Jaresbell
@jaresbell
Software Engineer at Google | Offensive Security Researcher | Curious | Hobbyist Commodore 64 game dev | Opinions are my own.
ID: 28657846
03-04-2009 21:29:12
123 Tweet
28 Followers
296 Following






It is well past time for laws that require all mission-critical software to have publicly published source code. Flying planes, driving cars, and using voting machines whose software hasn't been publicly analyzed is a dangerous (and deadly) policy choice. bloomberg.com/news/articles/…




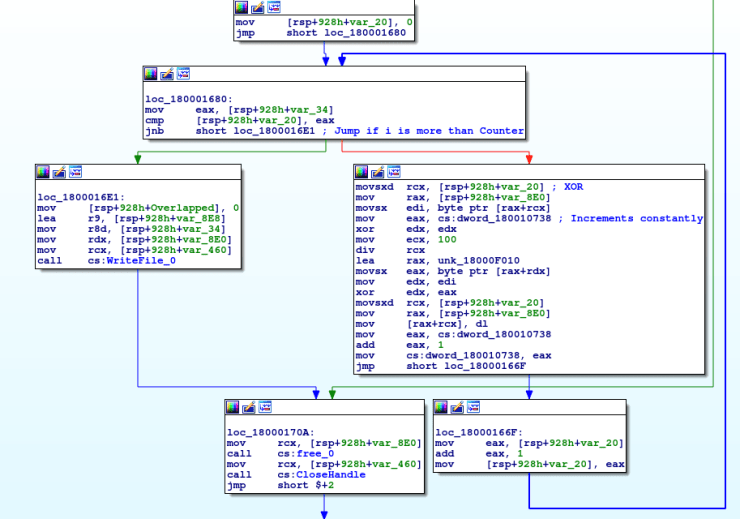
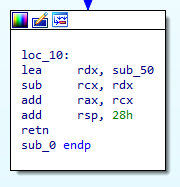
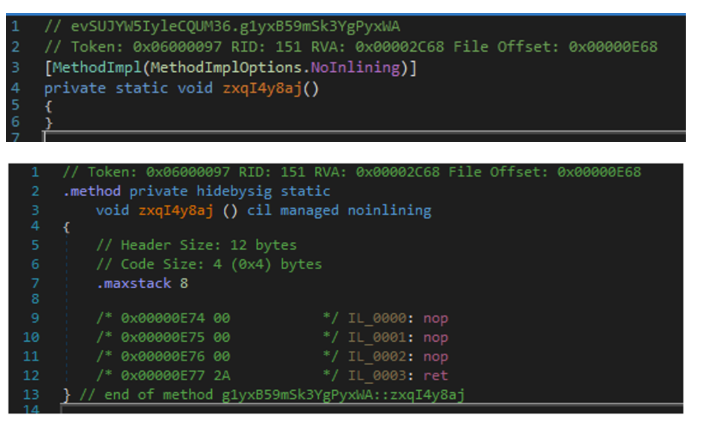
Reversing a real-world 249 bytes backdoor! : anee.me/reversing-a-re… cc Aneesh Dogra








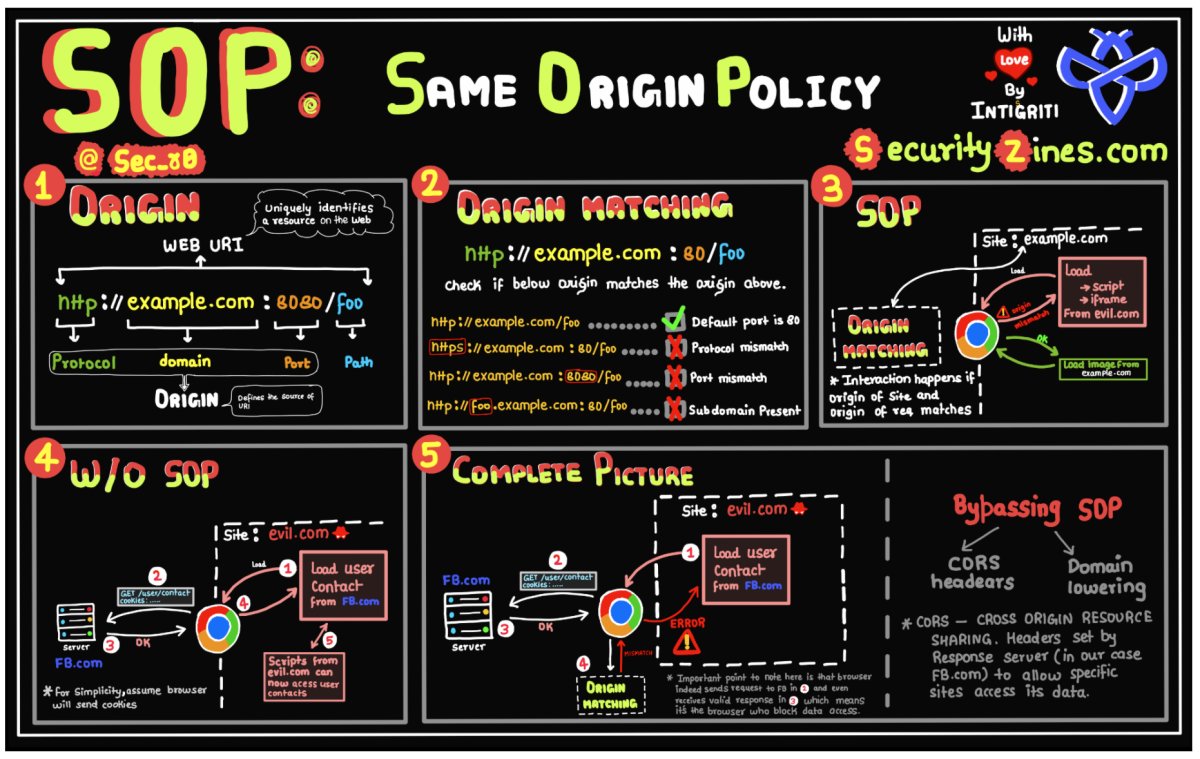
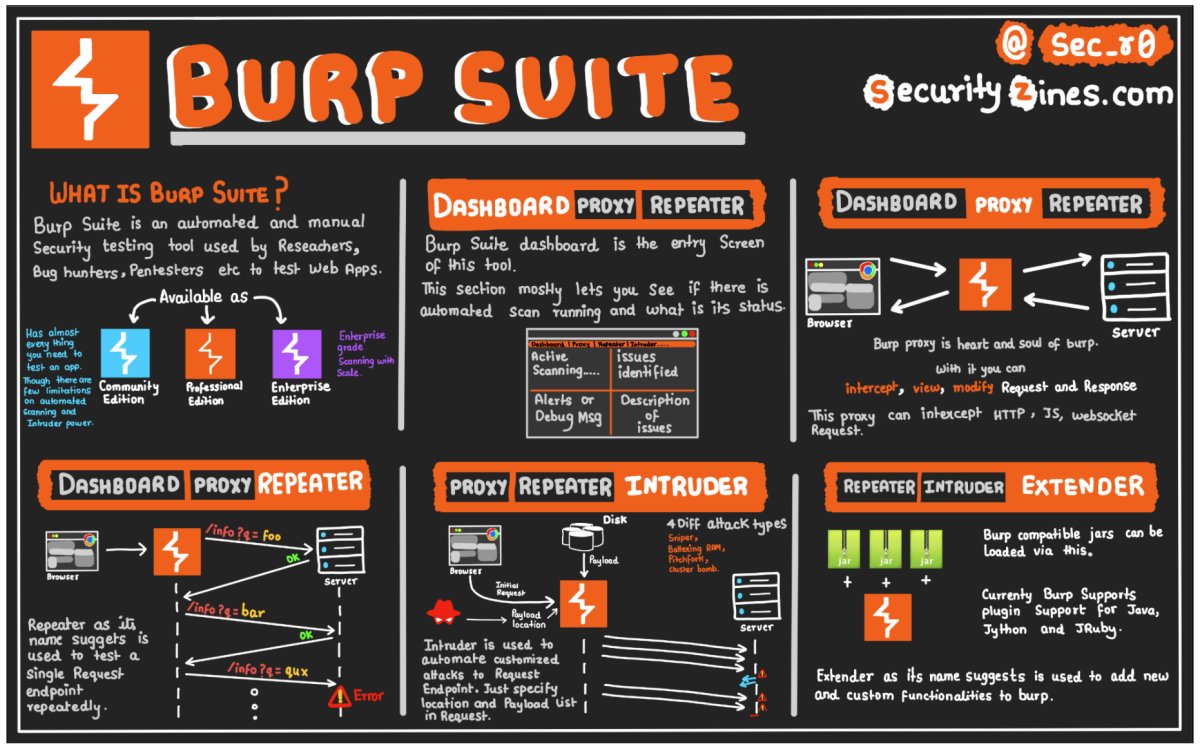
Learn WebAppSec With Fun - Part 3 In frame: - Stored XSS - Burp Suite Please RT for reach. More @http://securityzines.com #infosec #cybersecurity #pentesting #ctf #oscp #windows #cheatsheet #redteaming #burpsuite #bugbounty #bugbountytips #zines #security


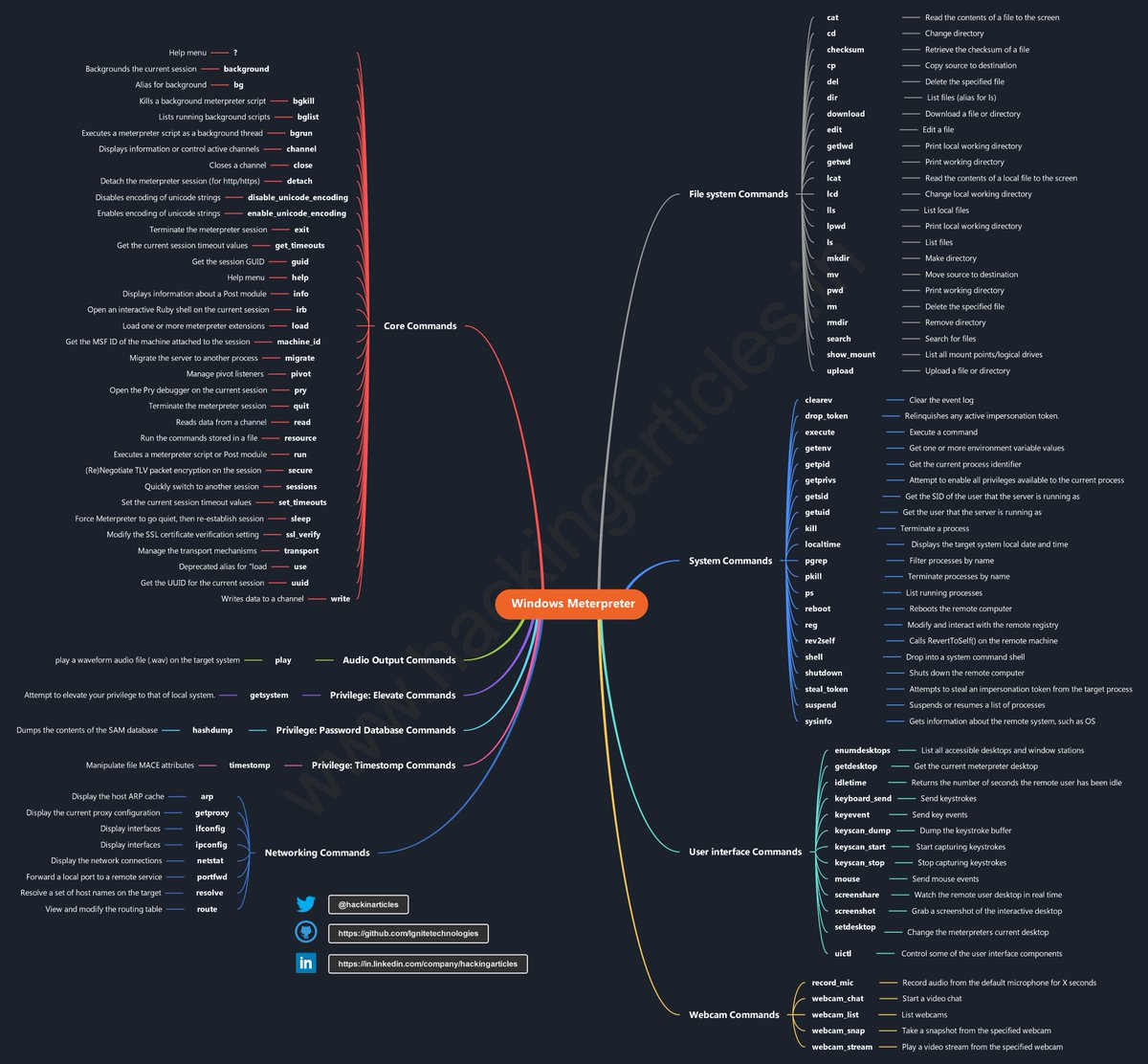
Mindmap : This repository contains many mindmaps for cyber security technologies, methodologies, courses, and certifications in a tree structure to give brief details about them : github.com/Ignitetechnolo… credits Hacking Articles