Ne0ne
@0xtoxin
Security Researcher at @msftsecurity | Ex - Perception Point Threat Analyst & Team Lead
ID: 1540090536685617155
https://0xtoxin.github.io/ 23-06-2022 21:53:03
2,2K Tweet
10,10K Followers
314 Following










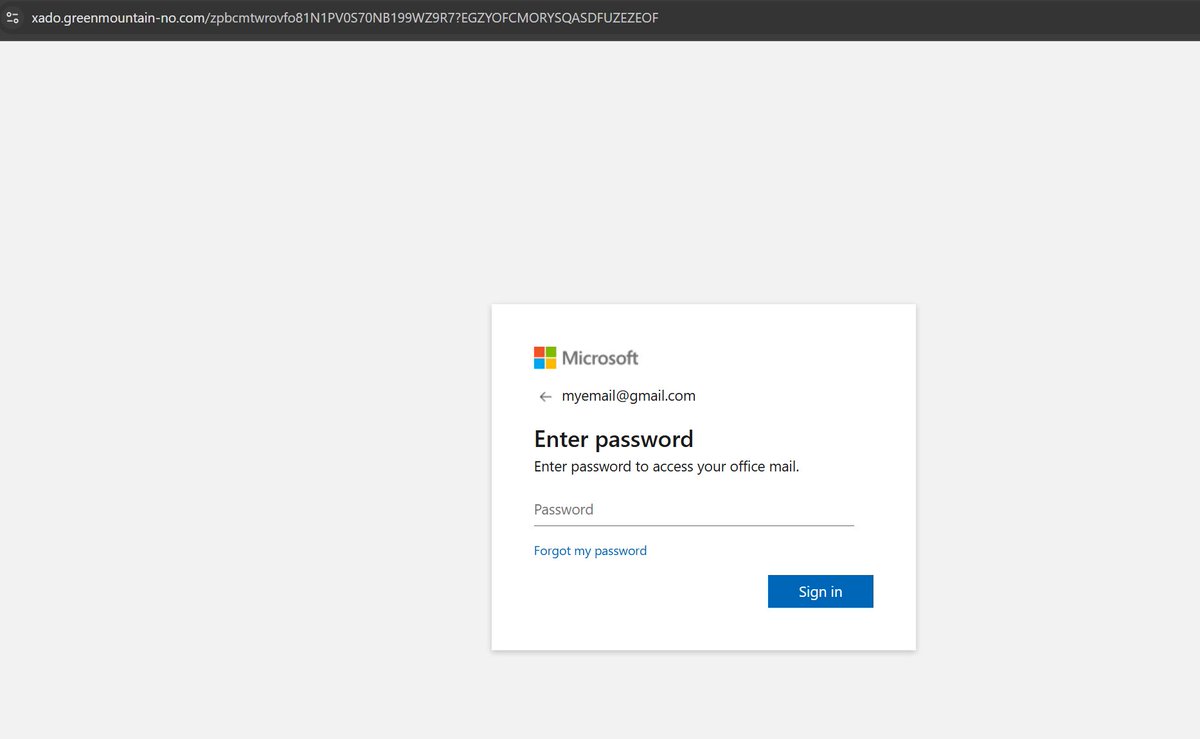
#Tycoon #Phishing With the help of Who said what?, we identified additional 482 domains linked to Tycoon. Here’s a list of domains+subdomains+full path, hosting Outlook/Gmail phishing pages: pastebin.com/r56UtHbD
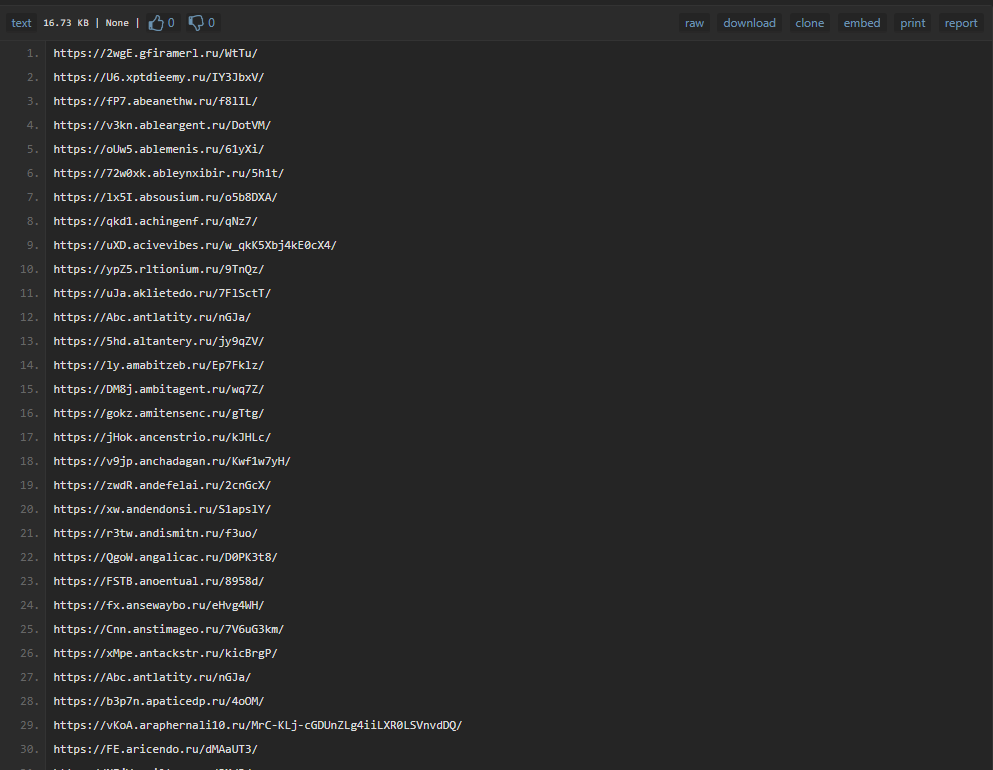




#Tycoon #Phishing Got more domains with the help of Who said what? 571 domains linked to Tycoon. Here’s a list of domains+subdomains+full path, hosting Outlook/Gmail phishing pages: pastebin.com/jp0uTrK4 A few of them are waiting for API renew (TA's didn't pay the bill 😂)






![Germán Fernández (@1zrr4h) on Twitter photo Nueva campaña de #FenixBotnet dirigida a México 🇲🇽
Ahora también utilizando la técnica "Copy&Paste"
Distribución a través de SMS con URL:
▪ https://sat[.]citatorio[.]com/file/declaracion.pdf (falso PDF).
Siguientes etapas desde:
▪ https://d3f8cv[.]top/d1zK3flPWA/v.txt
▪ Nueva campaña de #FenixBotnet dirigida a México 🇲🇽
Ahora también utilizando la técnica "Copy&Paste"
Distribución a través de SMS con URL:
▪ https://sat[.]citatorio[.]com/file/declaracion.pdf (falso PDF).
Siguientes etapas desde:
▪ https://d3f8cv[.]top/d1zK3flPWA/v.txt
▪](https://pbs.twimg.com/media/GZ5T8veWoAAxBrq.png)

![JAMESWT (@jameswt_wt) on Twitter photo #Donut > #AsyncRat #purehvnc ..etc
from initial <a href="/pr0xylife/">proxylife</a> samples
🔱Samples related to kendychop[.]shop
bazaar.abuse.ch/browse/tag/ken…
🔆AnyRun
app.any.run/tasks/952c1450… #Donut > #AsyncRat #purehvnc ..etc
from initial <a href="/pr0xylife/">proxylife</a> samples
🔱Samples related to kendychop[.]shop
bazaar.abuse.ch/browse/tag/ken…
🔆AnyRun
app.any.run/tasks/952c1450…](https://pbs.twimg.com/media/GcQNfI6XQAAexne.jpg)
![JAMESWT (@jameswt_wt) on Twitter photo "Booking. com lnvoice" spam email
PDF>url>js>urls>js >#rhadamanthys
Urls
b00king[.]com[.]ng/
urlhaus.abuse.ch/browse/tag/Rha…
C2
185.196.11.]18:7257
Samples
bazaar.abuse.ch/browse/tag/185…
AnyRun
app.any.run/tasks/b2627223…
app.any.run/tasks/6ecbae95… "Booking. com lnvoice" spam email
PDF>url>js>urls>js >#rhadamanthys
Urls
b00king[.]com[.]ng/
urlhaus.abuse.ch/browse/tag/Rha…
C2
185.196.11.]18:7257
Samples
bazaar.abuse.ch/browse/tag/185…
AnyRun
app.any.run/tasks/b2627223…
app.any.run/tasks/6ecbae95…](https://pbs.twimg.com/media/Gds2vhaXEAAZ2AH.png)
![JAMESWT (@jameswt_wt) on Twitter photo #Booking : Immediate Response Needed - Guest Items"
👇
https://extraguestreview.]com/#eM_0MX3z
👇#fakecaptcha
https://booking.extraguestreview].com/sign-in?
👇
http://92.255.57.]155/Capcha.html
👇
Samples #XWorm V5.6
bazaar.abuse.ch/browse/tag/92-… #Booking : Immediate Response Needed - Guest Items"
👇
https://extraguestreview.]com/#eM_0MX3z
👇#fakecaptcha
https://booking.extraguestreview].com/sign-in?
👇
http://92.255.57.]155/Capcha.html
👇
Samples #XWorm V5.6
bazaar.abuse.ch/browse/tag/92-…](https://pbs.twimg.com/media/GfEIhyTXYAAauRF.jpg)
![JAMESWT (@jameswt_wt) on Twitter photo #booking
"We received this message from"
#lummastealer
⛔️bit.]ly/4hdnEnC👇
⛔️admin.bookviewreserve.]com/confirm/login/NbVqArnK👇
⛔️view-reserve.]com/recaptcha-verify.html 👇
⛔️92.255.57.112/1/👇
1.png
2.png
3.png
Samples
bazaar.abuse.ch/browse/tag/boo…
AnyRun
app.any.run/tasks/0ee3a58d… #booking
"We received this message from"
#lummastealer
⛔️bit.]ly/4hdnEnC👇
⛔️admin.bookviewreserve.]com/confirm/login/NbVqArnK👇
⛔️view-reserve.]com/recaptcha-verify.html 👇
⛔️92.255.57.112/1/👇
1.png
2.png
3.png
Samples
bazaar.abuse.ch/browse/tag/boo…
AnyRun
app.any.run/tasks/0ee3a58d…](https://pbs.twimg.com/media/GhPNcW5XgAAtszO.jpg)