匚ㄚ乃乇尺ㄖᐯ乇尺ㄥㄖ卂ᗪ
@cyber0verload
Cyber Threat Hunter
ID: 1334214654172737537
02-12-2020 19:16:50
641 Tweet
1,1K Followers
118 Following



















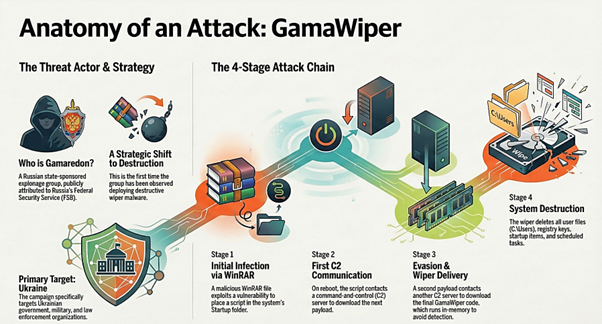
#ESETresearch analyzed the #Gamaredon VBScript payload recently flagged by ClearSky Cyber Security. It wipes registry Run keys, scheduled tasks, and kills processes – however, our assessment is that this is likely to clean researchers’ machines, not a shift to destructive ops.