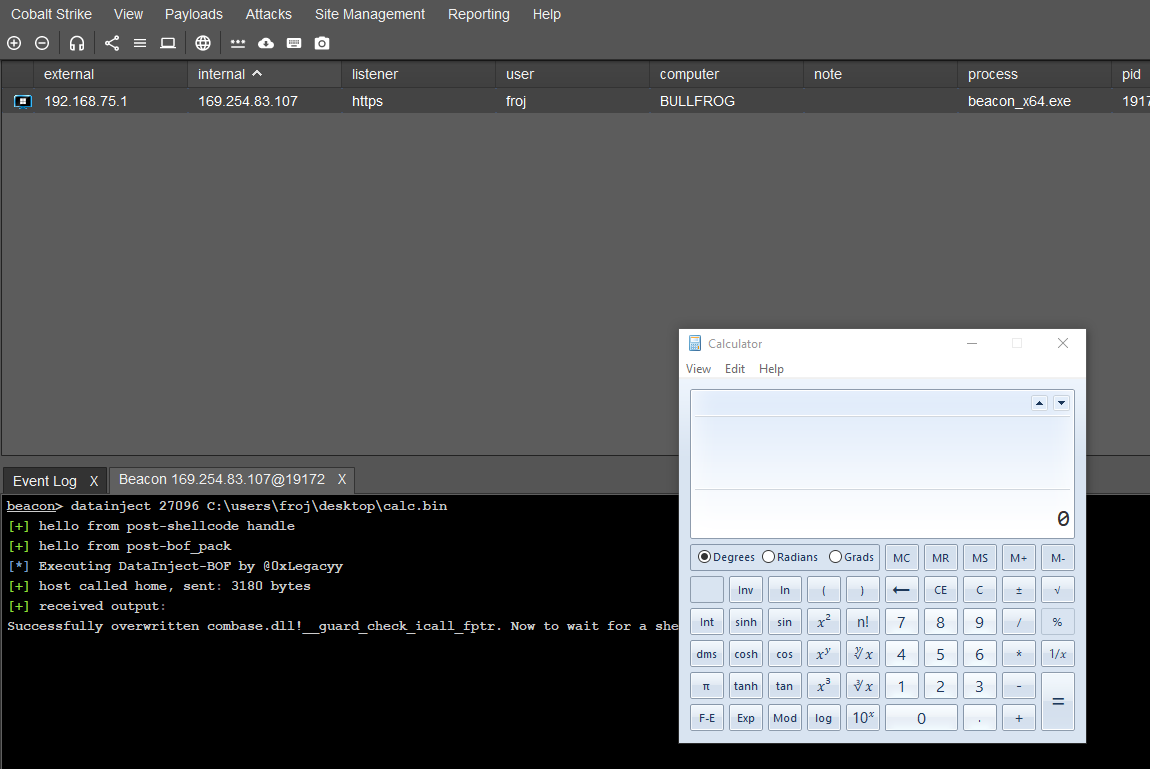
sinusoid
@the_bit_diddler
ID: 757648339630522368
25-07-2016 18:46:55
2,2K Tweet
1,1K Followers
1,1K Following


We're super stoked to publish this post. A huge shoutout to our former intern, rainbowpigeon who poured his heart & soul into this 7-8 months ago. It took us a bit to polish it up but we're incredibly proud of him. Dive in & let us know what you think! starlabs.sg/blog/2025/12-m…


While looking at the cesspit of online discourse, Connor McGarr is always a beacon of hope.

Found a .NET method on SCCM site servers that can be called to decrypt secrets stored in the site DB a while back with Garrett and Lee Chagolla-Christensen. Another alternative to 🥝🏳️🌈 Benjamin Delpy's mimikatz misc::sccm, Adam Chester 🏴☠️'s C# gist, and Sanjiv Kawa's SQLRecon. github.com/subat0mik/Misc…