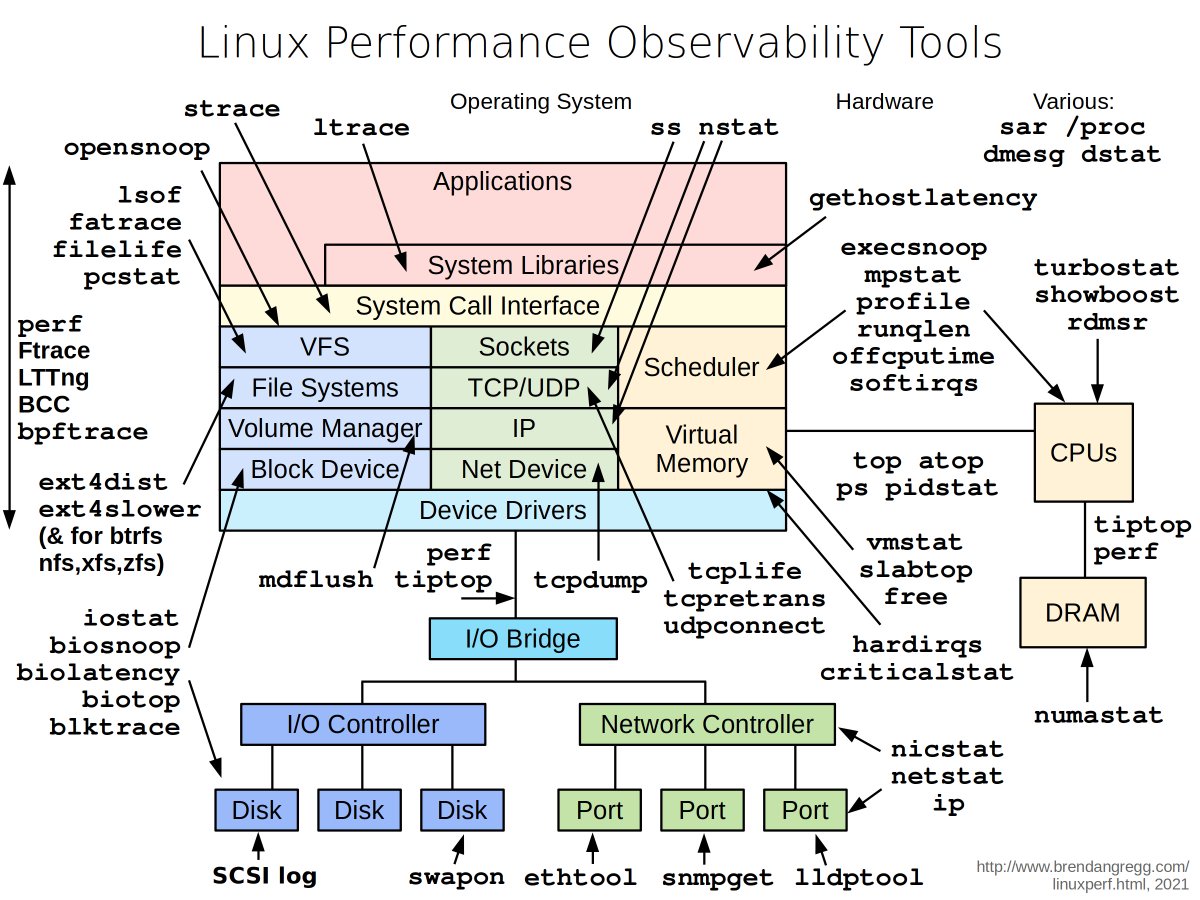
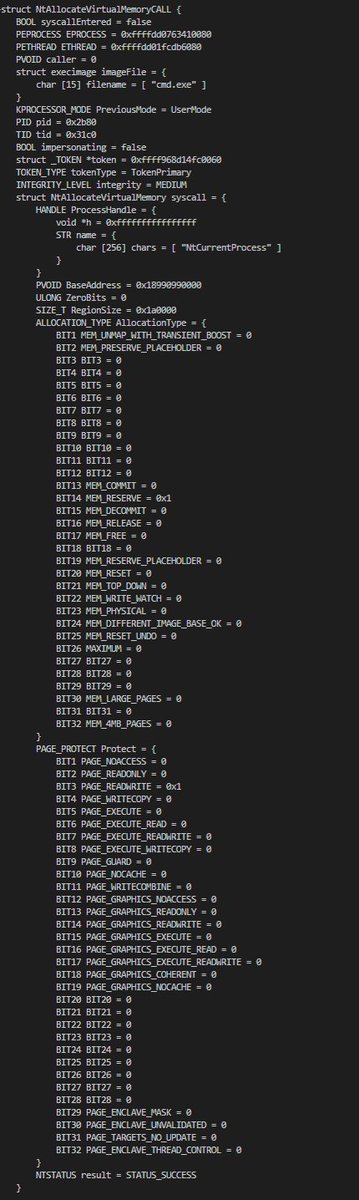
Daniel Shapiro
@wimpypolo

My friend 🌻e. v. m.🌻 and I have been playing around with a WebAPI for Thumb2 firmware reverse engineering, which you can freely use at symgrate.com 1/n











I'm not surprised that Adobe is acquiring Figma for $20B, nor that Wall Street doesn't understand it and $ADBE stock is down more than $20B today. It's a smart move for Adobe because it's nearly impossible to make legacy software applications multi-user collaborative. Thread: 🧵



Excellent LPE write-up by @[email protected] , where he details how suspected compiler changes lead to the introduction of double fetch vulnerabilities. Also discusses a KASLR side channel bypass. PoCs included. Definitely check it out exploits.forsale/24h2-nt-exploi…

Last month Arizona State University I presented my work on formalizing automated bug discovery, developing a framework to characterize the full spectrum of approaches - from fuzzing to human analysis. I'm sharing my evolving perspective on the fundamental nature of the bug finding problem. Full