estrellas
@cryptderivekey
Reverse engineer mostly interested in SAT/SMT solvers, Program Analysis and Obfuscation
Views are my own.
ID: 1235173277477281792
https://estr3llas.github.io/ 04-03-2020 12:00:40
529 Tweet
255 Followers
769 Following



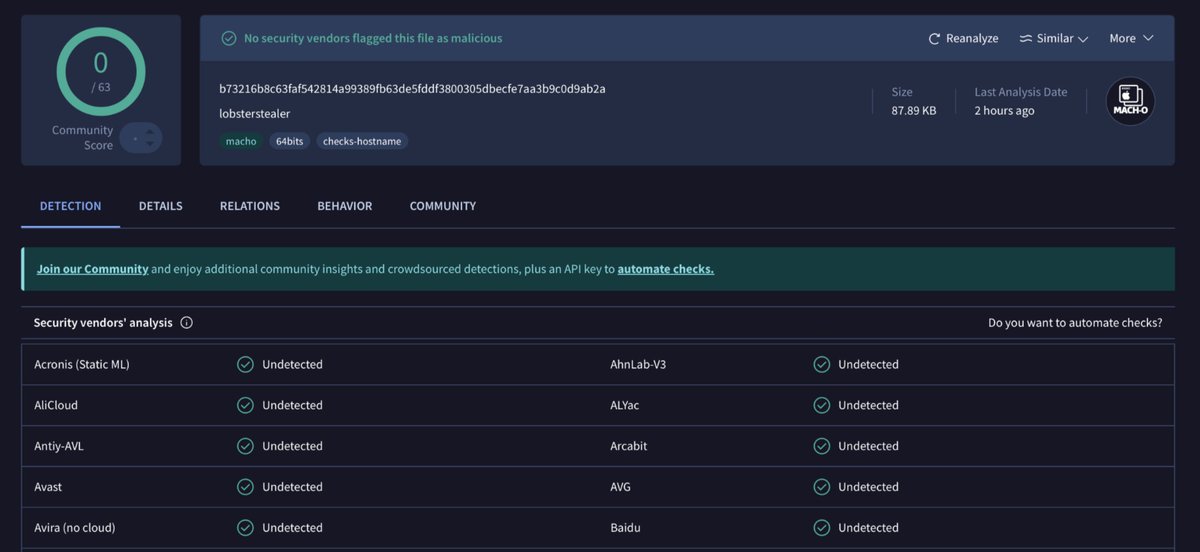
1/8: Did someone just add #CTF code to the #AMOS stealer?.. After analysis of a yet undetected ‘lobsterstealer’ sample discovered by Yogesh Londhe, we found a few noticeable things that differentiate it from regular filegrabbers we’ve seen before.