Daniel Graciá
@danigraciaitpro
IT Consultant Freelance,VCP6.7,MCSE Cloud,MCSA 2016,Nutanix NPP, ESAE, CompTIA Cloud+, Azure Architect, lector empedernido. Winter is coming.Fuerza y honor! :-)
ID: 866785759
http://blogs.itpro.es/danielgracia/ 07-10-2012 18:52:19
5,5K Tweet
521 Takipçi
1,1K Takip Edilen




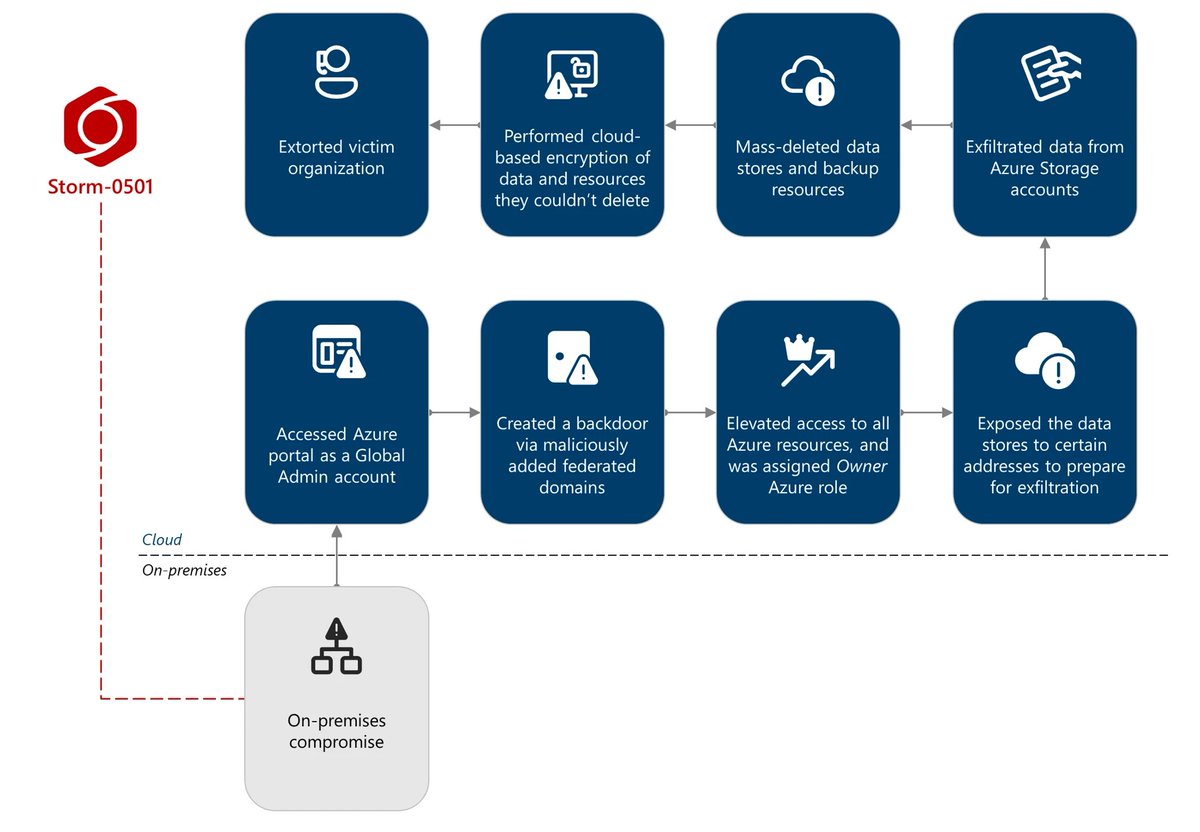
Highly recommend everyone read the latest Microsoft Threat Intelligence blog, especially if you are involved in identity or cloud security. It details how threat actors can pivot between both your on-premises and cloud identity planes and cause destruction across both. Without proper guardrails







Group Policy Security Filtering: Fine-Tune How GPOs Are Applied Michael Reinders petri.com/group-policy-s… #ActiveDirectory