Russ McRee
@holisticinfosec
Director, GCP Cyber Defense Center, @Google, former @MSFT MSRC, PhD, GSE, dissertation chair @captechu, @SANS_ISC handler, music via @russmcree
ID: 44394901
https://holisticinfosec.io 03-06-2009 16:33:18
3,3K Tweet
4,4K Followers
229 Following




I teach my teams this simple mantra: measurability == survivability. “Use specific, quantifiable metrics to showcase improvements in security posture and ops efficiency.” Reductions in vulnerability remediation time, decreases in IR costs, and latency too. helpnetsecurity.com/2024/07/24/kar…


Looking forward to seeing folks tomorrow at our BTV panel in LVCC W3 10 from 3-4p. With over 80 years of SOC experience, we cut the buzzword bingo & get real. We’ll be discussing topics like how to get value with threat intel beyond IOC matching, and more! cfc.blueteamvillage.org/dc32/talk/XR7H…
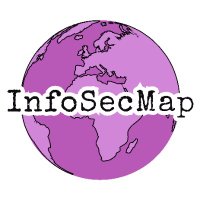
The Blue Team Village at #DEFCON32 had lots of defender-focused activities, and the best pool party! 💙 🛡️ Shoutout to Ray [REDACTED], Nicole Beckwith, Dr. Ch33r10, Ryan "Chaps" Chapman, @JamieAntiSocial, @HolisticInfoSec, @BenGoerz and [email protected]. More @DEFCON villages 👇🏽 infosecmap.com/listing/def-co…
![InfoSecMap (@infosecmap) on Twitter photo The <a href="/BlueTeamVillage/">Blue Team Village</a> at #DEFCON32 had lots of defender-focused activities, and the best pool party! 💙 🛡️
Shoutout to <a href="/RayRedacted/">Ray [REDACTED]</a>, <a href="/NicoleBeckwith/">Nicole Beckwith</a>, <a href="/Ch33r10/">Dr. Ch33r10</a>, <a href="/rj_chap/">Ryan "Chaps" Chapman</a>, @JamieAntiSocial, @HolisticInfoSec, @BenGoerz and <a href="/rpargman/">randy@infosec.exchange</a>.
More @DEFCON villages 👇🏽
infosecmap.com/listing/def-co… The <a href="/BlueTeamVillage/">Blue Team Village</a> at #DEFCON32 had lots of defender-focused activities, and the best pool party! 💙 🛡️
Shoutout to <a href="/RayRedacted/">Ray [REDACTED]</a>, <a href="/NicoleBeckwith/">Nicole Beckwith</a>, <a href="/Ch33r10/">Dr. Ch33r10</a>, <a href="/rj_chap/">Ryan "Chaps" Chapman</a>, @JamieAntiSocial, @HolisticInfoSec, @BenGoerz and <a href="/rpargman/">randy@infosec.exchange</a>.
More @DEFCON villages 👇🏽
infosecmap.com/listing/def-co…](https://pbs.twimg.com/media/GWAW9aoaoAIWHaL.jpg)

Google's Cloud Vulnerability Research team (CVR) presents vulnerabilities in the 3rd party image library Kakadu, outlining challenges external attackers face exploiting vulnerabilities in unknown environments. Simon Scannell Anthony Weems Ezequiel Pereira bughunters.google.com/blog/622075742…


At Google, we continually evolve security capabilities & practices to make our cloud the most trusted cloud. To help protect from stolen creds, cookie theft & accidental creds loss, announcing general availability of cert-based access in our IAM portfolio. cloud.google.com/blog/products/…

While working with Project Zero, #NickGalloway found an integer overflow in the dav1d AV1 video decoder. He received questions about issue discovery as dav1d is already being fuzzed by oss-fuzz. This is a useful case study in constructing fuzzers 4 effect googleprojectzero.blogspot.com/2024/10/effect…

Our CVR team performed vuln research on GCP’s AI Platform, Vertex AI & considered potential attack scenarios across Google & industry. They discovered unknown vulns that not remediated potentially could have allowed exfil of Gemini 1.0 Pro model Anthony Weems bughunters.google.com/blog/567986357…

While cloud providers can support customers in restoring access to their environments or activate backups, cloud providers generally lack the visibility & access to customer environments needed to perform customer incident response & remediation at scale. cloud.google.com/blog/products/…

Announcing the launch of Google Cloud Vulnerability Reward Program (VRP), dedicated to products & services that are part of Google Cloud. GC VRP focuses on coordinating new vulnerabilities and compensating security researchers. Top award: $101,010. cloud.google.com/blog/products/…


Big Sleep LLM agent found an exploitable stack buffer underflow in SQLite, the database engine. This is believed to be the first public example of an AI agent finding a previously unknown exploitable memory-safety issue in widely used real-world software. googleprojectzero.blogspot.com/2024/10/from-n…


As part of our continued commitment to security & transparency on vulnerabilities found in our products & services, effective today we will be issuing CVEs for critical Google Cloud vulnerabilities, even when we do not require customer action or patching. cloud.google.com/blog/products/…