
Niraj Mahajan
@niraj1mahajan
Microsoft 2024 MVR | #BugBounty Hunter | Application Security | Discovered 11x CVEs
ID: 162688452
https://www.linkedin.com/in/niraj1mahajan/ 04-07-2010 11:54:32
498 Tweet
1,1K Followers
656 Following




Sathwik Ram Prakki (Sathwik Ram Prakki), Senior Security Researcher at (SEQRITE) / (Quick Heal) discussed how APT group SideCopy (linked to APT36) is evolving its tactics across platforms at BlueHat india. His talk revealed a shift from HTA-based attacks to MSI stagers, targeting




Had an incredible time attending the MSRC BlueHat event at Microsoft — learning, connecting, and diving deep into security! Microsoft Security Response Center


Day 1 of #BlueHatIndia was absolutely electrifying with Tom Gallagher opening remarks David Weston (DWIZZZLE) keynote & insightful sessions🙌Best part? Connecting with Security Response fellow researchers & security pros 🫶Excited for Day 2-let’s meet up and make it awesome! Ashish Dhone


Honored to attend BlueHat India 2025 as a Microsoft Most Valuable Researcher (MVR) An inspiring journey, proud moment, and unforgettable experience. Microsoft BlueHat Security Response Microsoft Security


Day 1 of BlueHat India brought together a passionate, global community of security professionals, from seasoned defenders to up-and-coming researchers, who came to learn, share, and connect. We kicked off with keynotes from Tom Gallagher (Tom Gallagher) and David "DWIZZZLE"


At BlueHat India Day 2, Ram Shankar Siva Kumar (Ram Shankar Siva Kumar), Microsoft’s resident Data Cowboy and Head of the AI Red Team, took the stage for a keynote that was equal parts eye-opening and unsettling. Ram unpacked what happens when adversarial machine learning meets generative AI.



Missed BlueHat India 2025? Catch up now! Talks from Microsoft & global security experts are live on the Security Response YouTube channel: youtube.com/@msftsecrespon… From AI threats to ransomware ops, mobile red teaming and more, don’t miss these deep-dive sessions. #BlueHatIndia


✨ Honoured to be recognised as a Microsoft Most Valuable Researcher (MVR) for 2025! A heartfelt thank you to the Microsoft Security Response Center for this recognition and for their continued support in fostering a vibrant security research community.


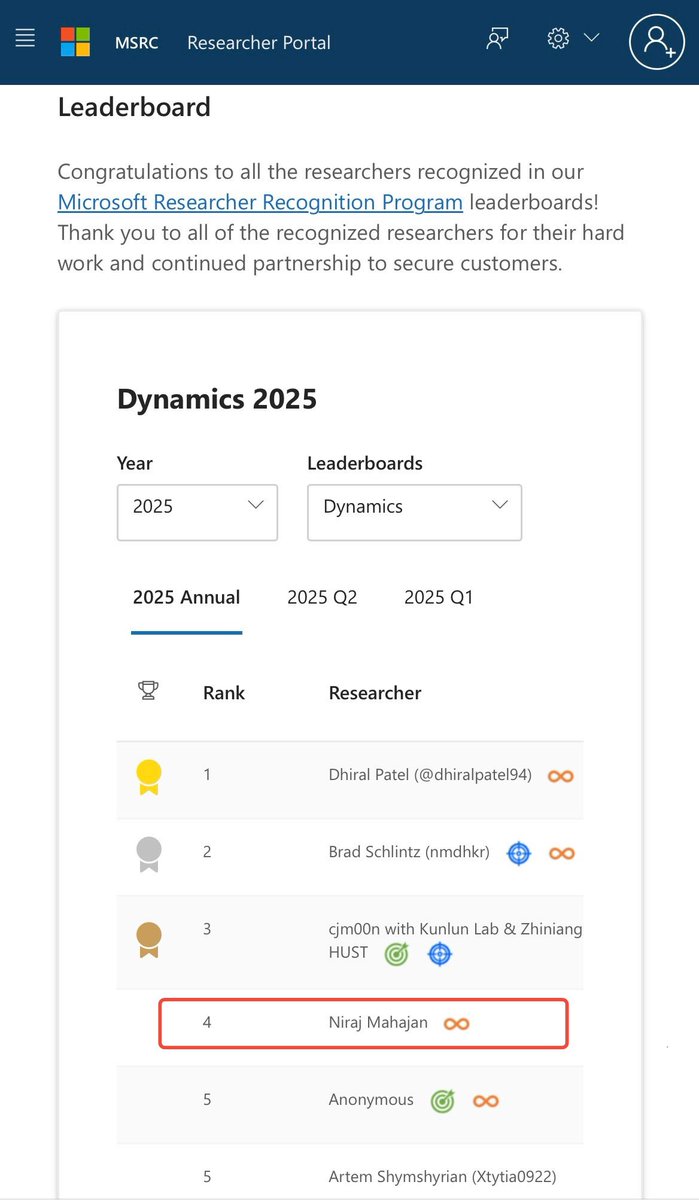
Proud to have secured a spot in the Top 5 for Microsoft Dynamics! ❤️ Microsoft Security Response Center

The MSRC team and I are excited up to connect and learn from security researchers and the community at Black Hat & DEF CON this week! If you spot me, I might have a shirt with your name on it. #blackhat2025 #blackhat #defcon Microsoft Security Response Center







