
MalwareTips
@malwaretipscom
Cybersecurity community (est. 2009) offering free malware removal guides, tech news, scam alerts, help forums, & security resources.
ID: 224593013
https://malwaretips.com/ 09-12-2010 11:21:51
5,5K Tweet
5,5K Followers
271 Following

🚨BREAKING: U.S. Government takes down China-linked botnet!Volt Typhoon targeted vulnerable routers in a major hacking campaign. The FBI remotely dismantled the KV-botnet, disrupting covert data transfer networks. Stay vigilant and follow Cybersecurity and Infrastructure Security Agency guidance for device security!




Avast releases free decryptor for DoNex ransomware and past variants - Bill Toulas bleepingcomputer.com/news/security/… bleepingcomputer.com/news/security/…


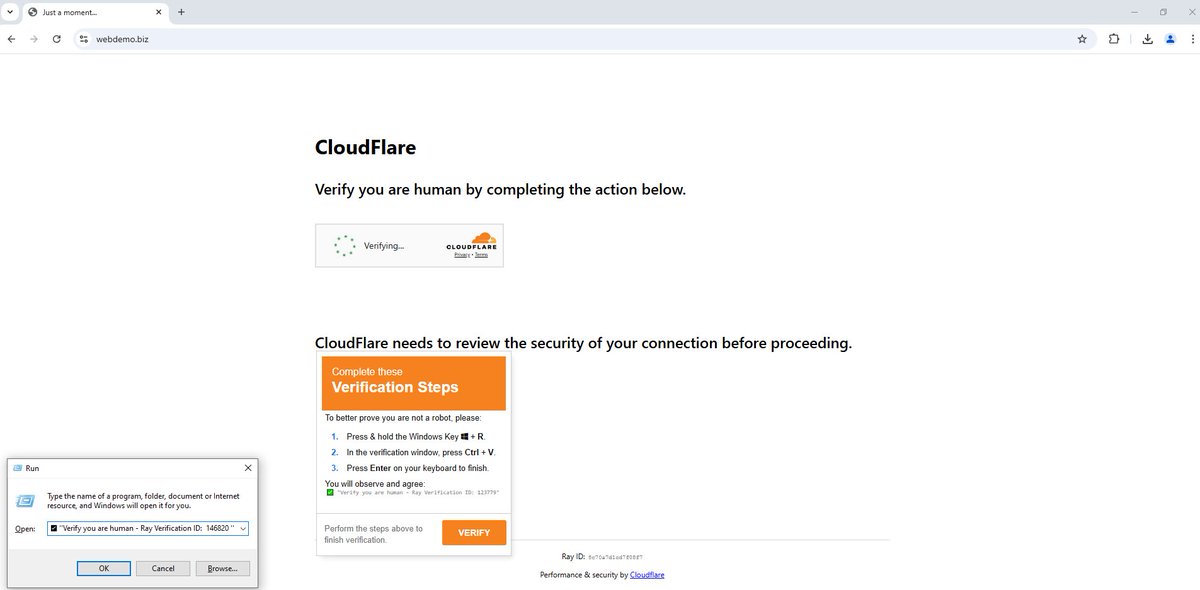
🚨 Interesting #FakeCaptcha technique alert! Attackers are using mshta commands formatted to show only harmless text like 'Verify you are human' in the Windows Run Dialog, hiding the malicious part. They also extended their #impersonation portfolio with Cloudflare CAPTCHA



SquareX is here to put a stop to that—providing real-time protection to keep your data and privacy secure. Read the ongoing discussion at: malwaretips.com/threads/google… (MalwareTips)




