Dejan Zelic
@dejandayoff
Cloud, WEB-300 (AWAE), and WEB-200 Content Developer at Offensive Security. Also helped on PEN-210(WiFu), PEN-200 (PWK), EXP-312, Thoughts are my own.
ID: 3666946214
https://dejandayoff.com 24-09-2015 05:15:20
153 Tweet
383 Followers
278 Following






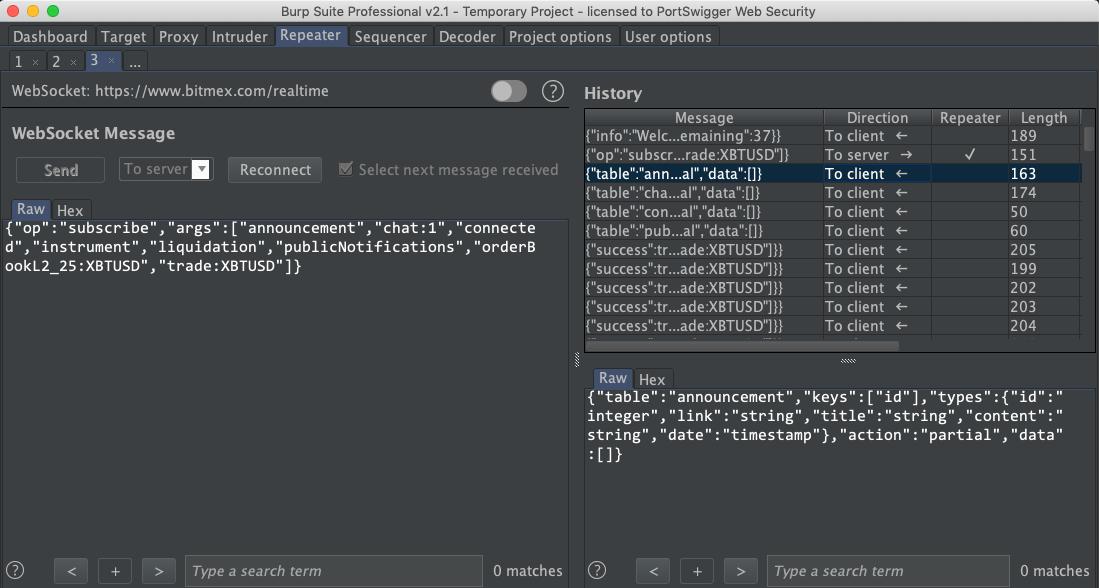
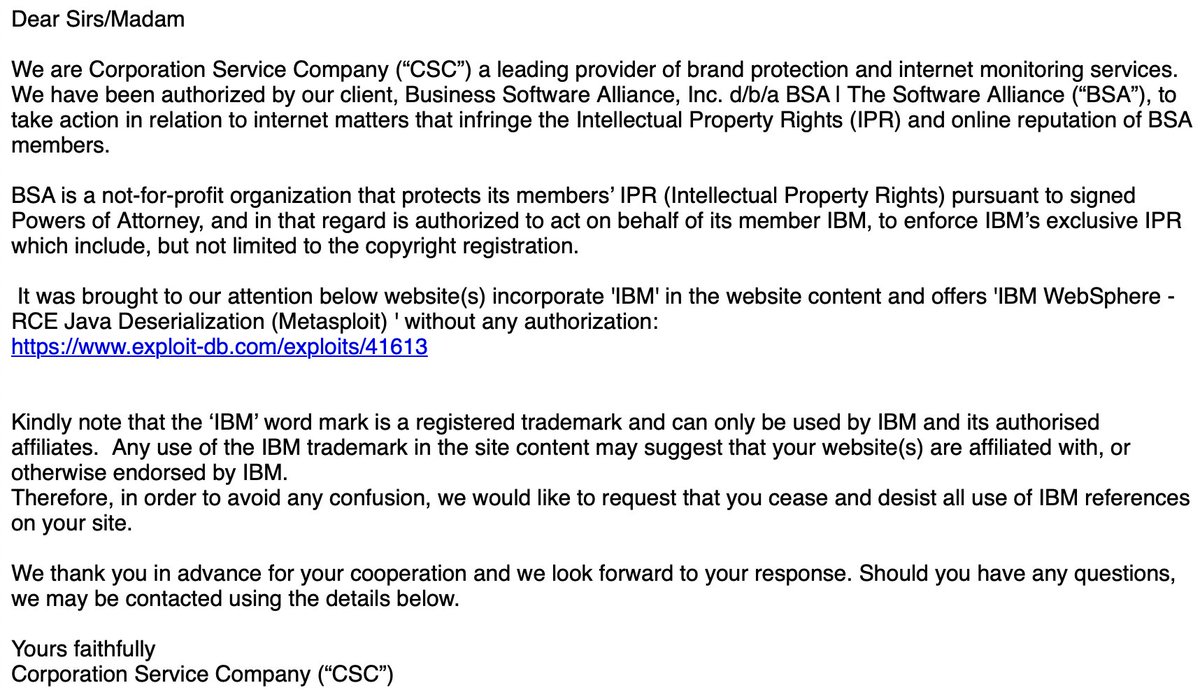
So CSC is doing take down requests on Exploit Database for any entry that contains the string “IBM” on behalf of Business Software Alliance and IBM. Very interesting. Anyone want to place bets on how this is going to turn out? exploit-db.com/exploits/41613




Jennifer Senior What does being "partial to Slavs" mean in these days of fight against racism? Or are we fair game?


AWAE content developer Dejan Zelic discovered and reported an authentication bypass vulnerability in Wekan. Check out the walkthrough: offs.ec/2R8ockW



A few quick posts for the "Beyond the good ol' LaunchAgents" series. Ideas from dade, Bradley Kemp and Dejan Zelic Part 6: SSHRC - theevilbit.github.io/beyond/beyond_… Part 7: xbar - theevilbit.github.io/beyond/beyond_… Part 8: Hammerspoon - theevilbit.github.io/beyond/beyond_…


In case you want a more traditional prompt for your Kali Linux terminal screenshots, pressing Ctrl+P switches it instantly 😌👌 You can permanently configure it and much more with the new kali-tweaks command


I'm not good at bragging, but I'm proud of this. I discovered an authentication bypass vulnerability which leads compromise of a K8s Cluster. I flexed some new muscles and learned to reverse a go binary. github.com/neuvector/neuv… Kudos to SUSE and NeuVector, now part of SUSE for the quick fix!

This was a fun one to find, Arbitrary File Read via Symbolic links in Artifact Hub github.com/artifacthub/hu… Also found SSRF via Rego Policy (github.com/artifacthub/hu…) and Docker Credential Hijacking (github.com/artifacthub/hu…)

I'm happy to publish a blog post regarding some Red Team tradecraft around Slack Impersonation tthat I've been working on. Please see falconspy.org/redteam/tradec… for more info. Big thanks Topher Timzen r00t killah Dejan Zelic for their help.