
Takahiro Haruyama
@cci_forensics
唇亡歯寒
ID: 126881953
https://speakerdeck.com/takahiro_haruyama 27-03-2010 08:35:13
4,4K Tweet
2,2K Followers
158 Following



🔎From Hidden Semantics to Structured Insights✨ By combining static analysis techniques and tailored heuristic improvements, we've significantly enhanced the precision of type inference, enabling more effective vulnerability triage. lukas seidel Sam Thomas 👏 binarly.io/blog/type-infe…


My #idalib based tools are featured in the latest Hex-Rays SA blog! hex-rays.com/blog/4-powerfu…

Nvidia OSR (Alex Tereshkin, Adam 'pi3' Zabrocki) reveals high-impact Supermicro BMC vulnerabilities (CVE-2024-10237/38/39). Binarly REsearch documenting the details: 👻Ghost in the Controller: Abusing Supermicro BMC Firmware Verification. Read the full story: binarly.io/blog/ghost-in-…








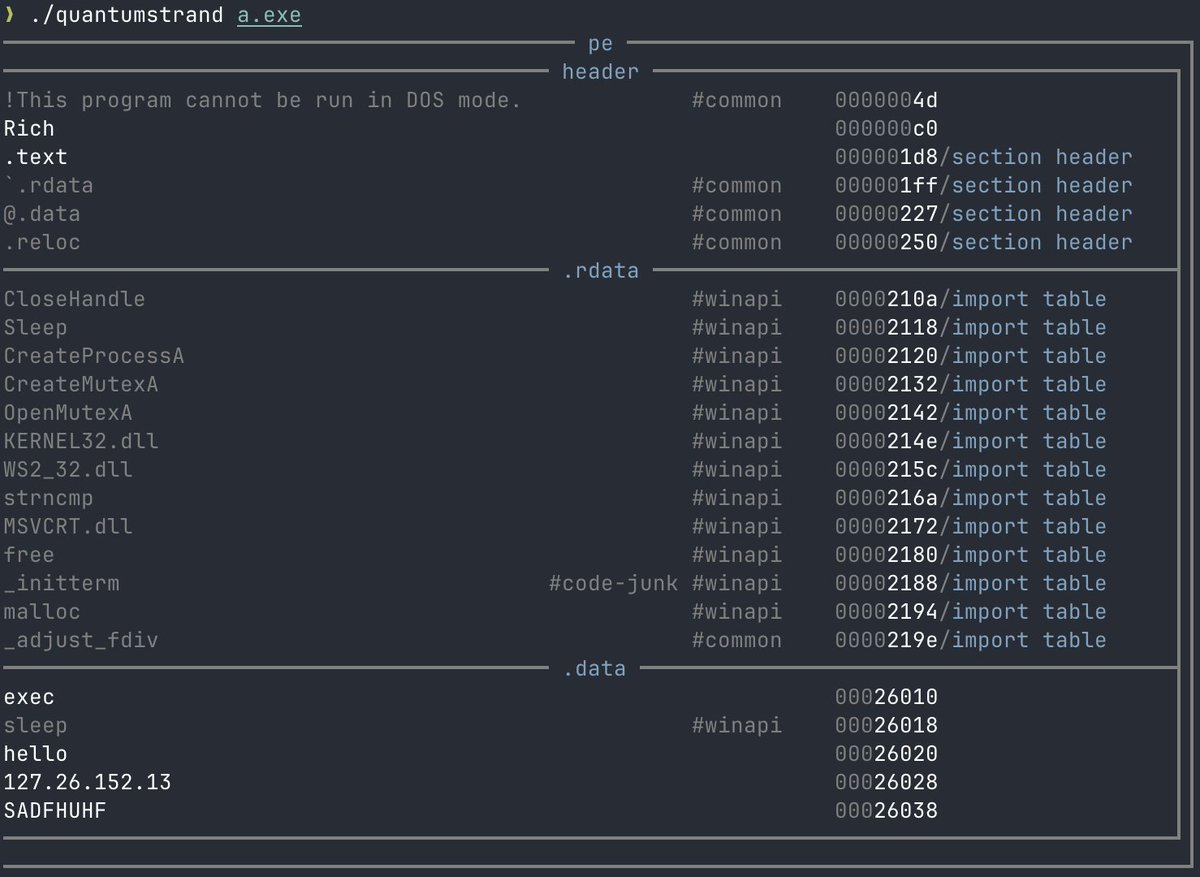
QUANTUMSTRAND beta 1 released: built for analysts to quickly understand *where* strings are, *what* they might be, and *how* important they are, without getting lost in a sea of undifferentiated text. Thanks Moritz and the crew at Mandiant (part of Google Cloud) FLARE github.com/mandiant/flare…



#ESETresearch has discovered #HybridPetya ransomware on VirusTotal: a UEFI-compatible copycat of the infamous Petya/NotPetya malware. HybridPetya is capable of bypassing UEFI Secure Boot on outdated systems. Martin Smolar welivesecurity.com/en/eset-resear… 1/8









