EmmsSec
@emmssec
ID: 1034631073135816705
29-08-2018 02:37:25
18 Tweet
42 Followers
430 Following



Bitfi finally gives up claim cryptocurrency wallet is unhackable zd.net/2N6XOY2 by Charlie Osborne





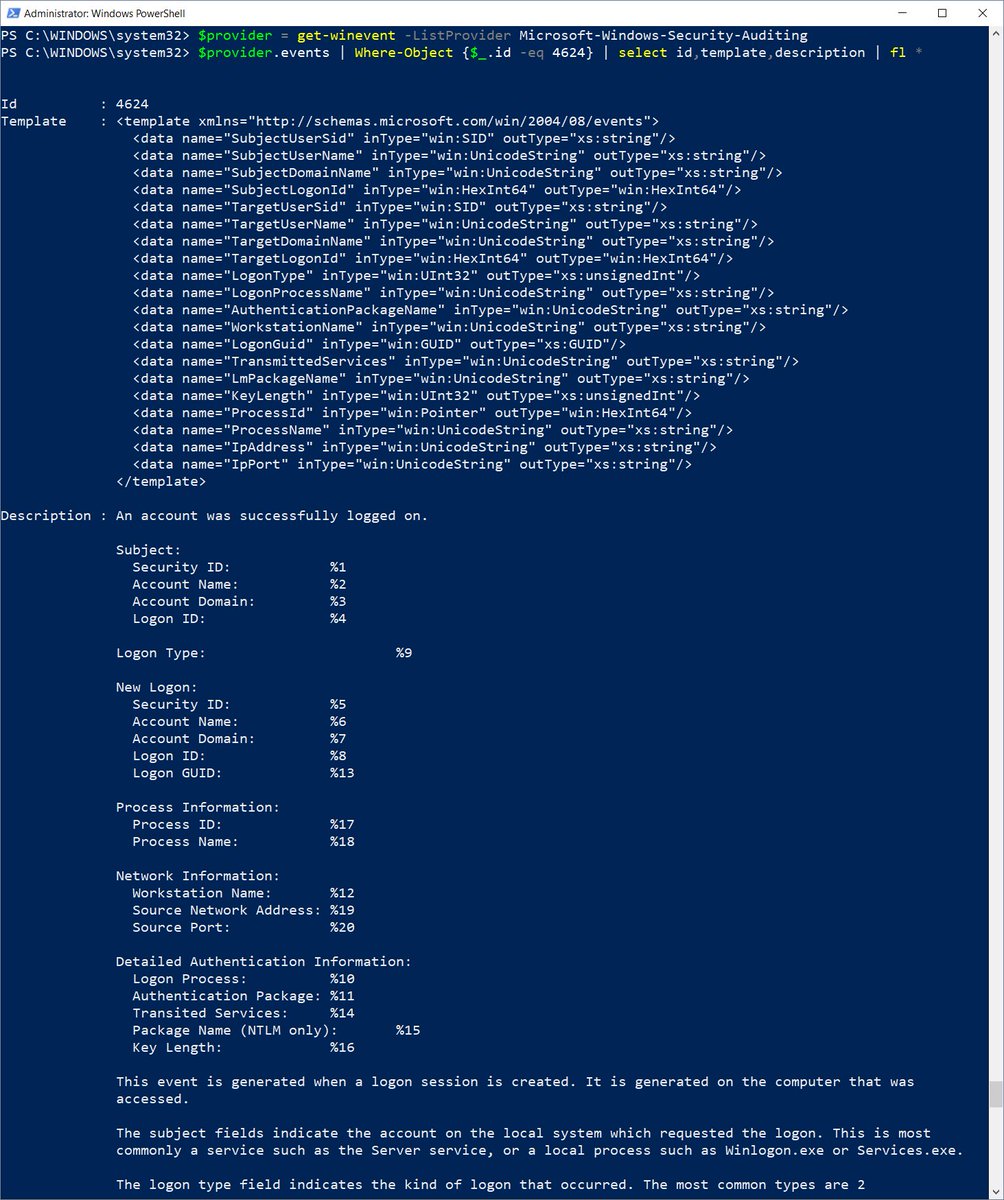
Ever wonder where Windows log descriptions come from? I was going deep on the logging section of my upcoming SANS Institute #SEC450 Blue Team Fundamentals class and ended up with this cool PowerShell command. It dumps all the XML fields and message templates for any event ID!





Ray [REDACTED] don't need the postcode mate, have everything you need Fristname Lastname Card Number Bank Name Issue Date Expiry Date CCV free Pizza's every night till Feb 2023 from what I can see thanks to horizontal "flip" oh, wait, it's safe because he photoshopped out the swipe strip!!
![Dez Blanchfield (@dez_blanchfield) on Twitter photo <a href="/RayRedacted/">Ray [REDACTED]</a> don't need the postcode mate, have everything you need
Fristname Lastname
Card Number
Bank Name
Issue Date
Expiry Date
CCV
free Pizza's every night till Feb 2023 from what I can see thanks to horizontal "flip"
oh, wait, it's safe because he photoshopped out the swipe strip!! <a href="/RayRedacted/">Ray [REDACTED]</a> don't need the postcode mate, have everything you need
Fristname Lastname
Card Number
Bank Name
Issue Date
Expiry Date
CCV
free Pizza's every night till Feb 2023 from what I can see thanks to horizontal "flip"
oh, wait, it's safe because he photoshopped out the swipe strip!!](https://pbs.twimg.com/media/D2osLuYU0AEFBIE.jpg)




For week 2 of #CyberSecurityMonth the Council shares tips to defend against #phishing attacks. #BeCyberSmart National Cybersecurity Alliance Read more: bit.ly/3mNkn3X