Comodo News
@comodonews
Read about news from the Comodo organization here
ID: 2938305509
http://www.comodo.com 23-12-2014 13:54:35
2,2K Tweet
2,2K Followers
3,3K Following















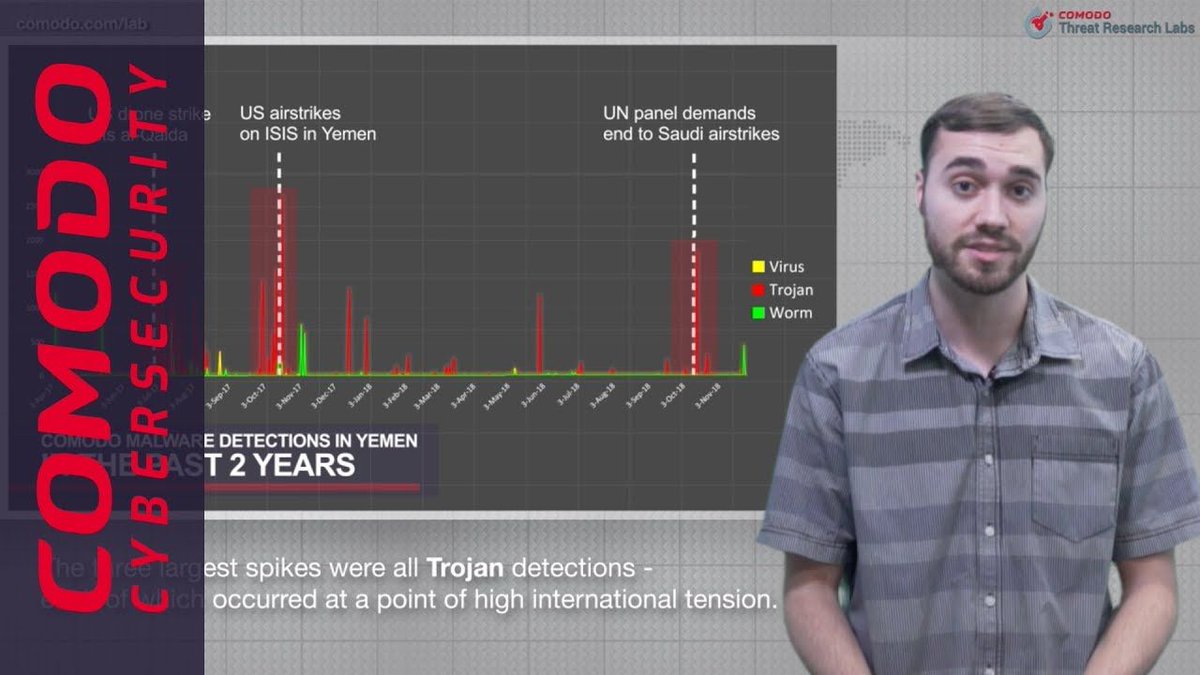
The Comodo Cybersecurity Global Threat Report offers unmatched insight into today’s evolving threat landscape. We just released our Q3 2018 Edition! Check it out to find out the latest trends and threats in cybersecurity! Comodo Threat Research Labs buff.ly/2ROhiQm