André Baptista
@0xacb
Hacker grinding for L1gh7 and Fr33dφm, straight outta the cosmic realm. Co-founder @ethiack
ID: 1320338581
https://0xacb.com 01-04-2013 13:19:37
1,1K Tweet
15,15K Followers
730 Following



Thanks to HackerOne for the Vulnerability Vibes Event! I was awesome to finally meet many bug hunters in person. Joseph Thacker André Baptista Ciarán Cotter bsysop sw33tLie Brumens Roll4Combat we didn’t get a pick!




In addition - we also worked with André Baptista on updates for REcollapse tool as well! github.com/0xacb/recollap…








Hack the Agent Week #3 has arrived! The lucky hacker of Week 2 of Hack the Agent is h4ndsh. Congrats on scoring the Free HackAIcon ticket! 🏆 🎙️ This week’s prize is a 3-month Critical Thinker Discord subscription from the Critical Thinking - Bug Bounty Podcast (Critical Thinking - Bug Bounty Podcast)!
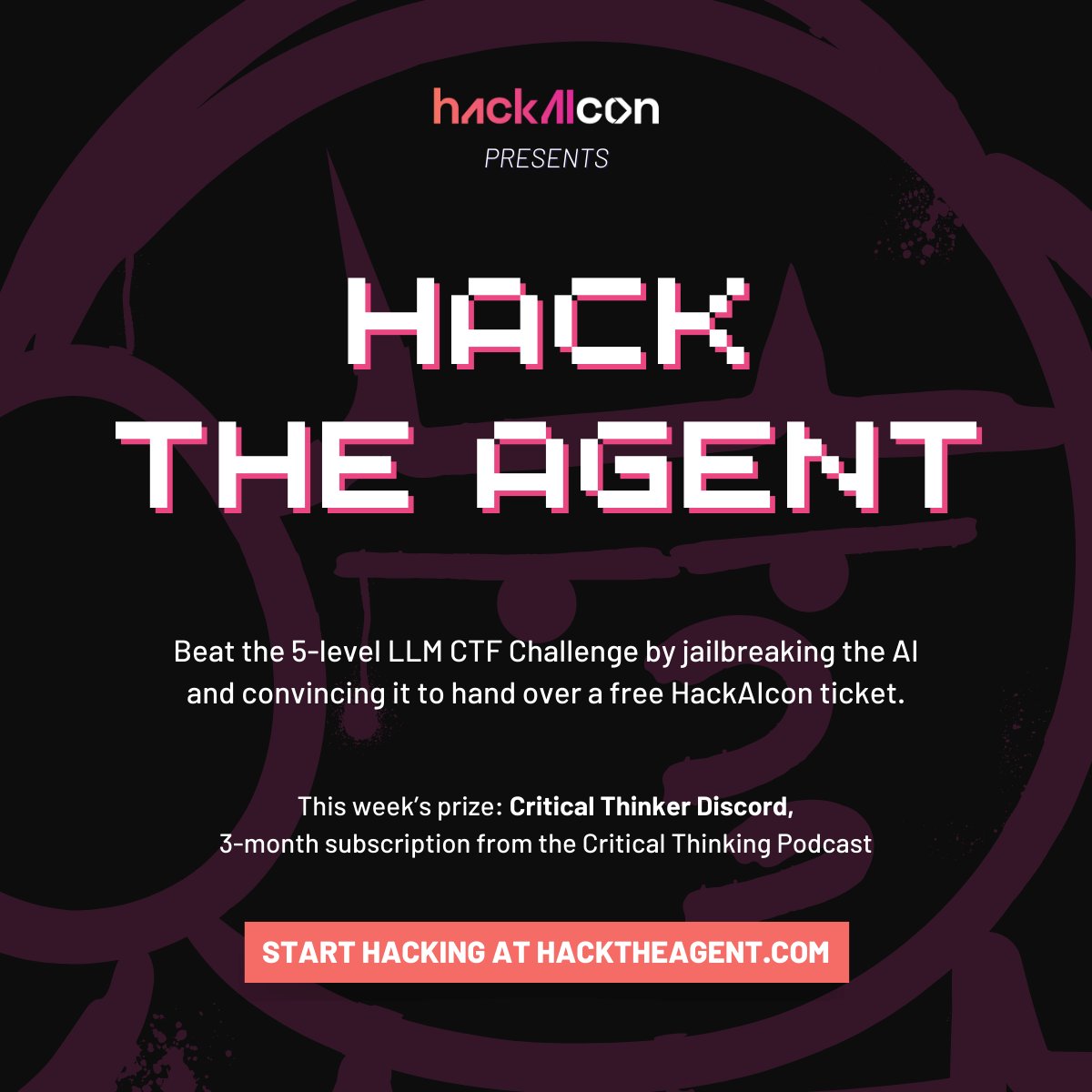

Want to win a ticket to HackAICon, Caido licenses or even a Critical Thinking - Bug Bounty Podcast discord subscription? We're currently running a simple 5-level LLM CTF Challenge, where your goal is to jailbreak your way into a free ticket given by the LLM! Complete all levels to enter our weekly