
Vikas Khanna
@0xn00b
#Learner #BugHunter #Pentester #InfosecAddict #WebSecurity
ID: 193242082
21-09-2010 10:20:47
810 Tweet
190 Followers
1,1K Following


This blog post by Prashant Kumar was so helpful in doing SQL injection with MS SQL Server. Definitely worth the read.

hackerone.com/reports/771666 A new fully disclosed HTTP Request Smuggling ATO report from yours truly. Thanks Prateek Tiwari and @Zomato for working to help kill this nasty bug. 🙏

Easy way to find BIG-IP Emad Shanab - أبو عبد الله Aditya Shende cat companys |while read url;do test=$(shodan search org:$url http.title:"BIG-IP®-Redirect" | awk '{print $1,$2}');echo -e "\033[32m$url""\033[34m\n$test";done




Want to find critical bugs by changing a single header? Do just like Corben Leo & set your host header to 'localhost' in your next directory bruteforce, the results might be surprising! 🔥 #BugBountyTip #BugBountyTips


BugBounty Resources ♥️♥️🤘 STÖK ✌️ TomNomNom JS0N Haddix Ben Sadeghipour ProjectDiscovery Suraj @farah_hawa01 Aseem Shrey Katie Paxton-Fear Heath Maverick Adams Ameen pry0cc Luke Stephens (hakluke) HAHWUL Reconless github.com/1ndianl33t/Bug…






We've just used Stepper to solve a new Web Security Academy lab. portswigger.net/bappstore/065d… It's a great BApp that allows you to construct multi-step sequences and extract data from any step and re-use that data. This is all done using repeater style tabs.

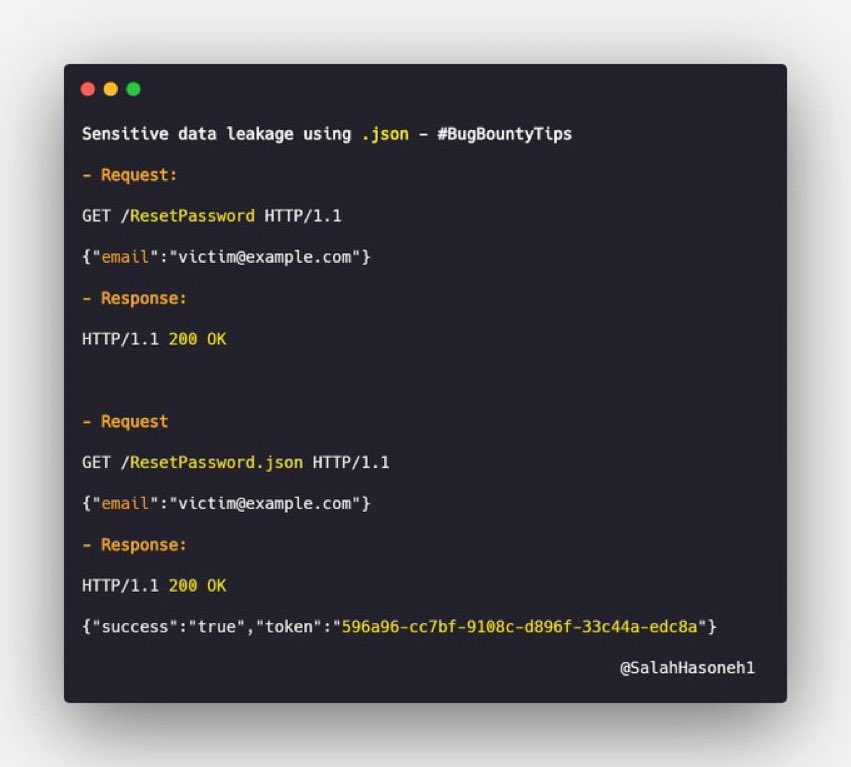
An Awesome Account Takeover just by adding .json on endpoint by Salahaldin #bugbounty #bugbountytip


SSRF Bypass list for localhost (127.0.0.1): http://127.1/ http://0000::1:80/ http://[::]:80/ http://2130706433/ http://[email protected] http://0x7f000001/ http://017700000001 http://0177.00.00.01 Also using a redirect to localhost will often work. #bugbountytips




