
Ch40s 🏴☠️
@drch40s
Reversing stuffs for fun and always looking for the perfect....former Symantec, RSA, EMC, DELL. Proud RETooling and Malware OPSEC training father.Opinions are…
ID: 2275852955
http://www.retooling.io 12-01-2014 00:46:54
2,2K Tweet
490 Followers
599 Following




New challenge coins celebrating 20 years of Trend Zero Day Initiative ! Want one? Find me at hacker summer camp!




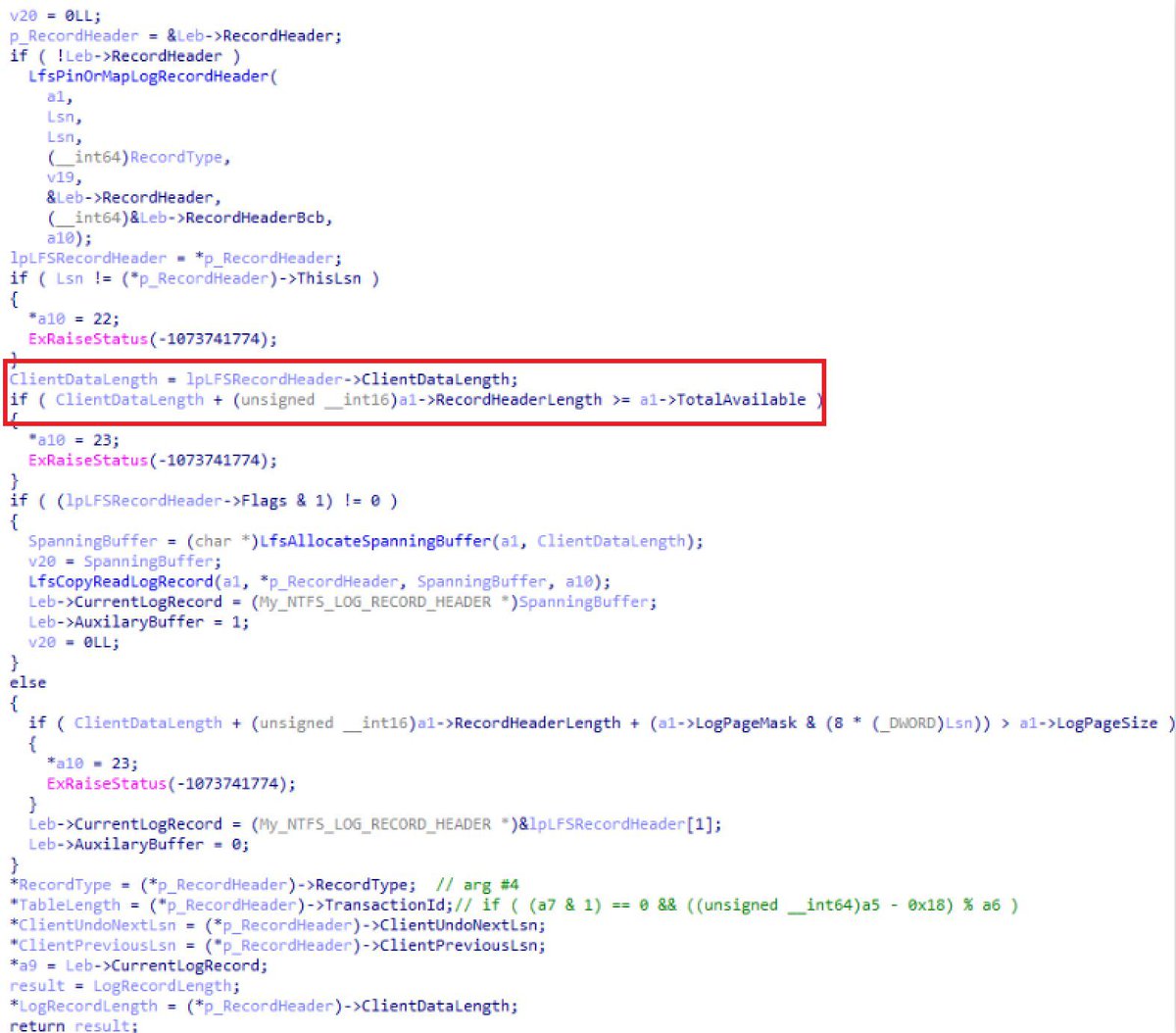
Exploiting a Windows NTFS implementation vulnerability for escalation of priveleges by immortalp0ny swarm.ptsecurity.com/buried-in-the-… #Windows #infosec











Xbow raised $117M to build AI hacker agents, in Alias Robotics open-sourced it and made it completely free. Github: github.com/aliasrobotics/… Paper: arxiv.org/abs/2504.06017









![Nasreddine Bencherchali (@nas_bench) on Twitter photo [New Blog 📚] Echo Chambers - Feedback Loops in Detection Engineering
You ship a detection, get feedback.
Is that feedback accurate? Is it diverse enough? or are you just stuck in an echo chamber of feedback loops?
Read more in this short blog - nasbench.medium.com/echo-chambers-… [New Blog 📚] Echo Chambers - Feedback Loops in Detection Engineering
You ship a detection, get feedback.
Is that feedback accurate? Is it diverse enough? or are you just stuck in an echo chamber of feedback loops?
Read more in this short blog - nasbench.medium.com/echo-chambers-…](https://pbs.twimg.com/media/GyBZ-yPXMAALmQP.jpg)