Isaiah
@hacker_ise
Web & Mobile Security Reseacher | Exploring Blockchain and Cloud Security | ARM | Chasing My Curiousity
ID: 1876946412773982209
08-01-2025 10:58:05
0 Tweet
0 Followers
106 Following




The detailed version of our #WorstFit attack is available now! 🔥 Check it out! 👉 blog.orange.tw/posts/2025-01-… cc: splitline 👁️🐈⬛



Guillermo Rauch Timely guide on how to migrate from Vercel to Cloudflare: x.com/osintly/status…







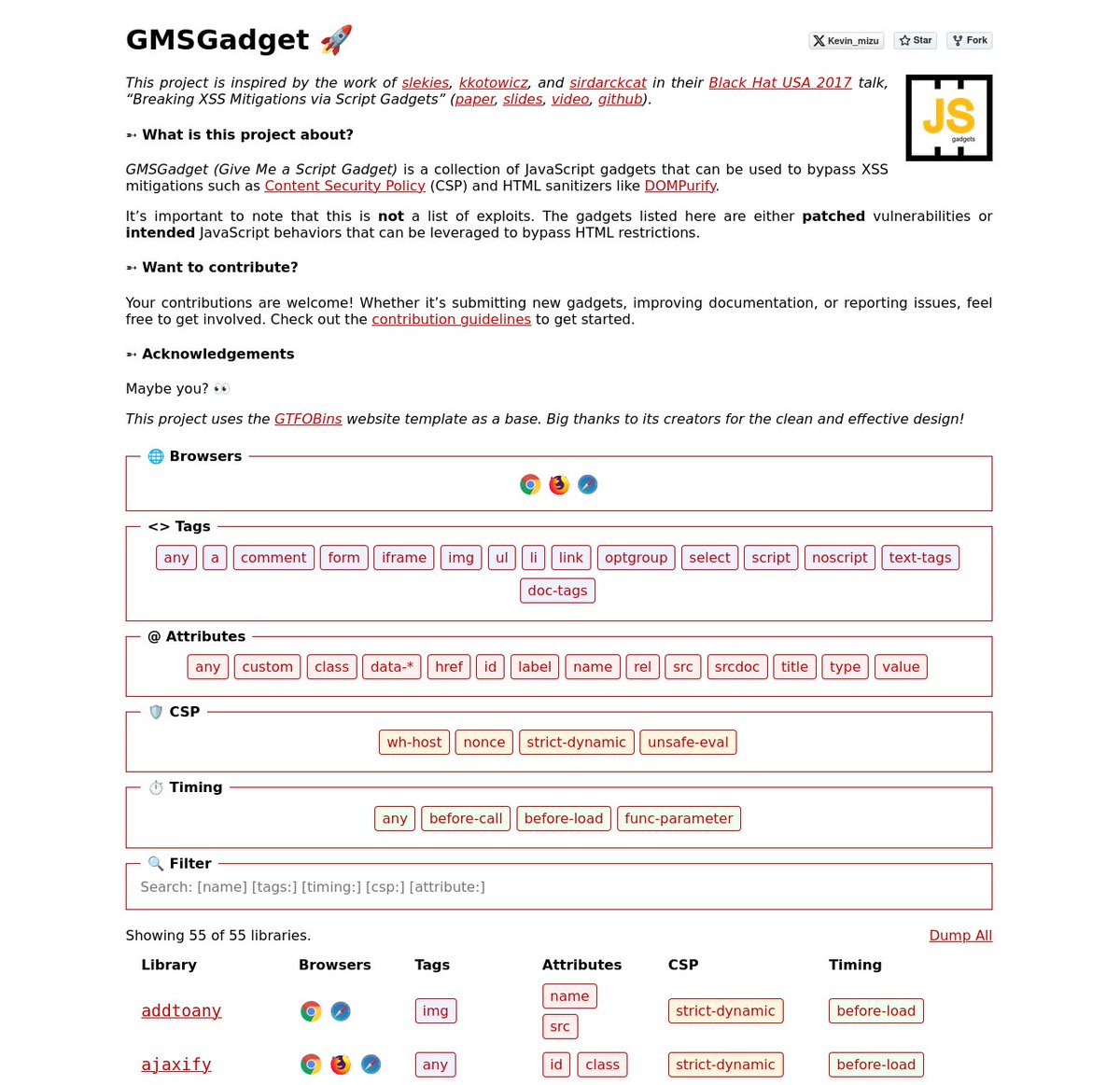
I'm happy to release a script gadgets wiki inspired by the work of Sebastian Lekies, koto, and Eduardo Vela in their Black Hat USA 2017 talk! 🔥 The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇 gmsgadget.com 1/4