
Ectario
@ectari0
Cryptography & Web3 enjoyer:
🇨🇵 CTF Player w/ @MadeinFranceCTF & @Phreaks2600 and Junior Security Researcher @FuzzingLabs
ID: 756980381069479940
http://github.com/ectario 23-07-2016 22:32:41
26 Tweet
60 Takipçi
196 Takip Edilen


PwnMe CTF qualifications are now over! Congratulations to the winning teams: 🥇 RedRocket.Club 🥈 Flat Network Society 🥉 Friendly Maltese Citizens The journey isn’t over yet, see you in France for the finals! 🇫🇷 Thanks to everyone who participated!💘




This weekend, we competed in Insomni'hack CTF and finished 🥉top 3 academic and top 10 overall! It's our third year in a row in the top 3 academic, and the competition keeps getting better every time. Big thanks to the organizers for a well-run event!🔥



🔐 We were proud to sponsor #PwnMeCTF 2025, organized by PHREAKS 2600 & ecole2600 ! 🎉 The finals took place last weekend at 2600 Campus with international teams battling it out onsite 🇫🇷 Huge congrats to everyone who played, and shoutout to the organizers (rayanlecat & co)





#ECSC2025 | 🐓 Découvrez la #TeamFrance 2025 ! 🇫🇷 Sélectionnés à l'issue du FCSC, les joueurs de la ECSC Team France représenteront la drapeau tricolore à Varsovie, en Pologne, dans le cadre de l'European Cybersecurity Challenge. 🔔 RDV en octobre ! PS: #YouAreAllWinners

🚨 Security Disclosure — ICON Validators at Risk 🚨 We (FuzzingLabs) privately disclosed a serious vulnerability in the ICON node client via Immunefi. The issue directly affects all validator nodes on the ICON network. Shortly after our report, ICON Foundation 🌐🔀 cancelled their







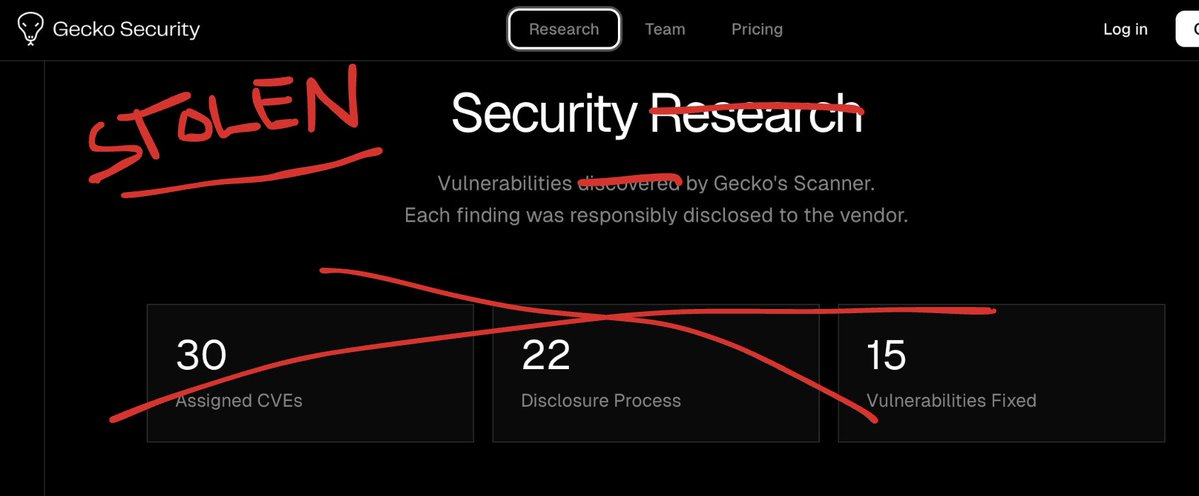
💣 We caught Y Combinator–backed Gecko Security stealing two of our CVEs, one on ollama , one on Gradio. They copied our PoCs, claimed CVE IDs, and even back-dated their blog posts. Here’s the full story 👇

🚨On Oct 16, the DeFi project Typus Finance on the #Sui was exploited. The team released a post-mortem report and thanked SlowMist for assisting in the investigation & fund tracing.🤝 We’ve published a deep dive into the root cause — a permission validation flaw that allowed







