pavan
@619_pavan
Cyber Security Professional
ID: 1150232911
05-02-2013 07:21:44
38 Tweet
29 Followers
515 Following

There is so much to learn from malware traffic! #pcap #netsec #Malware #cerber packettotal.com/app/search?q=c… #emotet packettotal.com/app/search?q=e… #gh0st packettotal.com/app/search?q=g… #kovter packettotal.com/app/search?q=k… #mirai packettotal.com/app/search?q=m… #nanocore packettotal.com/app/search?q=n…








SANS Data Incident 2020 - Technical Details on YouTube Archive | youtu.be/x2yNy-atf5g by myself Mike Pilkington and Lance Spitzner posted on YouTube SANS Institute


An idea evolved in a Statesman's mind is accepted & implemented across the nation benefiting millions of farmers #KCR #RYTHUBANDHU has become a slogan of development for farmers. When such slogans become a Nations pride you become praiseworthy to it @KTRTRS Singireddy Niranjan Reddy

The AWS Instance Metadata service strikes again! Privilege Escalation in AWS Elastic Kubernetes Service by compromising the instance role of worker nodes blog.christophetd.fr/privilege-esca… ... or how a single compromised pod in an EKS cluster can have serious account-wide consequences.







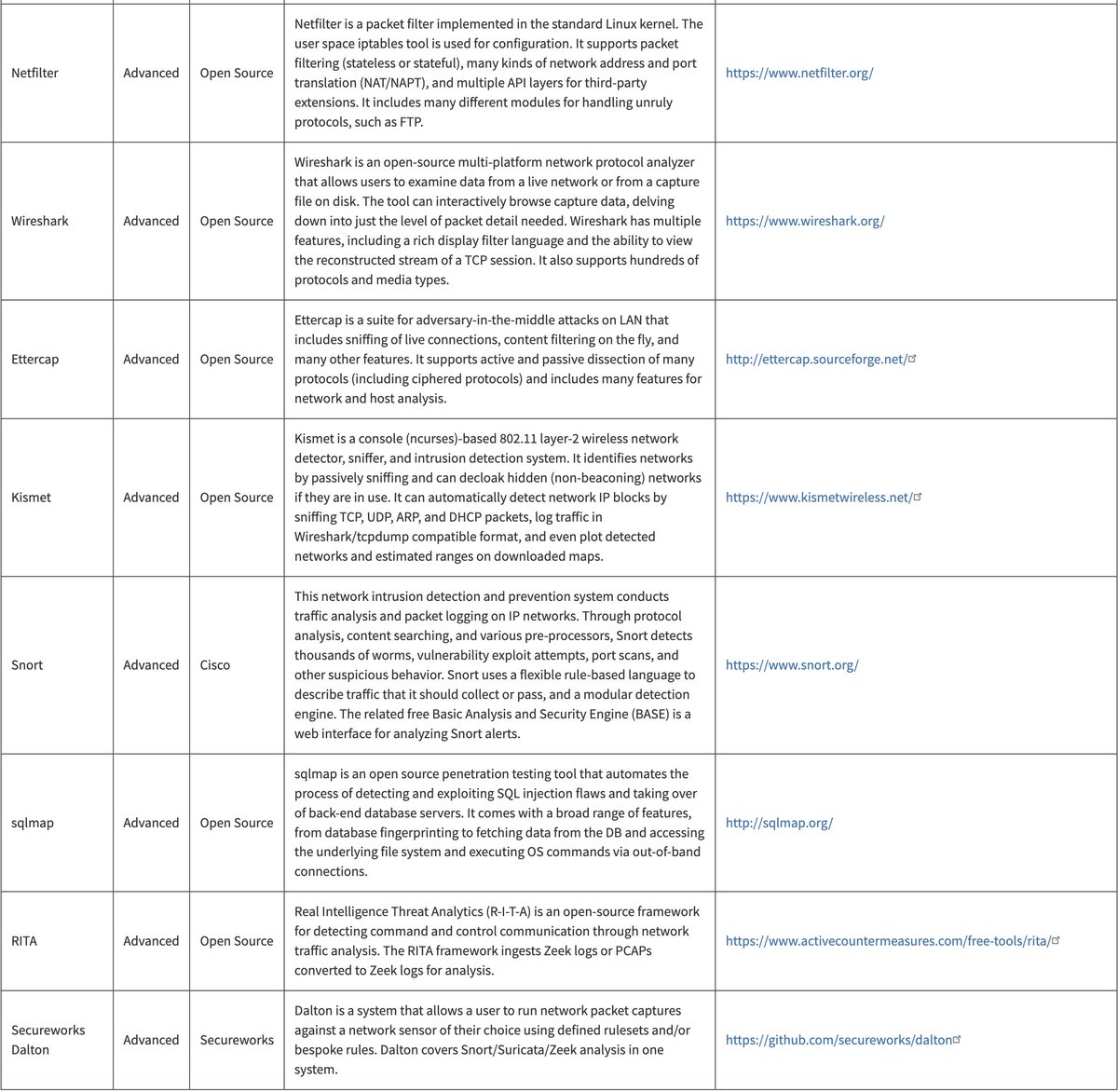
This is a pretty solid list of free cybersecurity tools/feeds/services from Cybersecurity and Infrastructure Security Agency cisa.gov/free-cybersecu… It's also VERY useful for folks looking to get hands on experience with different aspects of cyber without paying for tools.