Md Ismail Šojal 🕷️
@0x0sojalsec
Cyber_Security_Re-searcher || 0SINT || Malware Analysis II Pwn || Ai Re-searcher || @GHOST_3xP10iT || 0ld Accounts Suspended @0xSojalSec ||
ID: 1445347022555340805
https://www.linkedin.com/in/0xsojalsec/ 05-10-2021 11:16:38
34,34K Tweet
28,28K Followers
4,4K Following





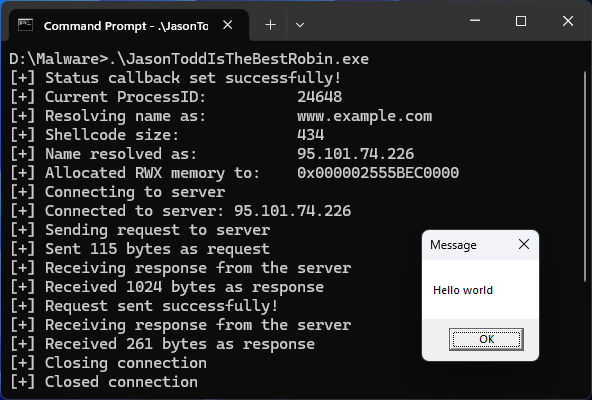
Today I got my 4th valid security vulnerability at Meta Bug Bounty 🥳🥳🥳 WhatsApp is my fav target out there. Try to break the apps logic you may find something #BugBounty #bugbountytip #Bugcrowd


Permission hierarchies hide more than just IDORs. Keep an eye out for complexion hierarchies and surface IDORs, understanding those levels is how you land the big finds 🤑 🎥: Katie Paxton-Fear youtube.com/watch?v=-MsjH-…