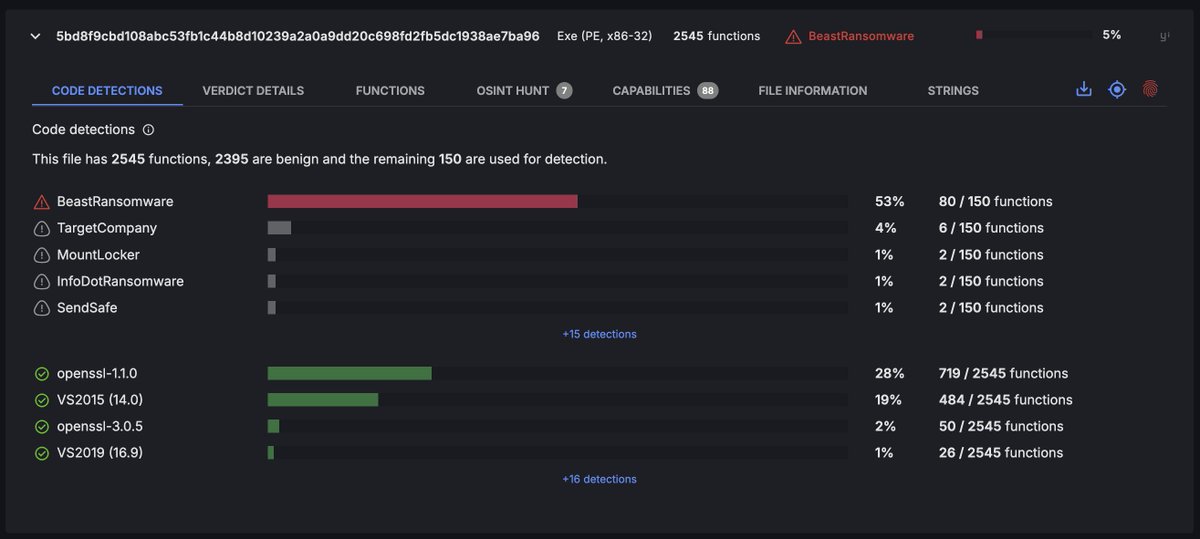
Our code analysis engine has found that the malware sample 5bd8f9cbd108abc53fb1c44b8d10239a2a0a9dd20c698fd2fb5dc1938ae7ba96 is a variant of Beast ransomware. This sample was recently reported as Boramae ransomware by CYFIRMA Research cyfirma.com/research/boram…. We compared this sample




Threatray's Abdallah Elshinbary and Jonas Wagner in collaboration with Proofpoint Threat Research Team have undertaken a deep dive into the India-aligned #Bitter (TA397) cyber espionage group. Read part one over at Proofpoint, where they cover campaigns, infection chains, hand-on-keyboard


⚡ Exciting Update ⚡ We're thrilled to announce our new partnership with Nextron Systems to take YARA rule development and malware classification to a whole new level. 🚀 This collaboration brings Nextron's high-quality YARA rules from THOR Thunderstorm directly into

