
Thomas Seigneuret
@_zblurx
Red Teamer & Security researcher
Maintainer of #NetExec, #DonPAPI, dploot, certsync, and all the stuff on my github repo
bsky: zblurx.bsky.social
ID: 1230105801278267397
https://github.com/zblurx 19-02-2020 12:24:19
358 Tweet
2,2K Followers
382 Following

I am very excited to be releasing Tetanus, a Mythic C2 agent written in Rust! This is a project Max Harley have been working on to experiment with the Rust programming language by developing a Mythic C2 agent. github.com/MythicAgents/t…



Impersonate another user by moving their Kerberos tickets into your logon session with lsa-whisperer by Evan McBroom. You can even move them back after you are done. Only your session will loose its tickets.







Okay so this is HUGE - our amazing AI red team have open sourced their AI red team labs so you can set up your own training! aka.ms/AIRTlabs Ram Shankar Siva Kumar


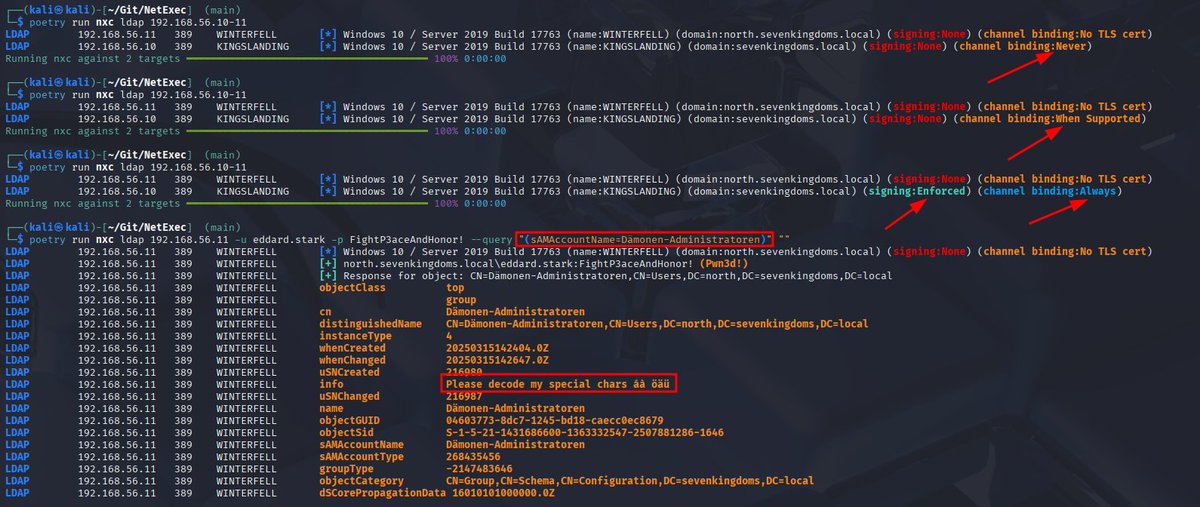
NetExec now has native checks for LDAP signing and channel binding capabilities of the target DC, thanks to the implementation of Thomas Seigneuret 🚀 I also fixed querying LDAP with non-ASCII characters, so you can finally query groups such as "Dämonen-Administratoren"🎉




🚨 Our new blog post about Windows CVE-2025-33073 which we discovered is live: 🪞 The Reflective Kerberos Relay Attack - Remote privilege escalation from low-priv user to SYSTEM with RCE by applying a long forgotten NTLM relay technique to Kerberos: blog.redteam-pentesting.de/2025/reflectiv…









