Vlado Vajdic
@vvlado
post quantum cryptography
ID: 22227248
28-02-2009 04:14:54
5,5K Tweet
383 Followers
542 Following

Microsoft Active Directory Forest Recovery Guide, by Sean Deuby semperis.com/wp-content/upl…




This article is really interesting to me: red.anthropic.com/2025/cyber-too… What if the most pressing security problem to solve with LLMs is how to defend against attackers using them to perform relatively repeatable attacks (e.g. install ransomware on low-to-mid defended environments)?




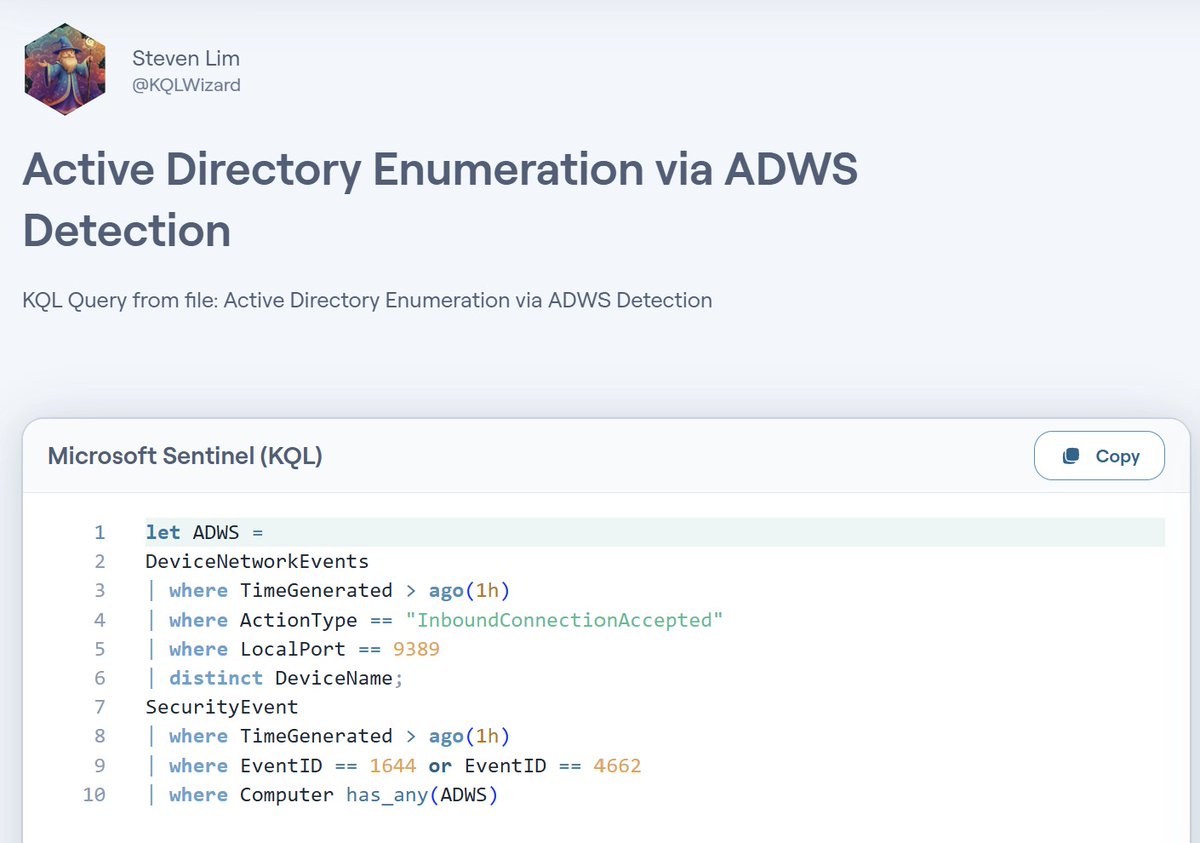
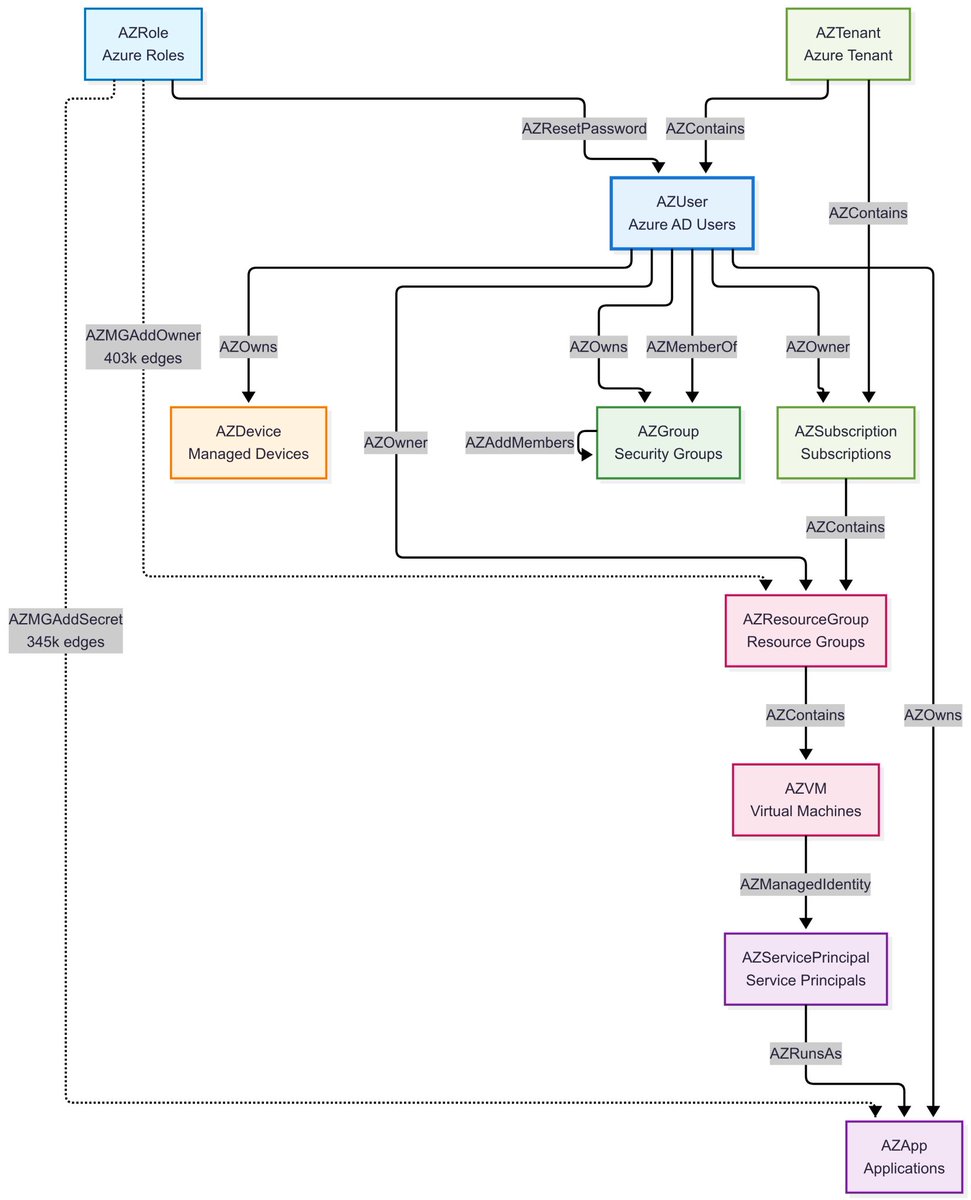
Wanna play around with #KQL and #Graph Microsoft just released sample datasets to play around and look at this gorgeous visualization for the #Bloodhound schema they offer! Thanks Henning Rauch 🥰 learn.microsoft.com/en-us/kusto/qu…


AD recovery is no simple fix; it’s a high-stakes strategy. The right prep, automation, and testing separate organizations that recover fast from those that crumble. Learn how leaders prepare before disaster strikes with Travers Clyde + Cohesity: cohesity.co/41Lm6fq









US army cyber chief: 'The general public does not and usually will never be able to know the extent of America's cyber successes versus its adversaries' | jpost.com/defense-and-te… The Jerusalem Post