voydstack
@voydstack
🥷 @Synacktiv | CTF with @RMUBYGG, @Hexagonctf, @ECSC_TeamFrance 20/21/22/23/24
ID: 1029874665949417473
https://voydstack.re 15-08-2018 23:37:09
593 Tweet
1,1K Followers
886 Following





#ECSC2025 | 🐓 Découvrez la #TeamFrance 2025 ! 🇫🇷 Sélectionnés à l'issue du FCSC, les joueurs de la ECSC Team France représenteront la drapeau tricolore à Varsovie, en Pologne, dans le cadre de l'European Cybersecurity Challenge. 🔔 RDV en octobre ! PS: #YouAreAllWinners










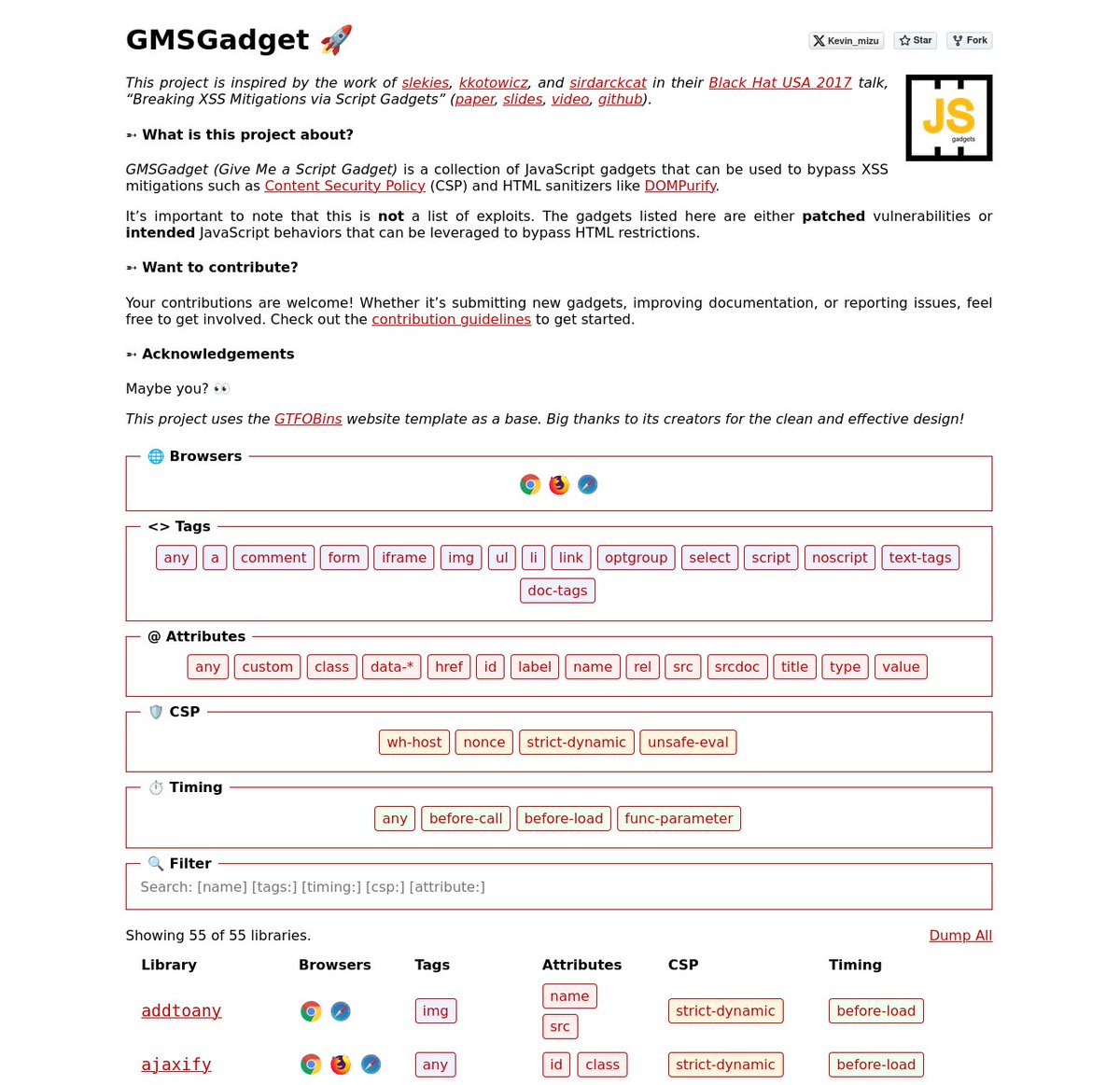
I'm happy to release a script gadgets wiki inspired by the work of Sebastian Lekies, koto, and Eduardo Vela in their Black Hat USA 2017 talk! 🔥 The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇 gmsgadget.com 1/4